What Are Threat Intelligence Tools?
Threat intelligence tools are software applications and platforms designed to gather, analyze, and disseminate information about cybersecurity threats, enabling organizations to proactively identify, assess, and respond to potential risks. These tools help security teams understand the threat landscape, prioritize threats, and improve their overall security posture.
Key functions of threat intelligence tools include:
- Data collection: These tools collect data from various sources, including open-source intelligence (OSINT), malware databases, dark web forums, and internal security logs.
- Analysis and correlation: Threat intelligence tools analyze the collected data, correlate it with known security threats, and identify potential vulnerabilities, attack patterns, and threat actors.
- Threat prioritization: By analyzing the potential impact and severity of threats, these tools help security teams prioritize which threats to address first.
- Actionable insights: Threat intelligence tools provide actionable insights, such as indicators of compromise (IoCs), threat actor profiles, and recommended mitigation strategies, enabling security teams to take appropriate action.
- Integration with security systems: Many threat intelligence tools integrate with other security systems, such as SIEMs, firewalls, and endpoint protection platforms, to automate threat detection and response.
We’ll discuss these features in more detail below.
Benefits of Using Threat Intelligence Tools
Incorporating actionable threat intelligence into a cybersecurity strategy offers several key advantages. These tools not only improve the detection and response capabilities but also contribute to a more proactive and efficient security posture. Here are the primary benefits:
- Improved threat detection: Threat intelligence tools enable organizations to detect threats earlier and more effectively.
- Reduced response time: By providing timely and actionable insights, these tools help security teams respond to security threats faster.
- Cost savings: By preventing attacks and reducing incident response time, threat intelligence tools can help organizations save money.
- Better risk management: Threat intelligence tools enable organizations to assess the risk posed by threats, allowing for targeted security investments and better resource allocation.
- Increased threat awareness: With detailed insights into attack trends, adversary tactics, and known vulnerabilities, security teams are more informed about the risks they face, improving overall preparedness.
- Reduced alert fatigue: By filtering and prioritizing the most critical threats, threat intelligence tools help security teams focus on what matters most, minimizing distractions from false positives and reducing burnout.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

Key Features of Modern Cyber Threat Intelligence
Data Collection
Modern threat intelligence tools excel at collecting data from a range of internal and external sources. Sources can include open-source intelligence (OSINT), commercial threat feeds, information sharing communities, dark web forums, malware analysis, and even telemetry from internal security systems. The purpose is to ensure visibility into the threat landscape, covering both commodity and targeted attacks.
The ability to aggregate and normalize diverse data sets is essential. By automatically harvesting and standardizing information, these tools make it readily accessible for analysis and integration into broader workflows. The combination of internal telemetry and external intelligence ensures security teams have the context they need to spot threats to their industry.
Analysis and Correlation
Advanced tools apply algorithms, machine learning, and heuristics to identify patterns, anomalies, and potential attack vectors within incoming threat data. By correlating indicators from multiple sources, they can uncover links between seemingly unrelated events that might indicate a coordinated attack.
As a result, security operations teams can investigate incidents with a deeper level of context, understanding how individual alerts and artifacts fit within the broader threat landscape. Effective correlation reduces the risk of missing complex attacks that use multiple stages or obfuscated techniques, allowing defenders to build a more complete attack narrative.
Threat Prioritization
Threat intelligence tools provide prioritization mechanisms to help security teams focus on the most relevant threats. These solutions assess the potential impact, exploitability, and relevance of threats based on an organization’s assets, configuration, and industry. Automated scoring and risk assessments highlight vulnerabilities and exposures that deserve immediate action.
By accurately classifying and prioritizing threats, teams can avoid alert fatigue and ensure critical issues do not get lost in the noise. Prioritization helps to optimize resource allocation in security operations, ensuring that limited analyst time and attention are spent on the events most likely to cause damage or require urgent mitigation.
Actionable Insights
A defining capability of effective threat intelligence platforms is their ability to translate complex data into actionable insights. This means presenting clear recommendations, suggested mitigations, and concise reports that security teams can directly apply to their environments. Actionability drives value, moving intelligence from static reports to decisions and playbooks.
