What Are API Security Tools?
API security tools are software designed to protect application programming interfaces (APIs) from various security threats. These tools help enforce security policies, detect and mitigate attacks such as SQL injection, and ensure secure data transfer between systems. API security is critical in today’s interconnected software environment, where APIs serve as the primary method for system integration and data exchange.
These tools offer a range of features including authentication, authorization, traffic management, and encryption. By monitoring API traffic, security tools can identify and block malicious activities, ensuring that only legitimate users and applications have access to sensitive functions and data. This is essential in preventing data breaches and maintaining system integrity.
Key Features of API Security Solutions
Authentication and Authorization
Authentication verifies the identity of a user or system using an API, typically through credentials like tokens. This security layer ensures that only authenticated users can access an API. After authentication, authorization determines the user’s permissions, limiting access to various parts of the API based on roles or policies. This prevents unauthorized access to sensitive data and functions within the system.
Implementing effective authentication and authorization protocols is fundamental to API security. Modern API security solutions usually support various authentication methods such as OAuth, API keys, and JWTs, providing robust security by aligning with the latest standards and practices.
Rate Limiting and Throttling
Rate limiting controls the number of API requests a user or service can make within a specific timeframe, while throttling adjusts the speed of incoming requests. These features protect APIs from overload, ensuring the API’s availability and performance remain stable even under high traffic conditions. This is particularly important to mitigate denial-of-service (DoS) attacks, where attackers attempt to flood the API with an excessive amount of requests.
Throttling and rate limiting both serve as practical approaches to manage and distribute server resources efficiently. By limiting how often users can call an API, these mechanisms help maintain service quality and prevent abuse, ensuring that all users receive fair access to the API.
Logging and Monitoring
Logging involves recording API usage data, while monitoring is the continuous review of this data to identify unusual or harmful activities. Effective logging and monitoring can provide comprehensive visibility into API performance and security, identifying potential security incidents as they happen. This allows organizations to respond promptly to threats, minimizing potential damage.
Logs typically include details about API requests such as the source, destination, and payload. Monitoring these logs helps in diagnosing issues, performing audits, and understanding user behavior. Together, logging and monitoring form a critical part of API security, enabling proactive management and security assurance.
Vulnerability Testing and Security Assessments
Vulnerability testing involves probing an API for security weaknesses, while security assessments evaluate the overall security posture of an API setup. Regular testing and assessments ensure that APIs remain secure against evolving threats.
Automated tools can perform vulnerability testing, simulating attacks and reporting potential weaknesses. Security assessments might involve manual review and comparison against security best practices. Both activities are fundamental in maintaining robust API security frameworks and safeguarding data.
API Gateway
An API gateway acts as a managing point in the API ecosystem, facilitating secure and efficient interactions between clients and services. It provides a single entry point for all API traffic, incorporating security, routing, and other management functions. The gateway can enforce SSL/TLS encryption, authenticate requests, and apply policies uniformly, enhancing security across all services.
Besides security, API gateways optimize service delivery by handling request routing, load balancing, and caching. This not only improves security but also enhances the performance and scalability of API services. An API gateway simplifies API management and is a key component of modern API architecture.
Related content: Read our guide to API discovery.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

Notable API Security Tools
1. Google Apigee Sense
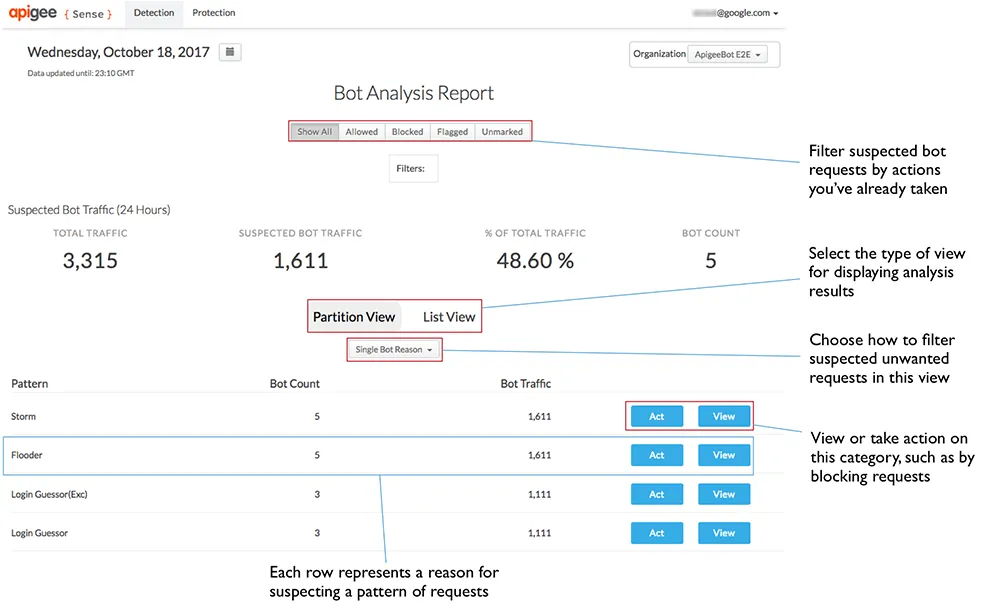
Source: Google Apigee Sense
Google Apigee Sense is an API security tool that leverages intelligent behavior detection to safeguard APIs against various threats, including bot attacks. It uses machine learning algorithms to analyze API metadata, identifying and responding to anomalies in real time. This tool enhances API security with comprehensive monitoring and automatic threat mitigation.
