What Are Red Teaming Tools?
Red teaming tools are specialized software, scripts, or utilities used by security professionals to emulate real-world cyberattacks and assess the security posture of a target organization. These tools help identify vulnerabilities, weaknesses in systems, applications, and processes, and improve defenses. They are used to simulate various attack stages, from reconnaissance to post-exploitation, and help organizations improve their ability to detect and respond to threats.
By using red teaming tools, penetration testers and ethical hackers can identify vulnerabilities, test detection and response mechanisms, and enhance overall security posture without causing actual damage. Red team operations, where defenders may or may not be aware of the exercise, enable an unfiltered evaluation of detection and response workflows. The insights gained from red teaming tools help organizations strengthen their defenses and improve incident response.
Key Features of Red Teaming Tools
Customizable Attack Scenarios
Customizable attack scenarios allow red teamers to simulate a broad range of threats tailored to an organization’s unique environment. Red teaming tools enable operators to craft specific narratives, from phishing and social engineering campaigns to advanced lateral movement through internal networks. This flexibility ensures that testing remains relevant and addresses real-world concerns rather than relying on rigid, generic templates.
By customizing attack workflows, red teams can recreate the tactics of known threat actors or explore potential novel attack paths unique to the target organization. This capability is crucial for evaluating how well existing defenses can recognize, investigate, and respond to customized threats, providing actionable feedback that goes beyond standard vulnerability reports.
Initial Access, Stealth and Evasion Techniques
Stealth and evasion capabilities are core features of red teaming tools, allowing them to bypass conventional security controls and achieve persistent access to the target organization. Techniques such as obfuscation, process injection, and command and control traffic mimicry help red teams remain undetected for longer periods during testing. Achieving stealth is vital for simulating advanced persistent threats (APTs) that deliberately avoid detection over extended engagements.
Effective evasion techniques also challenge defensive solutions like endpoint detection and response (EDR), security information and event management (SIEM), and network intrusion detection systems (NIDS). When red teaming tools circumvent these controls, defenders gain a clearer understanding of detection gaps and are better prepared to anticipate real-world evasion strategies employed by sophisticated attackers.
Privilege Escalation
Privilege escalation features in red teaming tools enable simulation of attackers gaining elevated access within a target environment. These tools automate the discovery of misconfigurations, vulnerable services, or weak access controls that allow lateral movement or administrative privilege gain. They support both vertical escalation (gaining higher privileges on the same system) and horizontal escalation (moving across systems or accounts at the same privilege level), often by leveraging known exploits, credential reuse, or token impersonation.
Advanced red teaming tools can identify opportunities for privilege escalation through local enumeration of permission sets, group memberships, and service configurations. They may also test Active Directory abuse techniques, such as Kerberoasting or exploitation of unconstrained delegation. Simulating these techniques helps defenders understand real escalation paths that attackers could use and implement targeted hardening measures.
Automation and Adversary Emulation
Automation capabilities within red teaming tools streamline the execution of complex attack chains and repetitive tasks, increasing the efficiency of engagements. Automated workflows can replicate multiple attack paths quickly, ensuring thorough coverage without requiring constant manual intervention. This allows red teamers to focus on creativity and in-depth analysis rather than operational overhead. Adversary emulation further enhances automation by modeling specific threat actors’ behaviors, including their preferred tools and techniques.
This level of detail enables organizations to prioritize defenses against relevant threats and gain insight into their exposure to actors targeting similar industries or technologies. Automation and emulation together reduce the time and resources required for effective red teaming, while maintaining realistic and meaningful simulations.
Reconnaissance and Enumeration
Red team operations often start with reconnaissance and enumeration, making these features essential in read teaming tools. Reconnaissance gathers public and internal information about the organization, such as domain names, IP ranges, employee details, and publicly accessible assets. Enumeration drills deeper, mapping internal infrastructure, discovering open ports, services, user accounts, and shared resources.
Having robust capabilities for these tasks allows red teams to realistically mirror the intelligence-gathering phases of adversaries. Efficient reconnaissance and enumeration inform targeted attack planning and help uncover potential pivot points and exploitable weaknesses. The insights gathered from red teaming tools during this phase illustrate the organization’s visibility on the internet and internal networks, guiding improvement of perimeter and internal defenses.