These insights support decision-makers by providing context on potential risks, attack vectors, and adversary TTPs. When intelligence is actionable, it enables fast containment, patching, or policy adjustments. This ensures that threat intelligence data is effective in reducing risk and improving detection and response.
Integration with Security Systems
Modern threat intelligence tools are built to integrate seamlessly with existing security infrastructure. Common integrations include Security Information and Event Management (SIEM) platforms, firewalls, endpoint detection and response (EDR) solutions, and Security Orchestration Automation and Response (SOAR) tools.
By enabling direct feeds and bi-directional communication with security controls, these tools ensure that up-to-date threat data is used in real time to block, detect, and respond to threats. Integration also enables faster incident response and allows organizations to automate enforcement actions, scaling security operations without increasing workload or cost.
Notable Cyber Threat Intelligence Tools
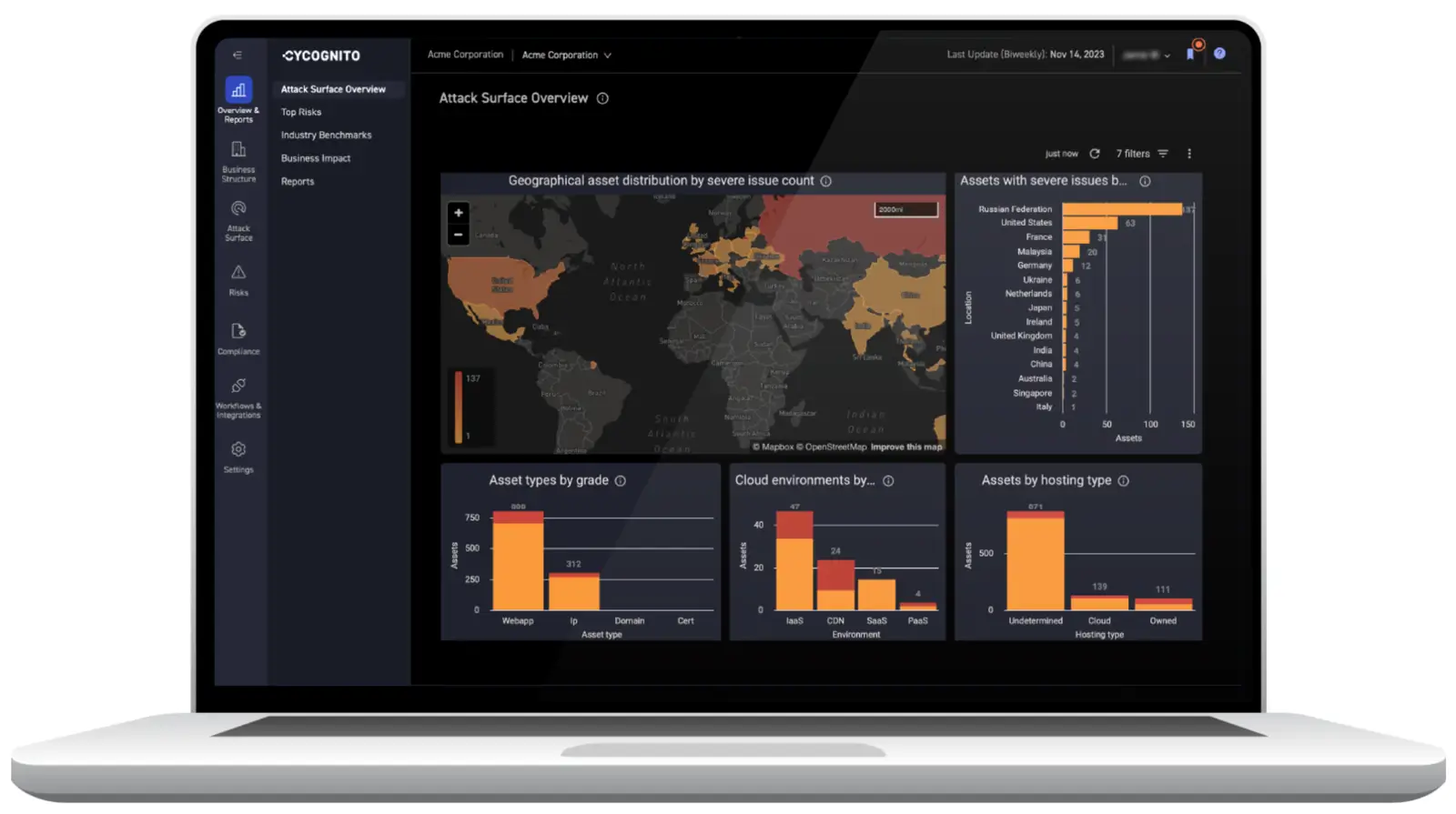
1. CyCognito

CyCognito is an exposure management platform that delivers actionable threat intelligence on external risks, vulnerabilities and potential attack paths. The platform continuously discovers and classifies externally reachable assets (incl. shadow IT, subsidiary, and third‑party infrastructure), correlates discovery, vulnerability and active testing results with broader threat context, and turns the output into prioritized remediation workflows.