Key features include:
- Intelligent API security: Utilizes machine learning to analyze call patterns from API metadata, autonomously identifying and alerting on suspicious activities.
- Behavior detection: The analysis engine scrutinizes every client request’s metadata, flagging those with suspicious patterns and monitoring for potential API-layer threats.
- Automated risk mitigation: Implements configurable countermeasures such as blocking, throttling, and ensnaring bots, allowing for proactive responses to identified risks.
- Unified API security solution: Offers a unified security framework that manages all aspects of API protection, equipped with visual dashboards for bot analytics and actionable intelligence.
2. StackHawk
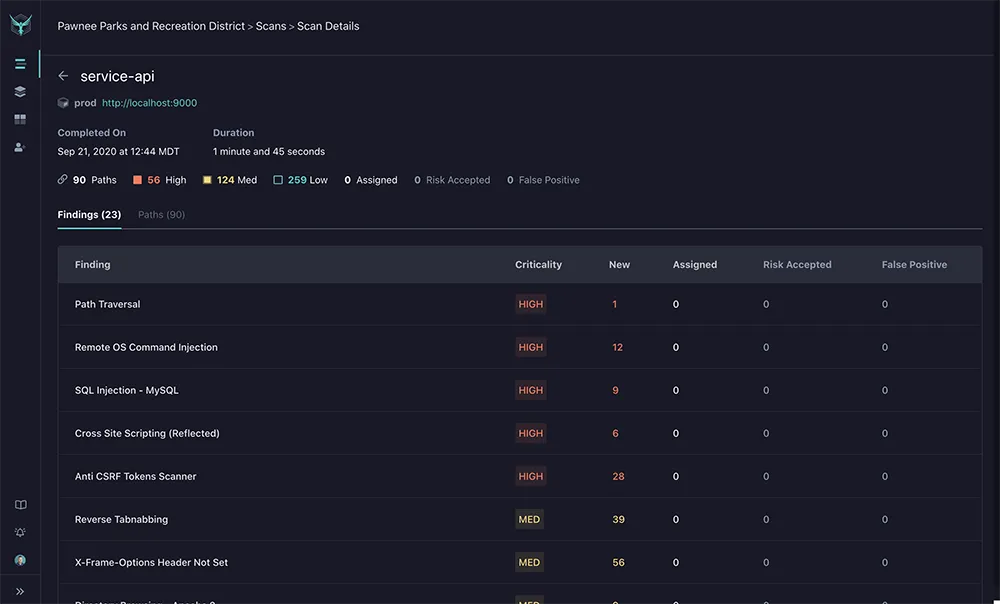
Source: StackHawk
StackHawk is an API security testing platform tailored for applications built on microservices and APIs. It automates security testing across all types of APIs including gRPC, GraphQL, REST, and SOAP, ensuring comprehensive coverage and early detection of vulnerabilities. Designed to integrate seamlessly with CI/CD workflows, StackHawk empowers developers to address security issues before they reach production.
Key features include:
- Comprehensive API coverage: Automates security testing for all API types—gRPC, GraphQL, REST, and SOAP—allowing developers to quickly identify, triage, and resolve security risks. The platform simulates real-world attacks to uncover unexpected data interactions and potential vulnerabilities.
- Automated testing in CI/CD: Integrates with CI/CD pipelines to continuously check for new vulnerabilities with every pull request. This ensures that no API vulnerabilities are unknowingly shipped to production. The platform provides detailed alerts and integrates with tools like GitHub, enhancing developer response times to potential security issues.