Integration and Reporting
Integration features let red teaming tools seamlessly communicate with existing security infrastructure and other assessment platforms. API support and SIEM connectors enable automated alert generation, event correlation, and ticketing. This ensures that red teaming activities are tracked within the organization’s regular workflows, supporting continuous improvement cycles and incident handling.
Comprehensive reporting is equally important, as it translates engagement findings into actionable deliverables for stakeholders. Modern red teaming tools generate detailed reports that document exploited vulnerabilities, attack paths, detection checkpoints, and remediation recommendations. These reports support technical staff with granular evidence and assist executives in understanding the overall risk posture and prioritizing investments.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

Notable Red Teaming Tools
1. CyCognito

CyCognito external exposure management platform supports red teams and penetration testers efforts by automating reconnaissance and testing activities. CyCognito’s platform helps red teams by providing a single source of truth for attack surface information, automating repetitive reconnaissance work, and offering context and attribution for external assets.
Key features include:
- Continuous asset discovery and monitoring: Maps an organization’s entire attack surface, including both known and previously unknown assets, and continuously monitors them.
- Automated reconnaissance: Automates the initial reconnaissance phase, replicating attacker workflows to identify exposed assets and potential vulnerabilities.
- Automated security testing: Applies tens of thousands of security tests across the attack surface to identify risk and exposure.
- Prioritization and remediation: The platform prioritizes vulnerabilities based on business context and provides guidance on remediation.
- Integration and collaboration: The platform integrates with various security tools and allows for the creation of subteams dedicated to specific red team or pen testing tasks.
2. Pentera

Pentera is a pentesting tool that improves the productivity and reach of red teams by safely emulating attacker behavior. It automates the execution of adversarial tactics and techniques, allowing red teams to focus on high-value investigations.
Key features include:
- Adversary emulation: Executes attack scenarios using TTPs aligned with the MITRE ATT&CK® framework, simulating how real attackers would navigate the network.
- Scenario configuration: Allows teams to design, schedule, and customize test.
- Scalable red teaming: Increases red team coverage across the attack surface without the need for additional headcount.
- Continuous validation: Provides ongoing assessment of defense posture.
- Focus on high-value tasks: Automates routine adversarial testing so security experts can concentrate on advanced threat hunting and targeted exploit development.
Visit here to learn more about red teaming vs pentesting
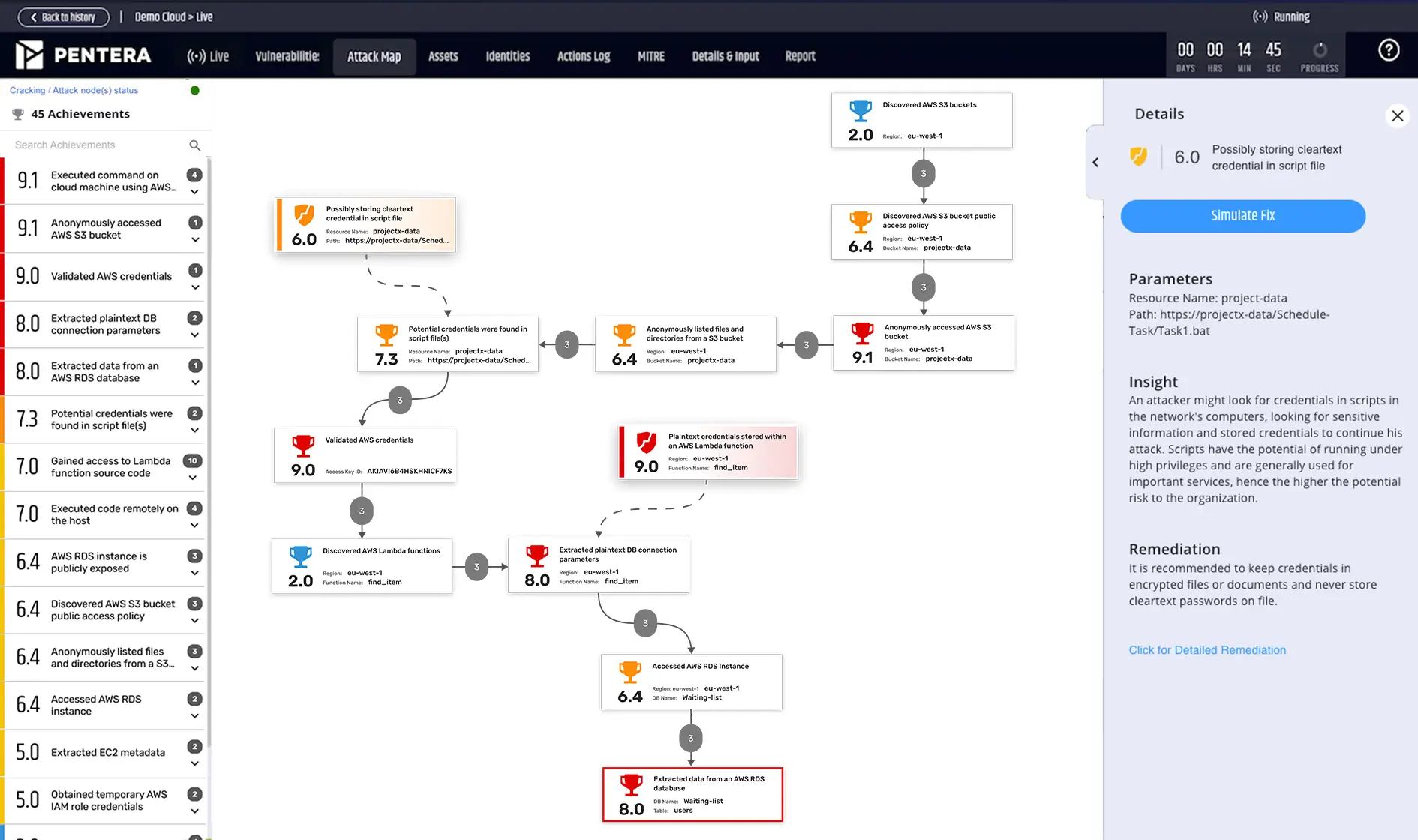
Source: Pentera
3. Mindgard

Mindgard is an automated AI red teaming tool and security testing platform to uncover risks in AI systems that traditional application security tools might miss. It conducts continuous, runtime-based security assessments throughout the AI software development lifecycle.