Key features include:
- External discovery: Continuously maps known, unknown, shadow, subsidiary and third‑party internet‑facing assets.
- Active testing: Validates exposures (incl. DAST-style probes) to confirm exploitability and reduce false positives.
- Contextual intelligence: Enriches findings with detailed evidence, service fingerprints, configuration details and non‑CVE issues (misconfigurations, open services, expired certificates, orphaned or shadow assets).
- Risk prioritization: Scores vulnerable assets by likelihood of exploitation and potential business impact to focus effort.
- Remediation workflows: Identifies likely owners and integrates with SIEM, SOAR and ticketing systems to track closure.
2. Recorded Future

Recorded Future is a threat intelligence platform that uses AI to provide threat data. It connects internal telemetry with external sources, including the open web, dark web, and technical feeds, through an AI-driven intelligence graph.
Key features include:
- Intelligence graph: Organizes and analyzes data from sources to provide insights.
- Threat intelligence: Continuously updates threat data to ensure timely detection and response.
- Integrations: Compatible with existing security tools like SIEM, EDR, and SOAR platforms.
- Threat prioritization: Helps security teams focus on critical threats by scoring and assessing risks.
- Vulnerability intelligence: Identifies and provides insights into critical vulnerabilities to mitigate potential attacks.
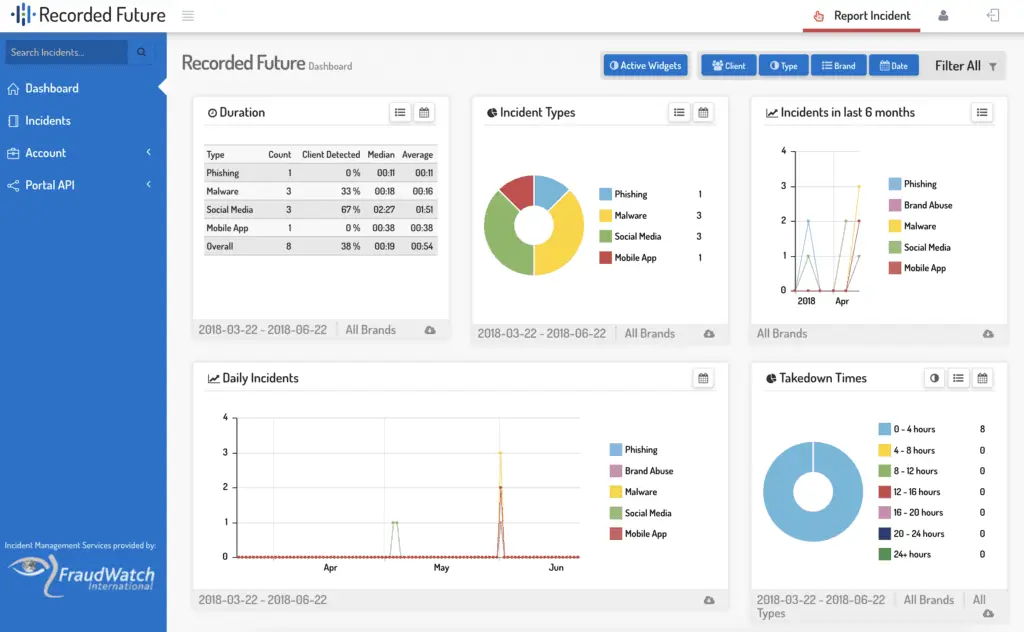
Source: Recorded Future
3. Anomali

Anomali is an AI-powered security and IT operations platform intended to modernize threat detection and response. It integrates security tools, including SIEM, XDR, UEBA, SOAR, and threat intelligence capabilities, into a unified solution.
