“Bad news, early” is a common business mindset designed to communicate urgency behind the need to identify small problems before they become big problems.
In IT security, this mindset is a way of life. Visibility into risk is never too soon, and with the number of internet-facing assets growing at an astronomical rate – for example, IDC reports that by 2023 over 500 million digital apps and services will be developed and deployed using cloud-native approaches – even a well-staffed IT security team will be kept busy trying to keep up.
To understand risk amidst constant change, IT security teams are turning to external attack surface management (EASM) tooling for early visibility and a path to lower risk.
Good EASM technologies make asset discovery, attribution/classification, testing and prioritization simple for its users. Behind the scenes, however, extensive automations, complex decision trees, global infrastructure, and integration with high-value data feeds are necessary in order to maintain pace with threats and assets. The CISA Known Exploited Vulnerabilities Catalog is a valuable tool in this regard.
[New to EASM? We recommend reading the blog series Principles of Attack Surface Protection, written by Rob Gurzeev, CEO and Co-founder of CyCognito.]
The CISA Known Exploited Vulnerabilities Catalog
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), a United States federal agency under the U.S. Department of Homeland Security, continuously updates a database of exploited vulnerabilities which it makes available online.
This living list, curated by the CISA, contains only those CVEs with evidence of active exploitation. While this list is mandatory only for Federal Civilian Executive Branch (FCEB) agencies, organizations are strongly encouraged to download this catalog and use it to compare against their own as a means of reducing risk:
“The CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice.”
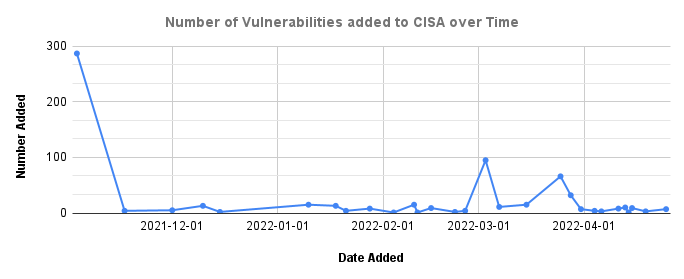
The catalog was first introduced November 3, 2021 with 287 entries and has grown to 624 entries as of April 11, 2022. The catalog is updated at a cadence based on threat activity, often multiple times per month.
For example, on March 3rd, ninety-five entries were added and on March 24th, sixty-six more were introduced, bringing the total count added in 2022 so far to 313, more than doubling the size of this valuable source of threat intelligence. It will continue to grow.
CyCognito adds the CISA known exploited vulnerabilities catalog to its platform