Key features include:
- AI-specific risk detection: Identifies vulnerabilities unique to AI systems that arise during runtime.
- Automated red teaming: Simulates adversarial behavior to test how AI systems respond to attacks and misuse.
- Continuous security testing: Provides ongoing assessments across the AI SDLC to catch risks early and track remediation over time.
- Integration with existing tools: Connects with reporting platforms and SIEM systems.
- Built for generative AI: Tailored for organizations using generative AI in production environments.
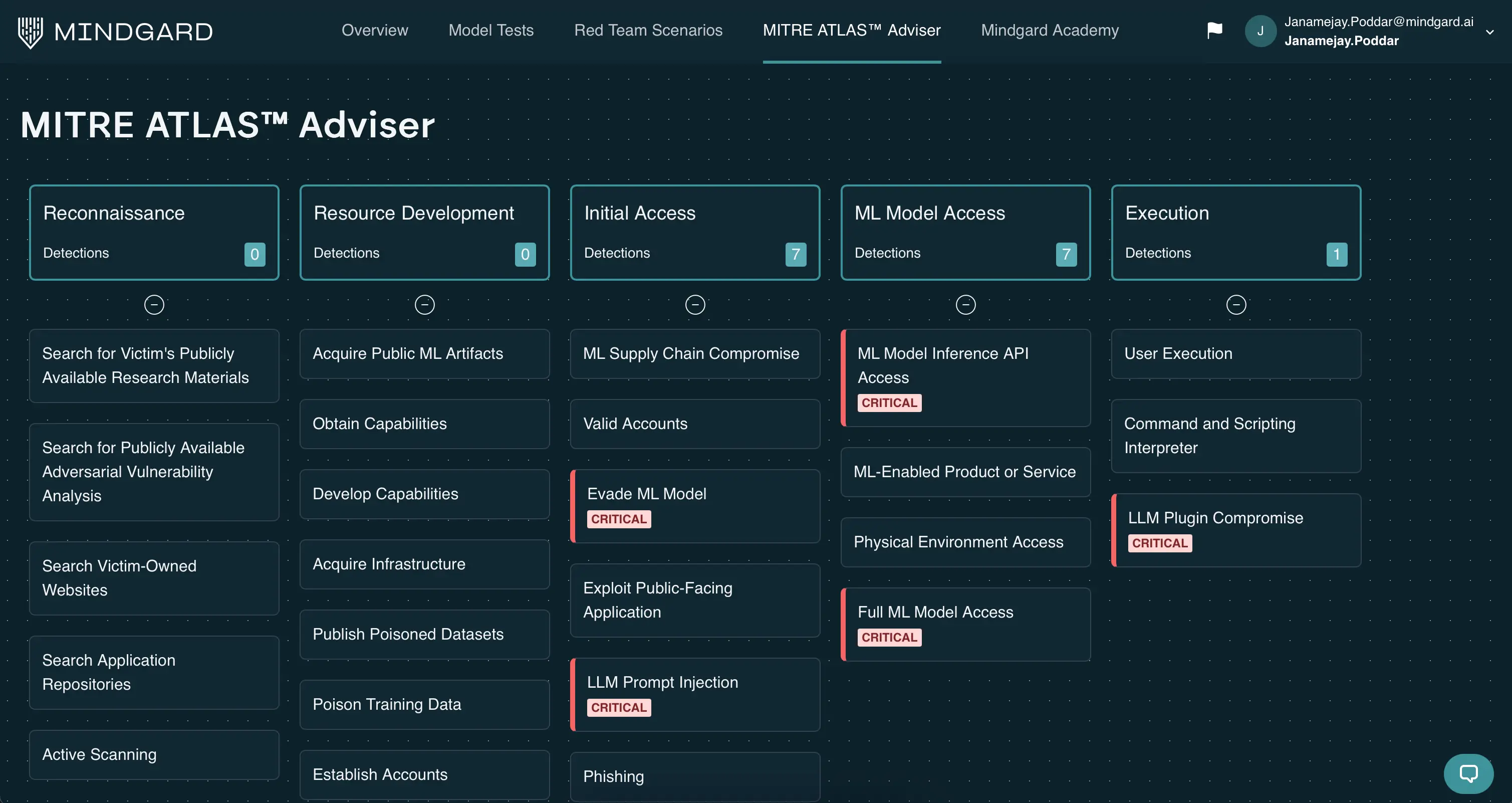
Source: Mindgard
4. FireCompass

FireCompass is a Continuous Automated Red Teaming (CART) platform to identify and prioritize threats across an organization’s digital footprint. Unlike traditional red teaming, which is limited by time, scope, and cost, FireCompass operates continuously, automating reconnaissance, attack emulation, and validation.
Key features include:
- Automated red teaming tool: Simulates multi-stage attacks continuously.
- Attack surface management: Performs reconnaissance across IPs using surface, deep, and dark web OSINT sources, with ML-driven asset attribution.
- Network and application pentesting: Emulates malware injection, privilege escalation, and lateral movement, while analyzing app architecture to uncover configuration and code-level flaws.
- Objective-based red teaming playbooks: Uses customizable playbooks to replicate threat scenarios based on an organization’s environment and risk profile.
- MITRE-based kill chain emulation: Automates end-to-end attack chains using the MITRE ATT&CK framework.