- Developer-centric fixes: Offers detailed vulnerability overviews with request/response evidence and fix documentation, enabling developers to quickly understand and rectify issues. StackHawk also supports the recreation of curl commands for findings, facilitating easier and faster fixes.
- Customizable testing and integrations: Allows for the customization of testing logic to either block or pass builds based on the security findings. It supports Docker-based scanner deployment and configuration through code, aligning with DevOps practices.
3. 42Crunch API Security Platform
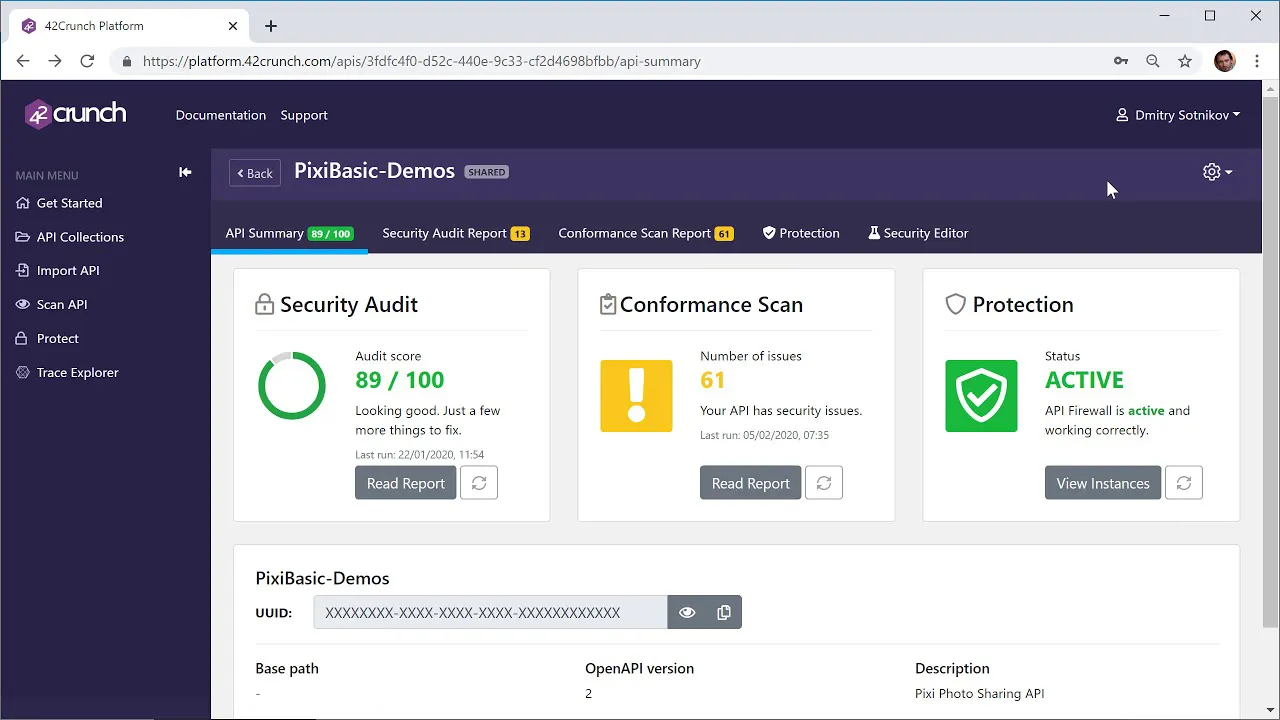
Source: 42Crunch API Security Platform
42Crunch offers a suite of tools that improve API security using a developer-first approach. This platform automates API security compliance across diverse development and security landscapes, especially suited for complex, distributed environments. It supports standardized security practices from API design to deployment.
Key features include:
- API governance and compliance: Automates the discovery and cataloging of APIs, builds API contracts from traffic, and integrates with development repositories. It also standardizes API contracts and manages security compliance and runtime security policies centrally.
- Security by design: Embeds security early in the API lifecycle, which is enforced continuously from design through development, testing, and runtime.
- Automated security testing and vulnerability detection: Empowers developers with tools that eliminate false positives and instantly assesses APIs against over 300 security checks.
- Runtime API threat protection: Automatically configures security settings from API contracts, detects and blocks unauthorized APIs, and applies uniform security policies compatible with any API gateway.
