Evaluate Merger & Acquisition Risk
Early insight into IT security risk for your merger and acquisition candidates
The CyCognito platform gives you immediate visibility into the risk posture of the targets you are evaluating for merger and acquisition (M&A). Full organizational business mapping, a complete asset inventory, and accurate risk scoring provide the visibility you need to make informed decisions.
As organizations seek to merge and/or acquire other organizations, cybersecurity due diligence has become a staple in the process. Scorecard services are well-known to provide low-value information and unvalidated assessments. Pen tests are costly and impractical for evaluation purposes.
How it helps
No longer base your M&A risk decisions on incomplete or incorrect information. Common M&A challenges include accuracy in security posture assessment, timely access to information, and lack of risk exposure inside subsidiaries.
With CyCognito, you have instant access to your M&A candidate's external attack surface and which assets pose the most risk. It identifies the effectiveness of its security controls without requiring any deployment or configuration.
Benefit 1
Identify risks that would leave your organization exposed
It is unlikely that two organizations have the same security technology stack and practices in place.
CyCognito provides high-confidence insight into risk that allows you to plan for the upcoming event as early as possible around areas such as tool consolidation, testing schedules, and team focus.
Benefit 2
Make sure you know what you are buying
CyCognito builds the business structure map of your target organization, allowing you to verify your knowledge of all associated entities and their risk profile.
The per-business unit security score enables a quick comparison, allowing you to zero in on problem areas rapidly. Misalignments can be tackled quickly and with facts, not estimates.
Benefit 3
Get actionable remediation guidance that you can share
Clear remediation steps, with evidence, allow you to proactively communicate issues in the candidate’s environment.
This includes details on potential impact and supporting evidence. Every asset has attribution information attached as context so that you know the business unit that owns it. Clear remediation steps are included for each issue to understand the effort and estimate costs.
Benefit 4
Complete the M&A event with confidence
Know that you have the risk insight you need to make a data-backed decision.
CyCognito provides you with the full external attack surface, asset context, asset attribution, security test results, and a remediation planner to assist your planning efforts. And once the M&A event has been completed you can continue to track the assets under your new parent organization.
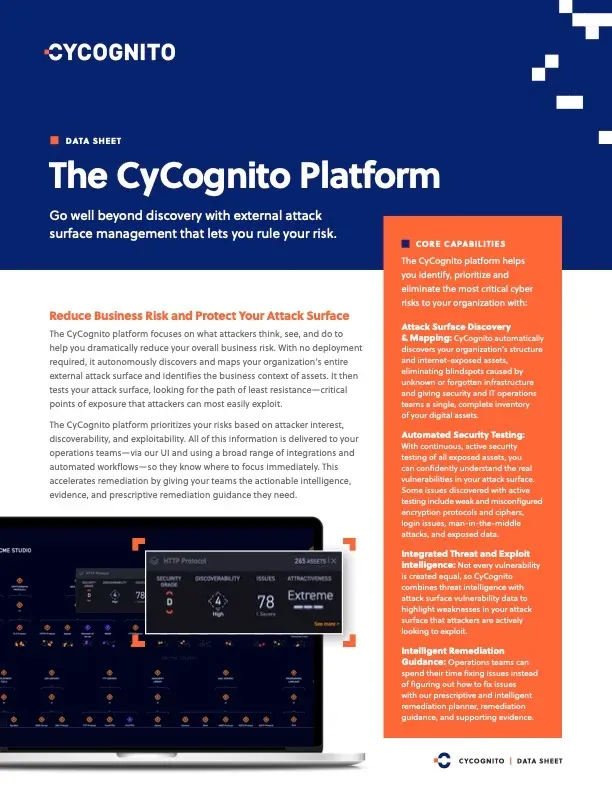
Platform Datasheet
The CyCognito Platform
See how our discovery engine uses graph data modeling to map your organization’s full attack surface. Review our core capabilities, key features and what differentiates us from legacy security tools.