Key features include:
- AI Copilot: Automates critical tasks, simplifying workflows.
- Data lake integration: Consolidates and accelerates data from legacy tools, providing analysis and visibility.
- Threat response: Enables lookback searches on petabytes of data to provide immediate results.
- Low-cost high-performance: Retains 7 years of critical data in hot storage at a lower cost than competitors.
- Generative AI: Uses AI to identify, correlate, and remediate threats while reducing errors or hallucinations in the analysis.
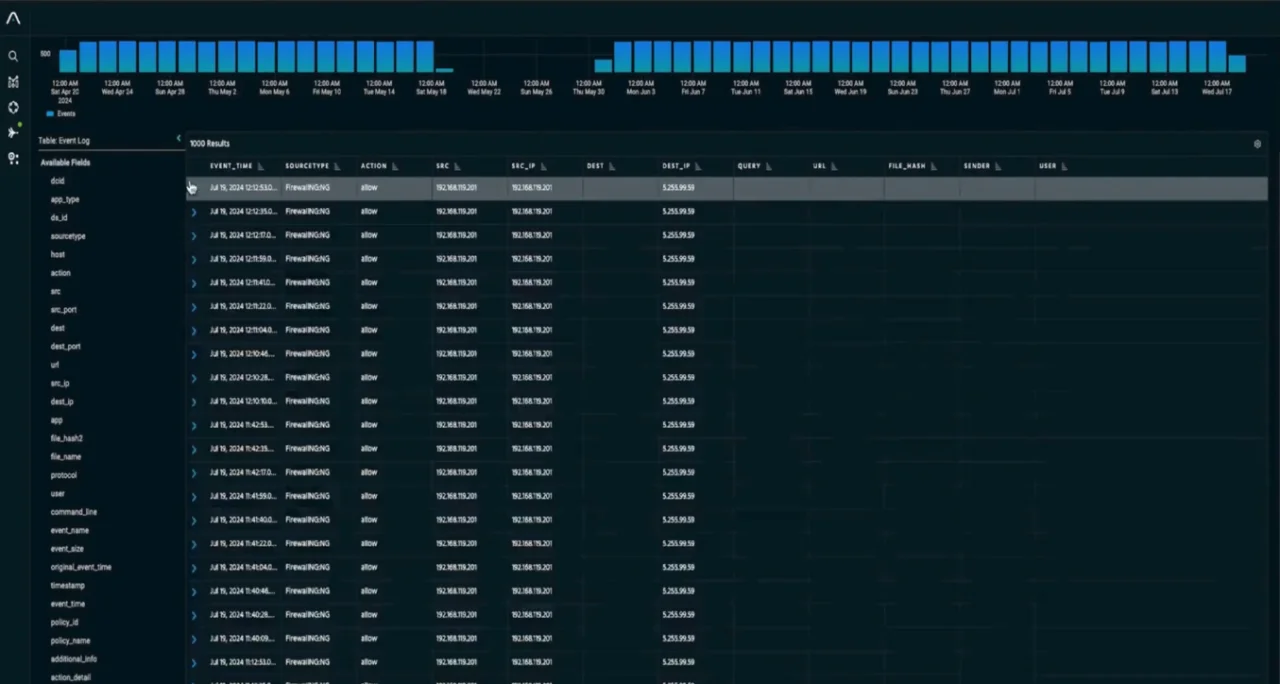
Source: Anomali
4. Cyble Vision

Cyble Vision is an AI-powered cybersecurity platform to provide digital risk protection through continuous monitoring and proactive defense. It combines AI features that span across multiple cybersecurity domains, including cyber threat intelligence, dark web monitoring, vulnerability management, and third-party risk management.