4. IBM API Connect
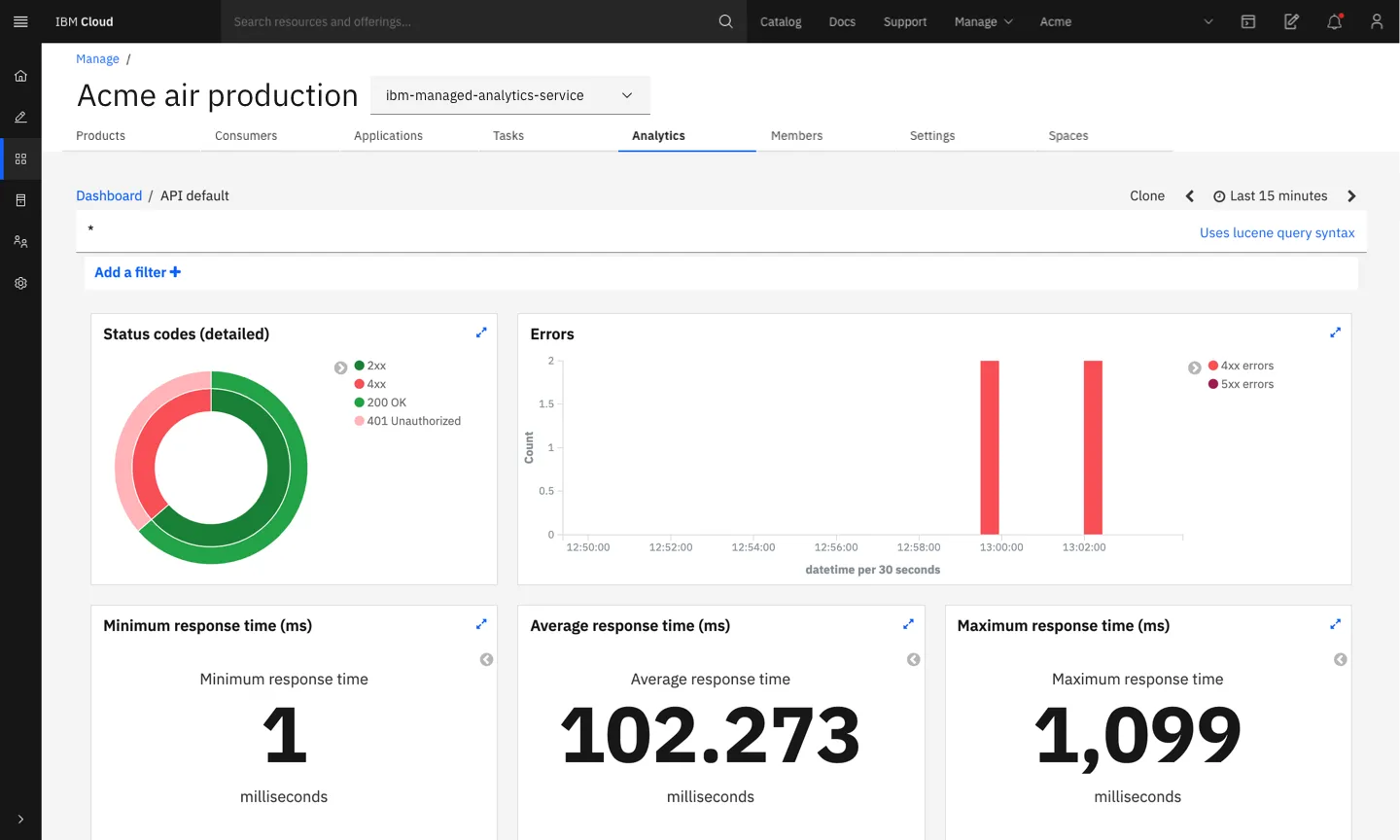
Source: IBM API Connect
IBM API Connect is an API management solution designed to support the full lifecycle of API creation, deployment, and management. It enables the consistent creation, management, and monetization of APIs across various environments, including on-premises and multi-cloud setups. IBM API Connect is available as both a self-managed service and a fully managed service on AWS.
Key features include:
- Intuitive API management: Features an award-winning developer portal with self-service capabilities that streamline the management and deployment of APIs throughout their lifecycle.
- Flexible deployment: Offers versatile deployment options across cloud, on-premises, or hybrid environments.
- Highly secure API exposure: Utilizes a powerful, enterprise-grade API gateway to manage and mitigate cybersecurity risks, protecting data across multi-cloud environments.
- Scalable and trustworthy architecture: Employs a microservices-based architecture that allows for the scaling of components to meet service level agreements and enhance security across all endpoints.
5. Wallarm API Security
Source: Wallarm API Security
Wallarm API Security is a robust solution designed to protect APIs by identifying, blocking, and responding to threats in real-time across entire API portfolios, including cloud-native and legacy applications. It supports a full spectrum of security actions from discovery to response, and integrates seamlessly into continuous integration and deployment pipelines, making it an essential tool for securing APIs in modern IT environments.