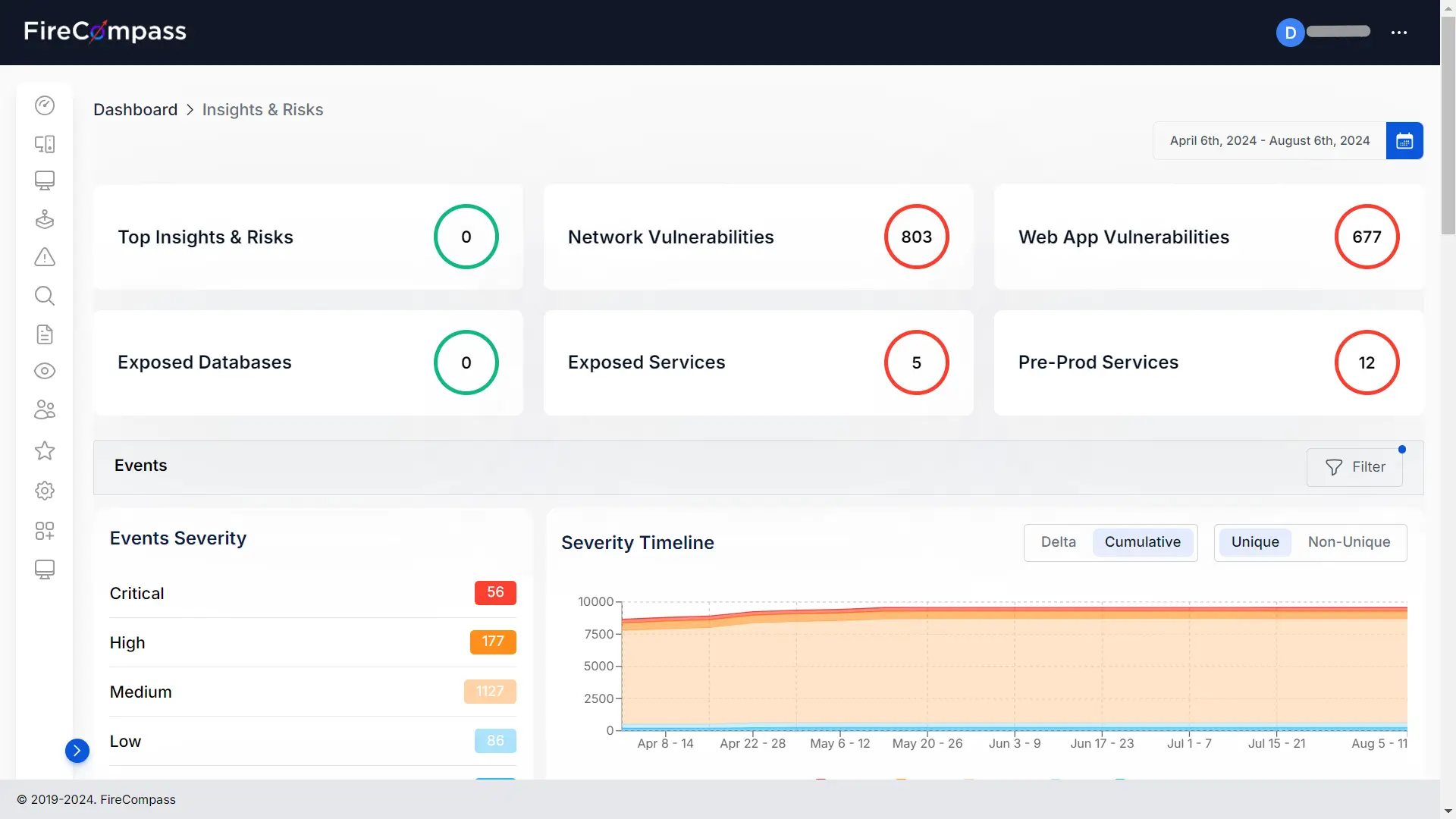
Source: FireCompass
5. Cobalt Strike

Cobalt Strike is a threat emulation platform used in red teaming to simulate post-exploitation behavior. It allows operators to replicate the tactics and techniques of adversaries, providing a controlled environment to test detection and response capabilities.
Key features include:
- Beacon payload: A post-exploitation agent that supports command execution, keylogging, privilege escalation, and more, while evading detection.
- Social engineering tools: Capabilities to craft spear-phishing emails and malicious documents for simulating initial access.
- Collaboration support: Real-time team collaboration features for coordinated red team engagements.
- Malleable C2 profiles: Customizable command and control traffic to mimic known threat actor behaviors.
- Post-exploitation modules: Tools for credential harvesting, lateral movement, and data staging.
