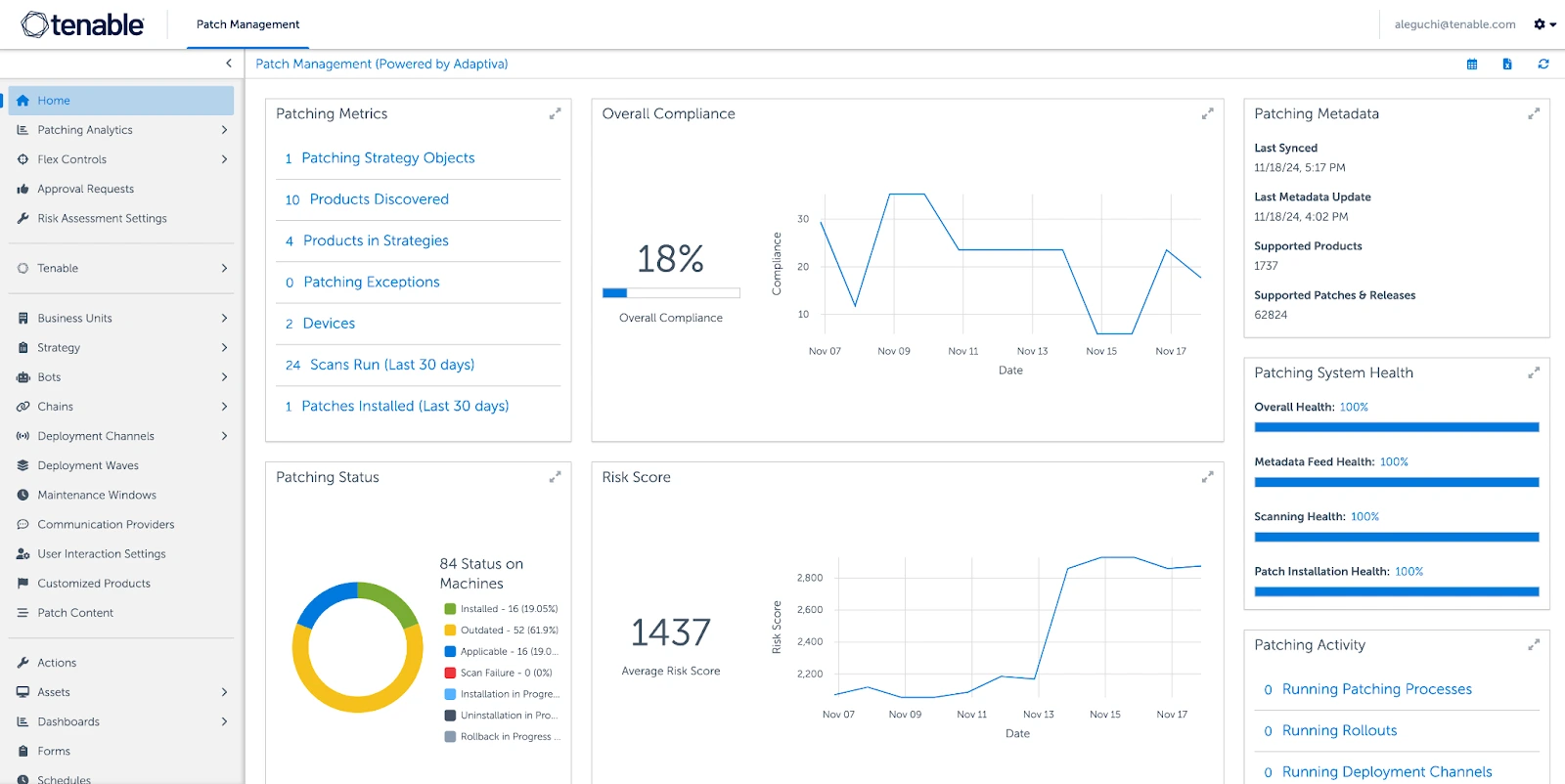
What Are Vulnerability Management Tools
Vulnerability management tools automate how organizations find, assess and fix security weaknesses across their networks and applications. They combine scanning, risk-based prioritization, guided or automated remediation and integrations with existing security and IT systems.
What needs do vulnerability management tools address?
From day-to-day operations to long-term risk reduction, vulnerability management tools address needs like:
- Handling scale and complexity: As environments spread across thousands of assets, manually tracking issues and patches stops working. These tools centralize discovery, vulnerability assessment and remediation so teams do not rely on spreadsheets and ad hoc audits.
- Keeping up with evolving threats: Attackers often go after unpatched systems, misconfigurations and newly disclosed vulnerabilities. Continuous scanning and risk-based prioritization help teams spot emerging issues quickly and focus on exposures that actually change risk.
- Bringing fragmented infrastructure into one view: Modern estates span on-premises servers, multiple clouds and remote user devices. Vulnerability management platforms consolidate scanning across all of these and present unified dashboards for risk and remediation progress.
- Streamlining patch management: Instead of separate lists and ticket queues, these tools link vulnerability data directly to remediation workflows. By automating parts of the patch cycle, they cut delays, lower manual error rates and free teams to focus on higher value work.
- Supporting regulatory compliance: Detailed audit logs and tracked remediation timelines help demonstrate that the organization is actively managing risk. This is often required for frameworks such as HIPAA or PCI DSS.
- Improving consistency and coverage: Automation helps ensure vulnerabilities are classified correctly, escalated based on severity and risk and not quietly lost in the noise. That makes it easier to apply policies consistently and show that exposures are being managed in a structured way.
Key Features to Look for in Vulnerability Management Tools
Comprehensive Asset Coverage
A critical feature of any vulnerability management tool is comprehensive asset coverage, ensuring visibility across all exposed assets, including web application, API, cloud and network devices. Effective tools continuously scan and monitor assets as they come online, capturing both managed and unmanaged devices. Without total asset visibility, critical exposures may remain undetected, leaving gaps in the organization’s defenses.
Asset discovery should not be limited to typical IT infrastructure. Modern tools extend their reach to cloud resources, remote endpoints, IoT devices, and even shadow IT systems that evade traditional inventory processes. They use network scanning, agent deployment, and integration with asset management platforms to create a complete map of the attack surface. This holistic view is essential to ensuring that no vulnerable asset is missed during scans or remediation efforts.
Risk Prioritization
Risk prioritization distinguishes high-quality vulnerability management tools from basic scanners. Given the large volume of vulnerabilities that can surface from automated scans, organizations need tools that intelligently rank vulnerabilities by potential impact and exploitability. Advanced risk models factor in CVSS scores, real-world threat intelligence, exploit availability, asset criticality, and business context to highlight the issues that truly matter.
Prioritization helps security teams avoid alert fatigue and focus limited remediation resources where they are needed most. Instead of working through lengthy generic lists, teams can act on the highest-risk findings first, reducing the likelihood of a breach from an actively exploited vulnerability. This makes risk-driven vulnerability management both more practical and more cost-effective, aligning remediation with organizational risk appetite and business objectives.
Remediation Guidance
Effective vulnerability management tools go beyond simply finding vulnerabilities, they also provide clear, actionable remediation guidance. This means recommending specific patches, configuration changes, or mitigation steps for each vulnerability based on the context in which it appears. By linking directly to vendor advisories, software updates, or knowledge base articles, these tools help streamline the path from detection to resolution.