- Cyber threat intelligence: AI-driven analysis and continuous monitoring to provide insights into emerging cyber threats.
- Dark web and cybercrime monitoring: Tracks dark web activities to protect sensitive information from exploitation and online abuse.
- Attack surface management: Identifies and mitigates threats across the attack surface.
- Vulnerability management: Provides scanning and risk evaluation.
- Brand intelligence: Protects brands from online abuse, phishing, impersonation, and fraudulent domains to maintain brand integrity.
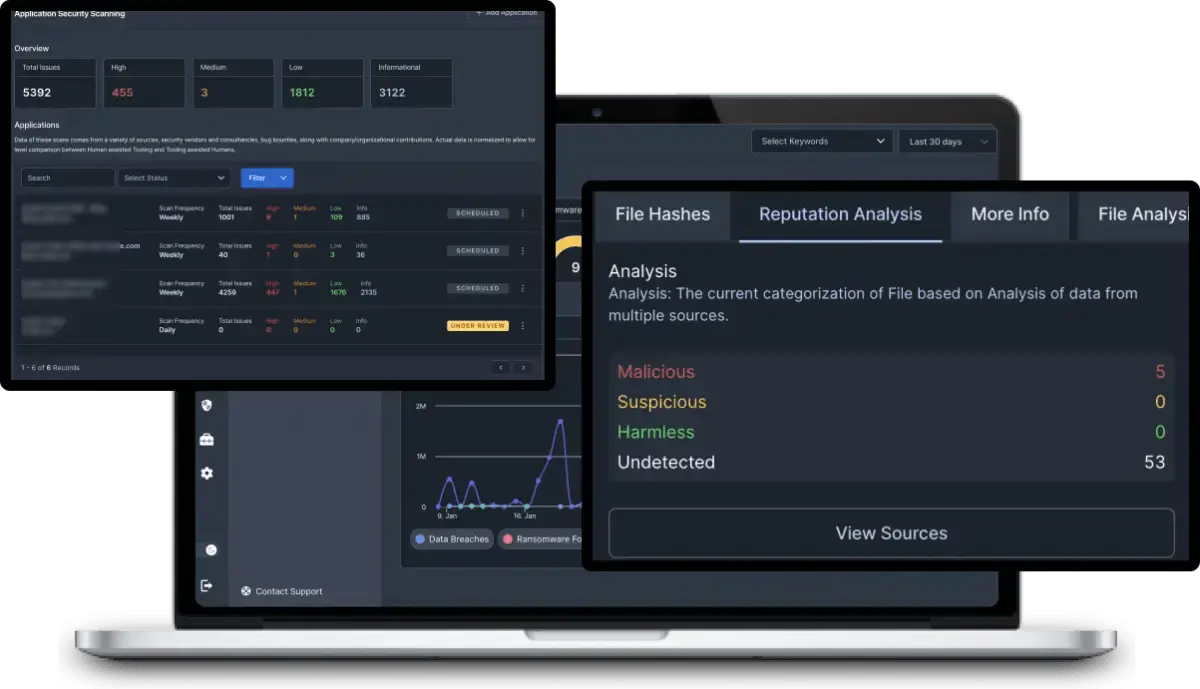
Source: Cyble Vision
5. ThreatConnect

ThreatConnect is a threat intelligence operations (TI Ops) platform that helps organizations to operationalize their threat intelligence data for faster detection and response. Unlike traditional Threat Intelligence Platforms (TIP), it supports operational capabilities by integrating AI and automation to aggregate, enrich, and analyze intelligence data.
Key features include:
- Unified threat library: Centralizes threat intelligence data sources, normalizing and scoring data to ensure it is ready for action.
- AI-powered analytics: Uses AI-driven tools like CAL™ and ATT&CK analysis to provide insights, contextualizing threats and behaviors.
- Automation for analysts: Offers automation options, including built-in enrichment and customizable low-code playbooks.