Key features include:
- Comprehensive API discovery: Automatically inventories all API assets, maps changes, and reconstructs API and app topology from traffic to provide visibility and control over the API attack surface.
- Advanced protection: Protects against API-specific threats including OWASP Top 10 API Security risks, bots, and Layer 7 DDoS attacks. It also enforces API specifications to ensure compliance with established API standards.
- Dynamic response capabilities: Provides complete visibility into security incidents with the ability to drill down into malicious requests and automate responses based on the severity of the threat.
- Automated API testing: Integrates security testing into the CI/CD pipeline, allowing for continuous assessments and timely identification of misconfigurations and vulnerabilities.
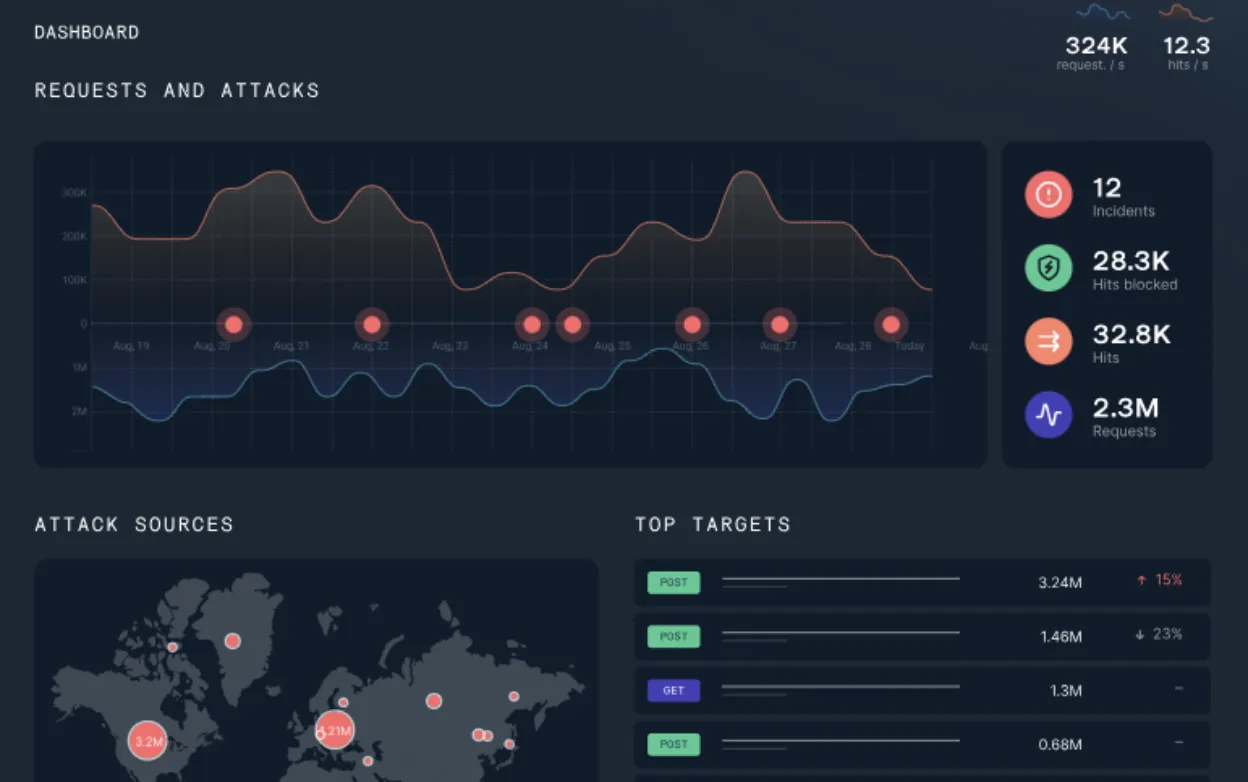
6. SALT API Protection Platform
Source: SALT API Protection Platform
The Salt Security API Protection Platform offers a comprehensive security solution designed to protect APIs throughout their entire lifecycle. Leveraging AI/ML and a scalable API data lake, the platform provides deep visibility into API traffic across all application environments, identifying vulnerabilities, and stopping attacks with actionable remediation insights. The platform requires no changes to existing applications and has no impact on application performance.
Key features include:
- Discovery and posture management: Automatically updates and maintains an inventory of all APIs, highlighting unknown (“shadow”) and outdated (“zombie”) APIs. It assesses the security posture continuously, identifying APIs that expose sensitive data.