Detailed guidance reduces the burden on security and IT teams by minimizing manual research. The best solutions also prioritize remediation tasks and assign them to specific teams or individuals, tracking remediation status and verifying when vulnerabilities have been resolved. This closed-loop process ensures that vulnerabilities are not only found but also remediated in a timely and auditable manner, supporting both operational security and regulatory compliance.
Automation and Orchestration
Automation is essential for vulnerability management at scale, enabling organizations to scan assets, assess risk, and trigger remediation workflows without constant manual oversight. The most effective tools support scheduling, agentless and agent-based scans, automatic ticket creation, and in some cases, auto-remediation actions based on pre-defined policies. Orchestration capabilities allow these automated processes to connect with patch management, IT operations, or incident response systems.
By reducing reliance on manual effort, automation improves both the speed and consistency of vulnerability management processes. This is particularly important for large or rapidly evolving environments. Automation not only accelerates time-to-remediation but also ensures that tasks do not slip through the cracks, which is critical for regulatory compliance and overall risk management.
Integration with the Existing Security Ecosystem
Modern vulnerability management tools must integrate seamlessly with existing security and IT systems. Integration with SIEMs, ticketing platforms, patch management systems, and asset management solutions ensures that vulnerability data is actionable and remediation is tracked within existing workflows. APIs and webhooks further expand integration capabilities, making it possible to automate handoffs between tools.
Without integration, organizations risk fragmented processes and siloed data, leading to delays and gaps in remediation. Effective integrated platforms allow for centralized visibility and streamlined response efforts, enabling teams to move quickly from detection to action. A well-integrated tool creates a unified security posture, leveraging the organization’s broader technology stack to reduce risk.
Support for Open Source and SBOMs
With widespread adoption of open-source components, vulnerability management tools should support open-source vulnerability scanning and Software Bill of Materials (SBOM) analysis. Effective tools scan dependencies in code repositories, containers, and built artifacts, identifying known vulnerabilities reported in public databases like the National Vulnerability Database (NVD). This helps organizations mitigate risks arising from the use of open-source libraries and frameworks.
SBOM support enables organizations to comply with emerging regulatory requirements and supply chain risk initiatives by providing visibility into all software components in use. By continuously monitoring for vulnerabilities in open-source and third-party software, organizations can quickly identify and remediate exposures as they arise, protecting applications and services from exploitation throughout their development and deployment lifecycles.
Compliance and Regulatory Alignment
Vulnerability management is closely linked to regulatory compliance. Many standards, including PCI DSS, HIPAA, NIST, and GDPR, require regular vulnerability scanning and documented remediation. Effective tools provide features such as automated audit trails, compliance-specific reporting, and policy mapping to simplify adherence and evidence gathering for audits.
Regulatory alignment reduces the risk of fines or breaches related to non-compliance. Vulnerability management solutions that automate reporting, demonstrate continuous vulnerability assessment, and support regulatory frameworks help organizations maintain a strong compliance posture. Alignment with compliance requirements ensures that security and risk reduction efforts are in sync with legal obligations, helping organizations avoid regulatory penalties and maintain customer trust.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