- Visualization tools: Enables threat analysis and relationship mapping using tools such as ATT&CK Visualizer and Threat Graph to understand behaviors of potential threat actors.
- Intelligence requirements management: Allows CTI teams to document, manage, and action intelligence requirements across security operations, cyber risk, and leadership.
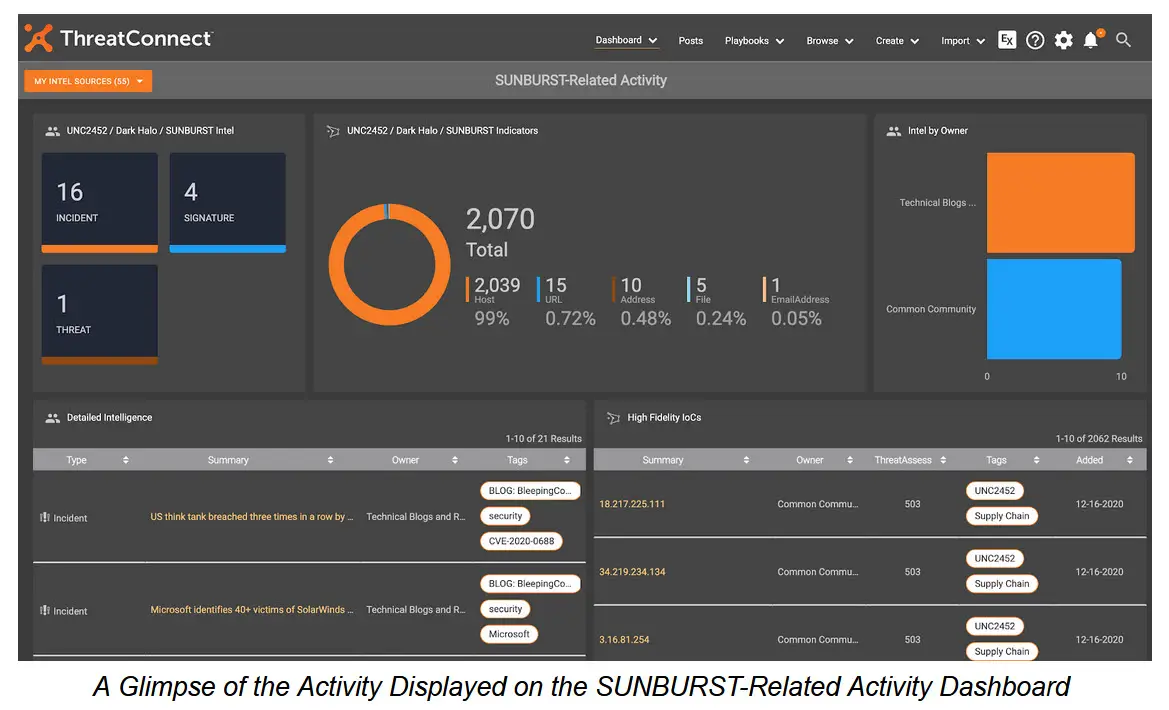
Source: ThreatConnect
6. ANY.RUN

ANY.RUN is an interactive sandbox and threat intelligence platform to accelerate cyberattack investigation and response. The platform allows analysts to analyze and gain context on indicators of compromise (IOCs) by performing fast lookups across a database of over 180 days’ worth of data.
Key features include:
- Threat intelligence lookup: Offers context for threat indicators, including file hashes, IPs, and YARA rules, with a 2-second response time.
- Contextual data enrichment: Enriches threat research by exploring associated metadata, such as threat names, file hashes, registry keys, and attack data from sandbox sessions.
- Community-driven threat intelligence: Accesses threat data from over 15,000 companies and 500,000 analysts to improve SOC efficiency.
- Search capabilities: Supports searches using over 40 search parameters, including TTPs, URLs, paths, and event fields.
- Sandbox session analysis: Helps investigate how threats unfold in sandbox environments by reviewing malware actions and associated IOCs from past research sessions.