- Advanced threat protection: Utilizes extensive data analytics to establish baseline behaviors for users and APIs over time, detecting anomalies and distinguishing between genuine mistakes and attacks. It blocks attackers by consolidating suspicious activities into a single attacker timeline, reducing false positives.
- Automated remediation and testing: Offers insights derived from runtime interactions to identify and remediate vulnerabilities. It analyzes OpenAPI (Swagger) files to detect security gaps and shares detailed remediation insights with development teams.
- Blocking API attacks: Provides a patented API Context Engine (ACE) which identifies behavioral anomalies and effectively reduces alert noise by eliminating most false alerts.
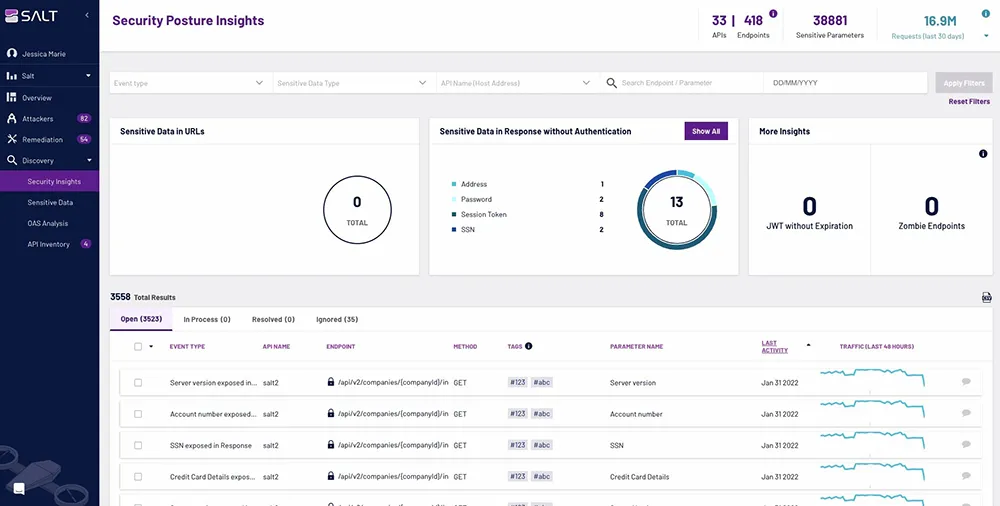
7. Imperva API Security
Source: Imperva API Security
Imperva API Security provides continuous protection for all types of APIs—public, private, and shadow—through deep discovery and classification of sensitive data. The platform ensures security teams can keep pace with API development and prevent data leakage and API abuse.
Key features include:
- API discovery and endpoint security: Conducts deep discovery of all API endpoints, classifying sensitive data to prevent leakage and abuse. It provides continuous monitoring and protection against changes in API structures and usage, covering all aspects of OWASP API Top 10 threats.
- Automated threat classification: Utilizes machine learning and automation to continuously detect and classify threats, enabling real-time responses to emerging risks and maintaining alignment with DevSecOps processes.
- Flexible deployment and API governance: Supports a flexible deployment model that can be tailored to specific organizational needs, facilitating effective API governance and ensuring comprehensive API inventory management.
- Real-time visibility and control: Offers security teams real-time, comprehensive visibility into API inventories, including undocumented or incompletely defined APIs, changes made to APIs in production, and shadow APIs that may be unknown to the organization.