Notable Vulnerability Management Tools
1. CyCognito

CyCognito is an attack surface management (ASM) platform that expands on the capabilities of traditional vulnerability management tools and scanners. It takes an external, attacker-centric view of the organization, identifies what is exposed to the internet and evaluates which issues create meaningful risk. Instead of relying only on internal inventories or scheduled scans, it connects external exposures to business context, ownership and remediation outcomes.
Key features include:
- Seedless asset discovery: Identifies known and unknown internet-facing assets across cloud environments, web applications, DNS, IP ranges and subsidiaries without agents, internal network access or any manual input.
- Automated security testing at scale: Continuously runs automated AI-driven security tests using a large library of exploit and validation modules (over 90,000) to validate exposures and reduce false positives.
- Contextual risk prioritization: Highlights critical vulnerabilities based on active test findings, attacker reachability, exploitability and business impact, not just static CVSS scores.
- Attack path mapping: Shows how vulnerabilities relate to each other and highlights potential routes an attacker could use to move deeper into the environment. Integration with CAASM, CNAPP and other internal cyber asset management tools further enriches this view.
- Ownership attribution: Links assets and findings to the appropriate internal teams or system owners so remediation can start quickly and in the right place.
- Automated remediation flows: Uses automation and insights about asset ownership to accelerate remediation and close the loop on the vulnerability management lifecycle. Provides concrete fix steps, integrates with ticketing systems and verifies when issues have been resolved.
- Continuous monitoring: Tracks changes across the external attack surface and flags new vulnerabilities as they appear, making it a bedrock for a CTEM program.