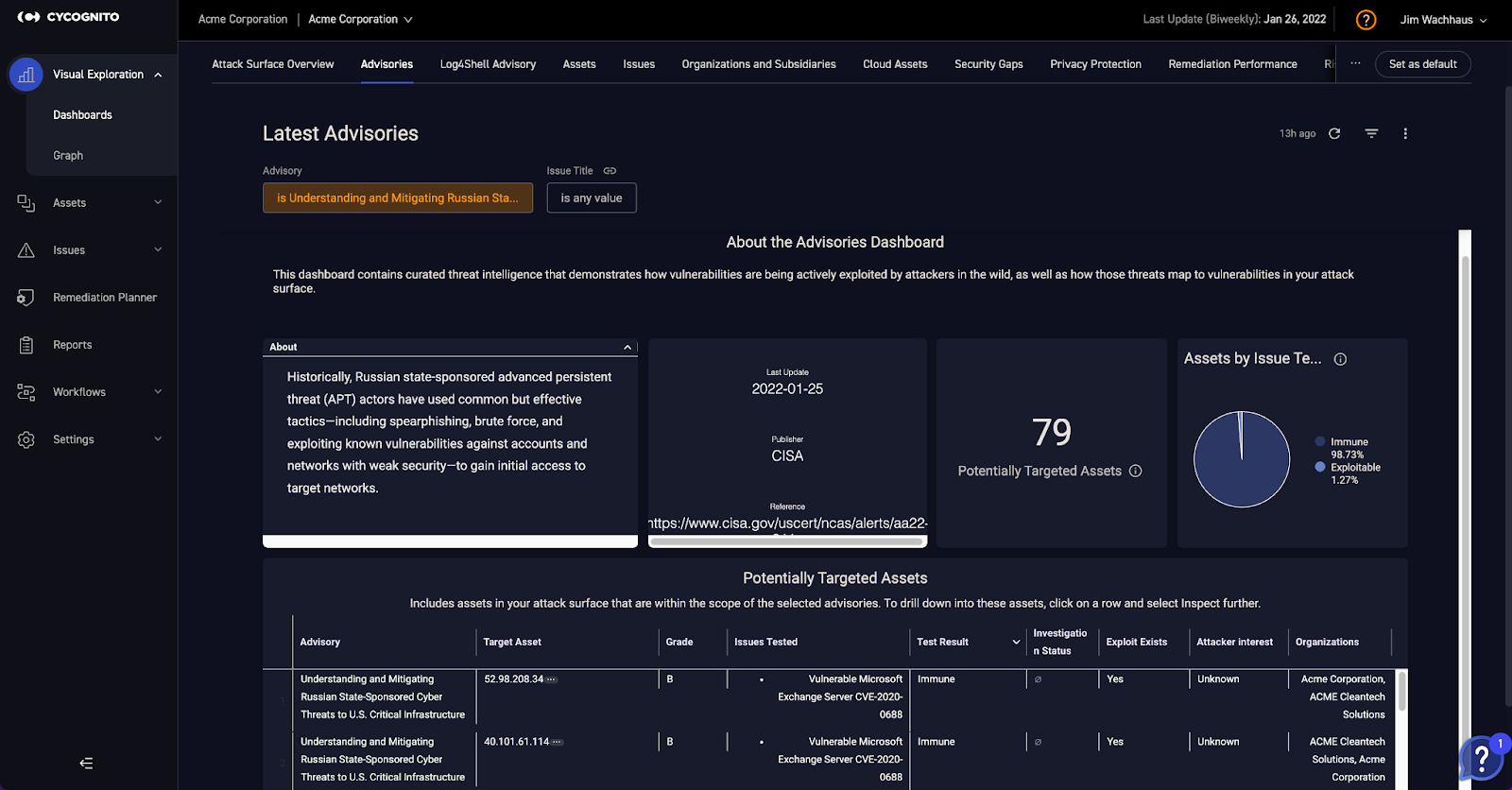
We are pleased to announce that the CyCognito platform operationalizes the CISA known exploited vulnerability catalog within its platform. Data from the catalog is used during assessment and prioritization phases to understand asset risk and assign urgency to issues.
CISA known exploited vulnerabilities can be accessed through the advisories dashboard in the CyCognito console. In the figure below, the CyCognito platform lists assets potentially affected by CISA Alert (AA22-011A) “Understanding and Mitigating Russian State-Sponsored Cyber Threats to U.S. Critical Infrastructure.
Operationally, insight from this new feed enables your incident response teams early opportunity to tactically disrupt and block instead of recover. Consumers of the CyCognito platform automatically benefit from this new integration – there isn’t a feature to configure and ongoing administrative maintenance isn’t required.
The CISA known exploitable vulnerability catalog is the latest of many intelligence sources used by CyCognito to develop asset risk scores, including those from NSA, MITRE, FBI and CISA. For example, MITRE ATT&CK Tactics and Techniques are often displayed as part of CyCognito Exploit Intelligence to assist in communicating how adversaries may use a particular exploitable vulnerability, in this case, initial access and lateral movement.
[For more information on the use of CyCognito Exploit Intelligence, see our blog here]
Lower your risk with CyCognito
Cybercriminals continuously adjust their approach to achieve their goal. Having a tool that operationalizes CISA exploited vulnerability recommendations – as they apply to your environment – is an important way to maintain pace with threats.
CyCognito’s automated asset discovery, attribution, and testing, coupled to advisories such as those from CISA, greatly improves overall awareness and significantly reduces the opportunity for an attack to be successful. This reduces manual, error prone workflows and helps your staff focus on the job at hand.
CyCognito allows customers to discover exposure, address security gaps timely, and operate efficiently. To learn more about CyCognito’s approach to attack surface management please watch our demo video.
Jason Pappalexis has worked in cybersecurity for nearly two decades, holding roles across government security administration, third-party testing, solutions architecture, product management, and technical product marketing.