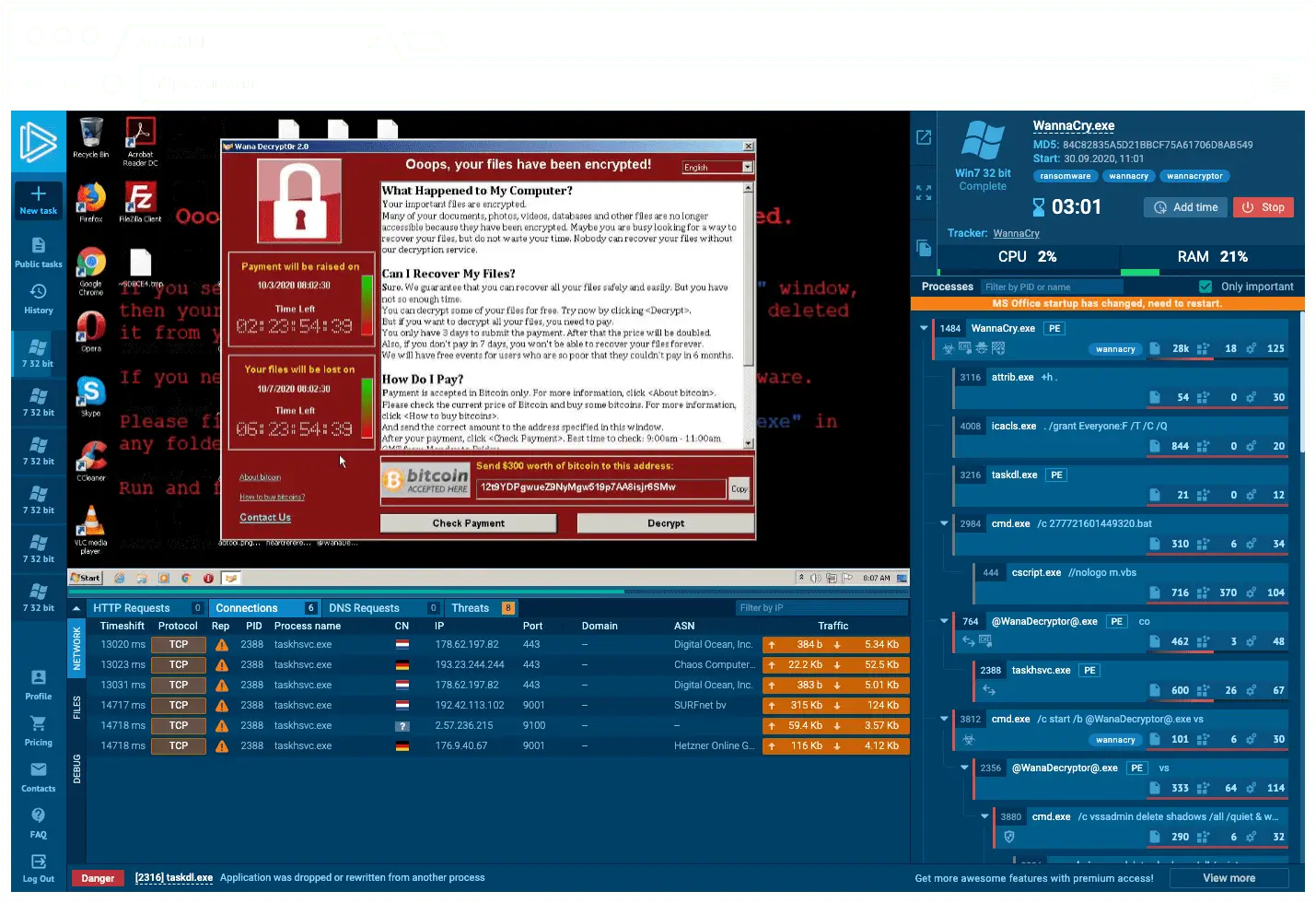
Source: ANY.RUN
7. MISP

MISP (Malware Information Sharing Platform) is an open-source threat intelligence platform for storing, sharing, and correlating Indicators of Compromise (IoCs) and broader cybersecurity intelligence. It supports collaboration between organizations, enabling them to exchange valuable threat data, such as attack indicators, malware analysis, and vulnerabilities.