With a combination of seedless discovery, active automated pentesting and AI-driven prioritization, testing and remediation, CyCognito pushes the envelope of traditional vulnerability management by focusing on the real external attack surface adversaries see and by turning those exposures into clear, owned and trackable remediation work.
2. Tenable

Tenable Vulnerability Management provides organizations with visibility into their IT environment, helping them detect, prioritize, and remediate vulnerabilities before they can be exploited. The platform combines continuous asset discovery with risk-based intelligence to identify both known and unknown exposures across on-premises, cloud, and remote assets.
Key features include:
- Continuous asset discovery: Identifies known and unknown assets, including dynamic cloud and remote workforce environments.
- Risk-based prioritization: Uses Tenable’s Vulnerability Priority Rating (VPR), powered by AI and enriched with threat intelligence, to rank vulnerabilities by exploitability and impact.
- Threat contextualization: Leverages Tenable Research data to provide context around weaponization, severity, and remediation urgency.
- Guided remediation: Offers best-practice remediation steps to quickly address high-risk vulnerabilities.
- Benchmarking and trend tracking: Monitors remediation progress and compares performance against industry peers.
3. Qualys

Qualys Vulnerability Management, Detection & Response (VMDR) delivers visibility and risk reduction by unifying asset discovery, vulnerability assessment, prioritization, and remediation in one platform. It leverages the TruRisk™ framework with threat intelligence to measure and communicate business risk while simplifying response workflows.
Key features include:
- Asset coverage: Identifies known and unknown assets across cloud, container, endpoint, and mobile environments using cloud agents, passive sensors, and virtual scanners.
- Risk-based prioritization: Applies TruRisk™ with 25 threat intelligence sources and MITRE ATT&CK® mapping to highlight vulnerabilities actively exploited in the wild.
- Automated remediation: Speeds risk elimination through patch deployment, mitigation workflows, and ITSM ticket generation.
- Integrated compliance and configuration assessment: Automates reporting against CIS benchmarks, PCI DSS, and other standards while reducing zero-day detection times.
- Runtime protection and software analysis: Includes runtime software composition analysis, certificate inventory, and correlation of CVEs to deployed software.

4. Rapid7 InsightVM

Rapid7 InsightVM provides a vulnerability management solution for dynamic IT environments. It combines continuous asset discovery with AI-driven risk prioritization and threat intelligence from Rapid7 Labs to help organizations focus on the exposures that matter most. It includes integrated remediation workflows, project tracking, and extensive automation.
Key features include:
- Attack surface visibility: Offers continuous discovery and assessment across endpoints, servers, cloud environments, and containers using a unified agent or agentless scanning.
- AI-driven risk prioritization: Uses Rapid7’s Active Risk scoring model, enriched with real-world exploit data, attacker behavior, and business impact to highlight the most critical exposures.
- Integrated threat intelligence: Leverages proprietary Rapid7 Labs research and the Emergent Threat Response (ETR) program to flag high-priority CVEs and emerging risks.
- Simplified remediation: Provides actionable guidance with remediation projects, SLA tracking, and automated workflows delivered directly into IT operations tools.
- Extensive integrations: Supports over 500 native integrations, including automated patch management solutions, to accelerate risk reduction.
5. Cisco Vulnerability Management

Cisco Vulnerability Management (formerly Kenna.VM) provides risk-based vulnerability management using contextual insight and threat intelligence. It centralizes asset and vulnerability data, prioritizes remediation with data science, forecasts weaponization likelihood, and simplifies reporting.
Key features include:
- Risk-based prioritization: Uses data science and internal and external intelligence to recommend fixes that reduce risk in fewer steps.
- Predictive forecasting: Tracks vulnerability fluctuations and forecasts weaponization with up to 94% accuracy, enabling earlier remediation of high-risk issues.
- Threat intelligence breadth: Aggregates more than 19 feeds to present emerging threats, shifting trends, and an up-to-date organizational risk profile.
- Operations and reporting: Centralize vulnerability and asset data, establish self-service environments, set intelligent SLAs, and produce clear, stakeholder-friendly metrics.
- Integrations and tiers: Ecosystem integrations include Secure Endpoint, Talos, and XDR, while Advantage and Premier tiers expand measurement, enrichment, and accelerated response workflows.

6. Sysdig Secure

Sysdig Secure is a real-time cloud defense platform that applies runtime insights and AI to prioritize exploitable risks and stop threats. It combines agentless posture assessment with an agent for live telemetry, uses an attack graph to expose paths, and provides guided investigation and response.
Key features include:
- AI-powered risk prioritization: Combines runtime insights with cloud context to highlight exploitable vulnerabilities and misconfigurations that present meaningful, actionable risk.
- Runtime insights and Falco: Uses Falco-driven runtime visibility to determine what packages and services are actually in use, improving prioritization and detection.
- Attack path analysis: Maps exploitable links across resources to reveal potential lateral movement paths and blast radius for faster remediation decisions.
- Agent and agentless coverage: Provides agentless posture assessment complemented by an agent for real-time process analysis, enabling broad visibility and precise runtime telemetry.
- Real-time detections and response: Delivers real-time threat detection with guided investigation workflows to triage incidents and take response actions quickly.
- Unified inventory and search: Maintains a searchable inventory of resources, configurations, and vulnerabilities to streamline investigation and focus on active, exploitable packages.