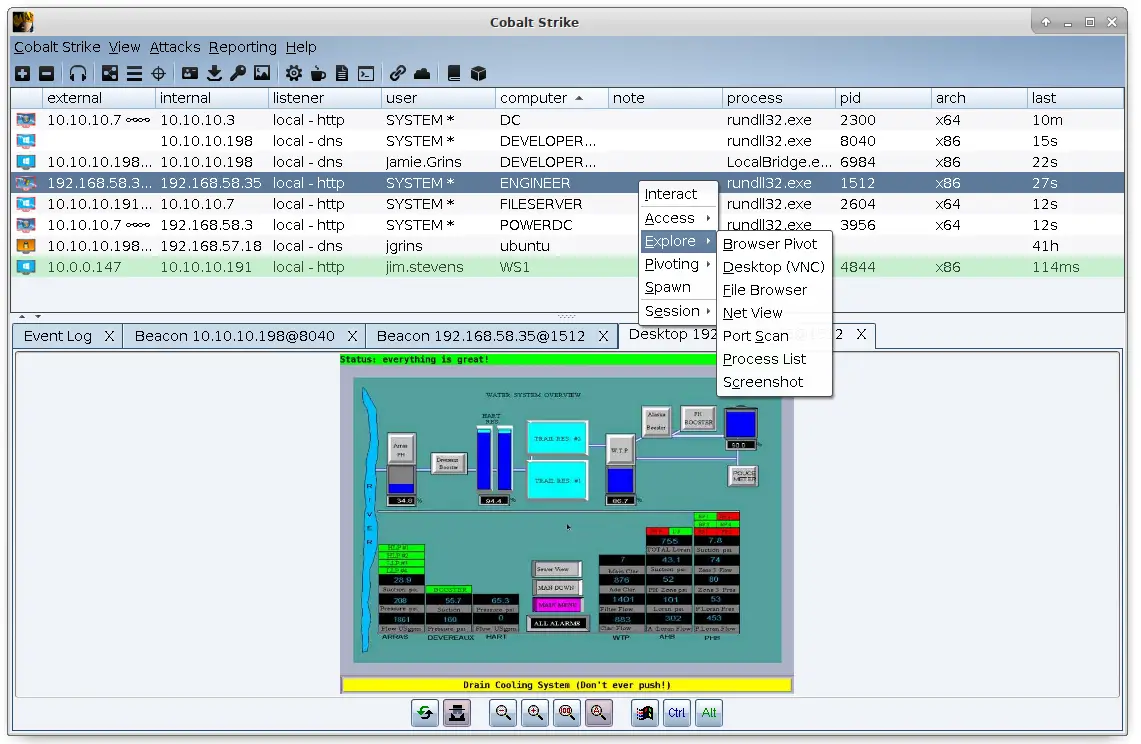
Source: Cobalt Strike
6. PyRIT

PyRIT (Python Risk Identification Tool for generative AI) is an open source red teaming tool that helps security engineers uncover vulnerabilities in generative AI systems. It supports risk identification through custom test cases, enabling red teams to assess how generative models handle inputs designed to elicit unsafe, biased, or unauthorized outputs.
Key features include:
- Generative AI risk focus: Built to assess risks in generative AI systems, such as large language models and image generators.
- Custom tools development: Users can craft test scenarios that simulate adversarial prompts or model misuse.
- Open source framework: Freely available and supported by a community of contributors.
- Red teaming for AI safety: Enables structured security testing of AI outputs, helping identify edge cases and failure modes.
- Community support: Includes access to resources, documentation, and discussion via the project’s website and Discord server.
Source: PyRIT
7. Garak

Garak is a specialized automated red teaming tool focused on uncovering security weaknesses in language model deployments. It targets the failure modes of LLMs, such as prompt injection, jailbreaks, and guardrail bypass, and probes models using an set of aggressive prompts and plugins to simulate realistic attack scenarios.
Key features include:
- LLM-centric security focus: Built to detect vulnerabilities such as jailbreaks, text replay, and prompt injection.
- Probing toolkit: Uses hundreds of probes and thousands of prompts.
- Automated scanning: Runs scans autonomously, handling configuration, detectors, and rate limits without supervision.
- Support for multiple LLMs: Compatible with platforms like OpenAI, Hugging Face, Cohere, and Replicate.
- Adaptive red teaming: Continuously improves test strategies using a feedback loop from previous scan results.
8. Wireshark

Wireshark is a network protocol analyzer used to inspect and analyze live or recorded traffic in detail. While not a red teaming tool in the traditional sense, it plays a supporting role by helping red teams monitor and understand network activity during engagements.
Key features include:
- Packet capture and analysis: Captures traffic from a range of network interfaces for inspection.
- Protocol support: Parses hundreds of network protocols with human-readable decoding.
- Filtering and search: Advanced display filters to isolate traffic of interest during complex assessments.
- Traffic reconstruction: Ability to reassemble and analyze complete sessions and payloads
- Extensibility: Support for custom dissectors and plugin development.