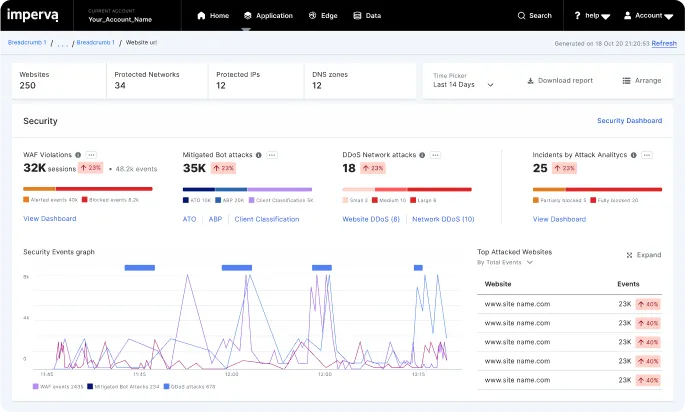
8. Orca API Security
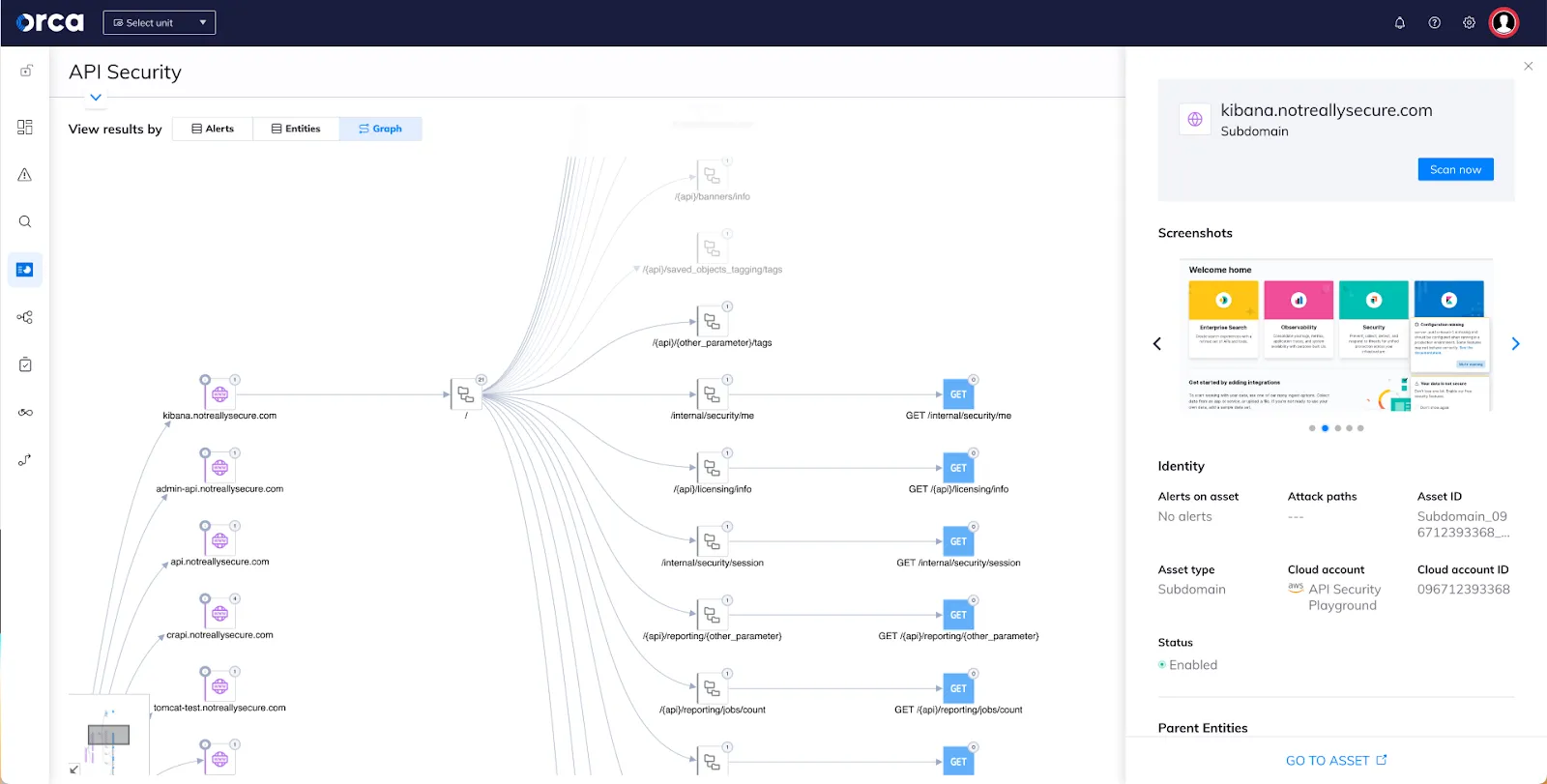
Source: Orca API Security
Orca API Security offers an agentless solution for API security in cloud environments. It provides full visibility and control over API inventories without the need for agents or network modifications, ensuring a low total cost of ownership and eliminating common blind spots of API security solutions.
Key features include:
- Complete API discovery and inventory: Orca Security provides continuous discovery of all API assets across cloud estates, including managed and unmanaged applications, domains, and endpoints. This agentless approach delivers a full inventory of APIs and their security and compliance risks in cloud environments.
- Comprehensive coverage and risk prioritization: The platform offers an extensive view of the API attack surface, enabling quick and accurate identification of API assets and associated risks. Orca leverages deep insights into cloud workloads, configurations, and identities to prioritize risks effectively.
- Frictionless deployment: Orca’s deployment does not require traditional agents, edge workers, or external log analysis, minimizing setup time and maintenance efforts. The solution can provide an API inventory within minutes.