7. CrowdStrike Falcon Exposure Management

CrowdStrike Falcon Exposure Management provides attack surface visibility across external assets, endpoints, cloud, network, OT/IoT, and shadow AI. It prioritizes vulnerabilities with agentic AI, incorporates adversary intelligence, analyzes attack paths, and automates remediation through Falcon Fusion, delivered via a single agent.
Key features include:
- Attack surface visibility: Uses active, passive, third-party discovery and internet scanning to enumerate external assets, endpoints, cloud, network, OT/IoT, and shadow AI.
- Real-time exposure assessment: Evaluates vulnerabilities, misconfigurations, and attack paths across hybrid and multi-cloud environments, with built-in security configuration assessment for major operating systems.
- AI Discovery for AI components: Identifies LLMs, agents, IDE extensions, MCP servers, and AI-infused packages, showing locations, installers, and configurations for governance and control.
- Agentic AI prioritization: Exposure Prioritization Agent validates vulnerabilities, quantifies impact, and ranks what to fix first using exploitability, asset criticality, and adversary intelligence.
- Automated workflows and response: Falcon Fusion SOAR automates playbooks, ticketing, and actions like network isolation and emergency patching using the existing single-agent deployment.
- Single-agent deployment: Delivers visibility and assessment without complex scanning infrastructure, consolidating discovery, evaluation, and remediation through the Falcon platform agent.

8. Trellix Security Platform

Trellix Security Platform is an integrated, AI-powered platform spanning endpoint, email, network, data, cloud, and security operations. It emphasizes detection and response efficacy, uses generative and predictive AI for investigations and context, and supports resilient operations across on-premises, hybrid, and cloud environments.
Key features include:
- Integrated platform coverage: Unifies capabilities across endpoint, email, network, data, cloud, and security operations within a single platform to streamline security workflows and visibility.
- Detection and response focus: Delivers high-efficacy detection and response outcomes, improving triage and investigative speed across standardized tests and operational environments.
- GenAI capabilities (Trellix Wise): Applies generative and predictive AI for detections, guided investigations, summarization, and contextualizing the broader threat landscape for security operations teams.
- Resilient architecture: Supports resilient management and operations across on-premises, hybrid, and cloud deployments to maintain continuity under diverse infrastructure constraints.
- Ecosystem integrations: Connects with numerous external tools through platform integrations, enabling data sharing and coordinated actions across heterogeneous security stacks.
- Operational efficiency: Designed to reduce operational burden in security operations centers by saving analyst time on triage, scoping, and assessment per alert.

9. SentinelOne Singularity Vulnerability Management

SentinelOne Singularity Vulnerability Management discovers unknown assets, continuously assesses application and operating system exposures, and prioritizes remediation by likelihood of exploitation and business criticality. It leverages existing agents, augments with network discovery, and supports isolation and automated workflows to reduce risk.
Key features include:
- Continuous assessment: Provides continuous visibility into vulnerabilities across applications and operating systems on Windows, macOS, and Linux endpoints.
- Intelligence-driven prioritization: Ranks exposures using environmental factors, business criticality, and likelihood of exploitation to focus remediation where it has the greatest impact.
- Asset and network discovery: Combines passive and active scanning to fingerprint devices, including IoT, and uncover unknown or unmanaged assets across networks.
- Leverages existing agents: Uses existing SentinelOne agents for deployment in minutes without additional hardware, reducing complexity compared to traditional network scanners.
- Automated controls: Isolates suspicious devices, closes agent coverage gaps automatically, and streamlines workflows to contain risk and maintain comprehensive protection.
- Granular scan policies: Customizable network discovery policies control scanning depth and breadth, aligning coverage with organizational requirements and constraints.