Key features include:
- Threat intelligence repository: Stores and manages technical and non-technical threat intelligence, including IoCs, attack techniques, and detailed reports.
- Automatic correlation engine: Automatically correlates threat attributes, revealing relationships between indicators, attack campaigns, and malware analysis.
- Flexible data model: Users can create and link complex objects (e.g., attack incidents, malware families) to express relationships and context in threat intelligence data.
- Customizable sharing and distribution: Shares intelligence securely with trusted partners through granular sharing mechanisms, including customizable sharing groups.
- Collaborative threat intelligence: Enables collaboration between users, allowing analysts to propose changes, share opinions, and contribute additional insights.
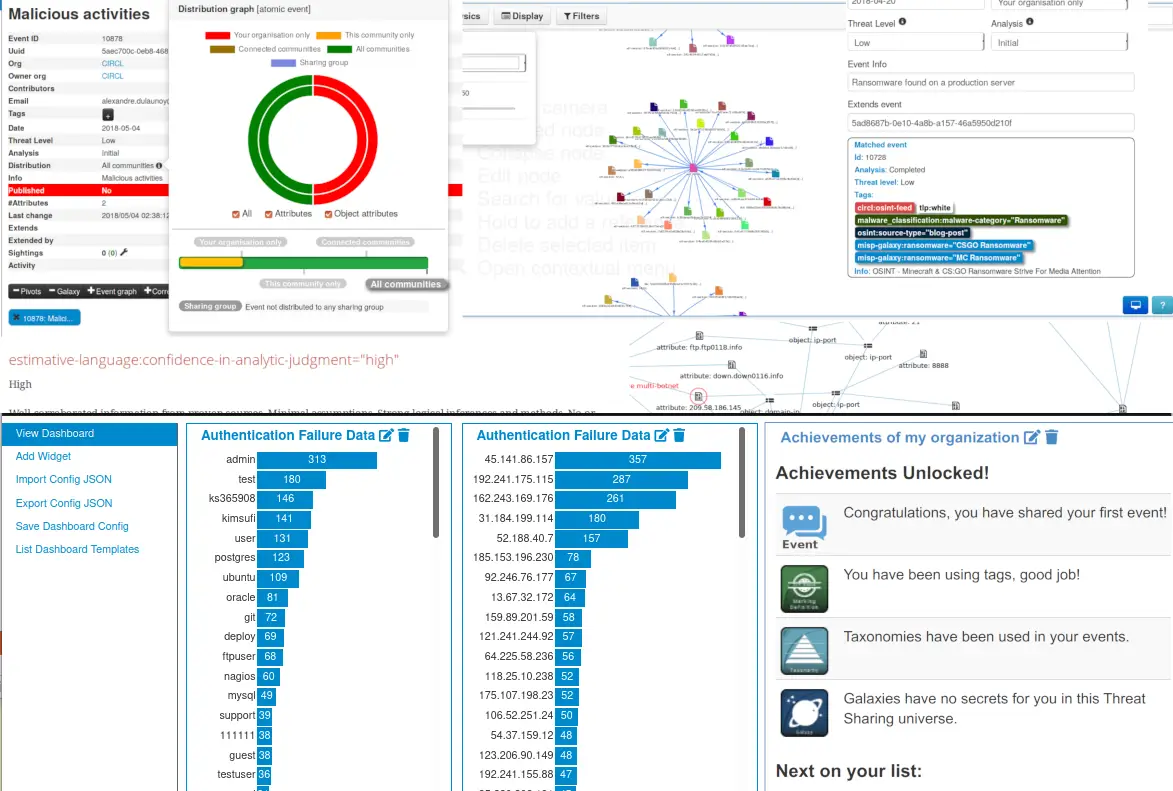
Source: MISP
Conclusion
Threat intelligence tools have become an essential component of modern cybersecurity strategies, enabling organizations to stay ahead of evolving security threats. By providing visibility into the threat landscape, contextual analysis, and integration with existing security infrastructure, these tools empower security teams to detect, prioritize, and respond to threats more effectively.