- Continuous monitoring and drift detection: Orca continuously monitors API behavior and usage, alerting security teams to any unwanted changes or drift in API configurations, ensuring compliance with intended API policies.
9. Data Theorem
Source: Data Theorem
Data Theorem API Secure is a comprehensive, automated security service that focuses on continuous monitoring and protection of APIs in modern cloud environments. The platform is designed to discover all APIs, including shadow APIs, and efficiently handle security testing, real-time protection, and auto-remediation of critical issues.
Key features include:
- API discovery and inventory: Uses a black-box approach to continuously monitor and discover APIs across multi-cloud environments such as AWS, Azure, GCP, and private clouds. The service integrates seamlessly with existing API gateways and developer tools to ensure all APIs are inventoried as they are developed.
- Security testing: Offers a variety of security testing methods including static analysis (SAST), dynamic analysis (DAST), software composition analysis (SCA), and fully customized tests with associated hacker toolkits.
- Real-time active protection: Delivers active protection measures for APIs focusing on authentication, authorization, encryption, attack prevention, and protection against malicious sites and domains. It also includes bot protection to safeguard APIs from automated threats.
- Automated alerts and remediation: The analyzer engine detects vulnerabilities in real-time and generates policy-based alerts. It provides auto-remediation solutions that help maintain secure API operations across multiple cloud environments.
Tips from the Expert

Rob Gurzeev, CEO and Co-Founder of CyCognito, has led the development of offensive security solutions for both the private sector and intelligence agencies.
In my experience, here are tips that can help you better enhance your API security strategy:
- Implement Zero Trust principles: Apply a Zero Trust model to APIs by assuming every request is potentially hostile, even those from internal networks. Enforce strong identity verification, least privilege access, and continuous validation of request integrity.
- Employ API security testing as part of CI/CD pipelines: Integrate API security testing early and consistently within your CI/CD pipeline. This ensures vulnerabilities are detected and remediated before APIs are deployed into production environments.
- Utilize encryption for all API communications: Ensure that all data exchanged via APIs, including internal APIs, is encrypted in transit using protocols like TLS 1.3. This prevents data interception and man-in-the-middle attacks.
- Secure API keys and secrets management: Implement robust secret management practices, including rotating API keys and using hardware security modules (HSMs) or cloud-based key management services to securely store API keys.
- Perform threat modeling specific to APIs: Conduct threat modeling exercises focused on APIs to understand how attackers might exploit API-specific vulnerabilities. This proactive approach allows you to design countermeasures before attacks occur.
How to Choose an API Security Solution
Here are some of the key considerations for selecting an API security solution:
- Integration and compatibility: The solution should support the types of APIs your organization uses, such as REST, GraphQL, or SOAP, and be compatible with your development tools, API gateways, and CI/CD pipelines. Compatibility with your infrastructure, whether it’s on-premises, cloud-based, or hybrid, is crucial for smooth deployment and operation.
- Scalability: As your API usage grows, the chosen security solution must be able to scale accordingly. Look for tools that can handle increased traffic and a growing number of API endpoints without compromising performance or security. A scalable solution ensures that your API security framework can expand in line with your business needs.
- Ease of use: The user-friendliness of an API security tool is vital for its adoption and effectiveness. The solution should offer intuitive interfaces, clear documentation, and robust support. Features like automated configuration, out-of-the-box policies, and comprehensive dashboards can significantly enhance usability.
- Real-time monitoring and alerts: Look for tools that offer comprehensive logging, anomaly detection, and instant alerting systems. These features enable quick identification and mitigation of potential security incidents, reducing the risk of data breaches and other malicious activities.
- Compliance and regulatory support: The tool should support compliance with frameworks such as GDPR, HIPAA, PCI-DSS, and others pertinent to your business, and provide the required reports and audit trails.
- Customizability: Choose a solution that allows for customization of security policies, testing procedures, and threat responses. The ability to tailor the tool to meet specific security requirements and business processes ensures more effective protection and operational alignment.
API Security with CyCognito
CyCognito is an exposure management platform that reduces risk by discovering, testing and prioritizing security issues. The platform scans billions of websites, cloud applications and APIs and uses advanced AI to identify the most critical risks and guide remediation.
Emerging companies, government agencies and Fortune 500 organizations rely on CyCognito to secure and protect from growing threats.
Want to see how it works?
- Check out our website and explore our platform with a self-guided, interactive dashboard product tour.
- To learn how CyCognito can help you understand your external attack surface and exposed risks, please visit our Contact Us page to schedule a demo.