10. Fortinet FortiRecon

Fortinet FortiRecon is a SaaS threat exposure management service supporting continuous programs. It monitors internal and external attack surfaces, prioritizes exploitable vulnerabilities, enriches with adversary intelligence, and includes brand protection and takedown services alongside orchestration playbooks.
Key features include:
- Attack surface management: Continuously discovers internal and external assets from an adversary viewpoint, prioritizing risks and exposures for proactive mitigation before attacks begin. Adversary-centric intelligence: Aggregates dark web, open source, and technical intelligence, including ransomware activity, leaked credentials, and threat actor insights for faster response.
- Vulnerability validation and prioritization: Prioritizes high-risk vulnerabilities and validates them using offensive tactics to focus remediation on issues most likely to be exploited.
- Brand protection and takedowns: Detects impersonation risks, fake domains, rogue mobile apps, and phishing campaigns, with takedown services coordinated through FortiGuard Labs.
- Security orchestration: Integrates SIEM and SOAR to correlate risk and threat intelligence and automate response through inbuilt and custom playbooks.
- Supply-chain monitoring: Tracks vendor exposure, leaked data, and ransomware incidents to inform supply chain and third-party risk assessments within programs.

Source: Fortinet
11. Palo Alto Networks Cortex Cloud

Cortex Cloud 2.0 highlights a code-to-cloud approach, with Prisma Cloud securing applications from design to runtime. It prioritizes and eliminates risks across code, build pipelines, infrastructure, and runtime using AI-powered analysis, with capabilities spanning SCA, IaC, CSPM, CIEM, agentless scanning, and runtime protection.
Key features include:
- Code security: Addresses risks in code with software composition analysis, secrets scanning, IaC security, and CI/CD protections to prevent issues before deployment.
- Cloud posture and entitlements: Provides cloud security posture management, API visibility, and cloud infrastructure entitlement management for hardened configurations and least-privilege access.
- Agentless workload scanning: Performs agentless workload scanning to assess infrastructure and images, enabling rapid coverage without deploying additional endpoint components.
- Runtime protection: Detects and blocks active attacks with runtime controls including host, serverless, and web application and API security capabilities.
- AI-powered risk insights: Uses AI-powered prioritization to analyze blast radius from at-risk assets and guide investigations and response actions across the lifecycle.
- Copilot assistance: Prisma Cloud Copilot enables conversational analysis across code to cloud data, surfacing answers and recommended fixes without specialized expertise.

12. Netskope One

Netskope One is a cloud-native platform unifying SASE components with a Zero Trust Engine and the NewEdge private network. It delivers converged SWG, CASB, ZTNA, FWaaS, and SD-WAN with continuous adaptive trust, emphasizing visibility, real-time data and threat protection, and performance.
Key features include:
- Zero Trust Engine: Implements continuous adaptive trust using risk telemetry for users, data, devices, and applications, enabling precise, context-driven policy decisions.
- Unified SASE components: Consolidates secure web gateway, CASB, ZTNA, cloud firewall, and SD-WAN under one engine, client, gateway, network, and console.
- AI-powered visibility and protection: Decrypts and decodes cloud, SaaS, and web activity, applying patented AI for data and threat protections across vectors.
- Granular data protection: Provides cloud-delivered DLP with thousands of data identifiers and AI/ML techniques to classify and control sensitive information.
- Performance and reach: Uses the NewEdge private cloud with many regions and peerings to minimize latency and improve user-to-app experience globally.
- Single-pass inspection: Performs single-pass traffic inspection to reduce latency while maintaining availability and consistent policy enforcement across services.

Conclusion: Vulnerability Management Tools and Beyond
Vulnerability management tools benefit most from continuous asset visibility, risk-based prioritization and integrated remediation workflows. When these tools combine threat intelligence, clear reporting and automation, they cut noise, focus effort on material exposures and support consistent, measurable risk reduction across changing environments.
In practice, vulnerability management tools are only effective if they fit into real workflows. The strongest vulnerability management tools integrate with existing IT and security systems, help teams understand who owns each issue and provide clear next steps to resolve it.
This turns long scan reports into accountable work, shortens exposure windows and makes vulnerability management a repeatable, outcome-driven practice rather than a periodic checkbox.
Related content: Read our guide to setting up your vulnerability management program














