If asked, “How often do you test your external attack surface,” a common response is the frequency of vulnerability scans. There are significant technical differences between scanning and testing, but the words are often used interchangeably. At what cost?
Active Testing vs. Passive Scanning
Active testing involves repeated interactions with a digital asset to reach success criteria defined by a test methodology. Active testing can be human-led, using multiple tools, with each test an evolution from the prior step. Active testing can also be automated, where the testing engine sends a payload to the asset at a pre-determined schedule and scope. The payload defines the success and all the steps needed to complete the test.
Active testing, including application security (for example, dynamic application security testing, or DAST), provides more risk insight, at a higher confidence, than software-version-based vulnerability scanning (also called “passive scanning”). Let’s look at some examples.
Passive scanning lacks depth and leaves many uncertainties. For instance:
- You appear to have Apache 2.2.3 and, therefore, are potentially vulnerable to CVE-123-4567
- You have RDP exposed on the internet
- You support RC4 ciphers
- You don’t know if your Apache configuration is susceptible to log4j
Active testing provides validated results that uncover complex risks:
- You have a system that has been actively verified as vulnerable to BlueKeep
- You scan your cloud services, classify an exposed asset as an email server, and find it has a broken authentication mechanism and a bypassable vulnerability
- You have a system verified as vulnerable to Log4J
- Your exposed web application does not have input restrictions, is susceptive to injection attacks like XSS and SQLi
- You are exposing a web index that includes sensitive files (financial, PII, confidential, etc.)
Night and day difference. Active testing verifies vulnerabilities are present, not just assumes them from the software version.
Active testing is the minimum level of risk detection and confidence your organization requires. But it can be difficult to accomplish at scale, even with most automated tools. Why? Let’s talk about that.
Internal Scanning Approaches Aren’t Enough for the External Attack Surface
The external attack surface is complex and constantly changing. However, many organizations take legacy internal scanning approaches and apply them “from the outside.” Periodic vulnerability scans across known IP segments and annual pen testing of critical web applications may be useful within internal networks but aren’t nearly the frequency, coverage, or depth for externally exposed assets.
Some organizations see the deficiencies in this approach and purchase a legacy external attack surface management (EASM) solution, perhaps one tied to a bundled offering from a large security vendor. Unfortunately, nearly all of these EASMs use basic scanning techniques to both “find” assets and identify software-version-based vulnerabilities. The initial excitement of finding a new asset with a vulnerability quickly subsides as it becomes apparent that the lack of validated risk insight, high false positives, and volume of missed assets are not saving time nor helping reduce risk.
Challenges with Risk Detection on the External Attack Surface
The 2023 Verizon Data Breach Investigations Report (DBIR) states your external attack surface represents the most targeted attack vector. To have any hope to maintain pace with risk, your organization needs more than a list of some assets with unpatched software. You need active test results across your full external asset inventory.
But it’s difficult. The external attack surface is a complex ecosystem that changes frequently. Before you can test, you first need to set the foundation with a list of assets and relevant context. This forms the first set of challenges:
- Finding the assets to test – This critical step has a ripple effect on the success of an entire external risk program. In order to minimize unknowns, you need a tool that first dynamically maps your business structure and then automatically uncovers assets within it.
- Building the asset context – Once the asset is in your inventory, you need to uncover its purpose and location within your ecosystem. Classifying an asset’s purpose and ownership can take 4-10 hours alone. A tool that automatically classifies assets and identifies the location provides significant time savings.
Once the asset inventory is built, the next set of challenges begins:
- Choosing the right test payload – Applying the wrong tests wastes time and resources. You need a tool that will dynamically build payloads on a per-asset basis.
- Scheduling tests – Active testing can create high traffic if not managed carefully. To minimize impact, organizations either test non-production systems or carefully schedule the testing of production systems. The best answer is a tool that doesn’t require manual scheduling or policy development and can be run on production systems.
- Managing asset resource impact – This is a big one. Even with careful scheduling, active tests can consume resources if not handled properly. A “low and slow” approach to active testing tied to careful monitoring of resources is essential.
Legacy testing tools often require extensive effort to crawl websites, build test policies, schedule, and monitor. Active testing, performed automatically, continuously, and without resource impact, is the clear path forward.
CyCognito – Actively Test Your Full External Attack Surface Without Legacy Challenges
CyCognito solves the challenges of active testing across your external attack surface. First, we integrate our security testing engine with our asset inventory engine. This removes coverage gaps, eliminates delay, and allows our testing engine to tailor tests per asset. We then carefully perform the testing using a proprietary network of over 60,000 nodes spread across 100 countries. Resource impact levels are monitored carefully, including both load (“bandwidth”) and depth (the number of interactions), even for basic user actions such as fetching a homepage.
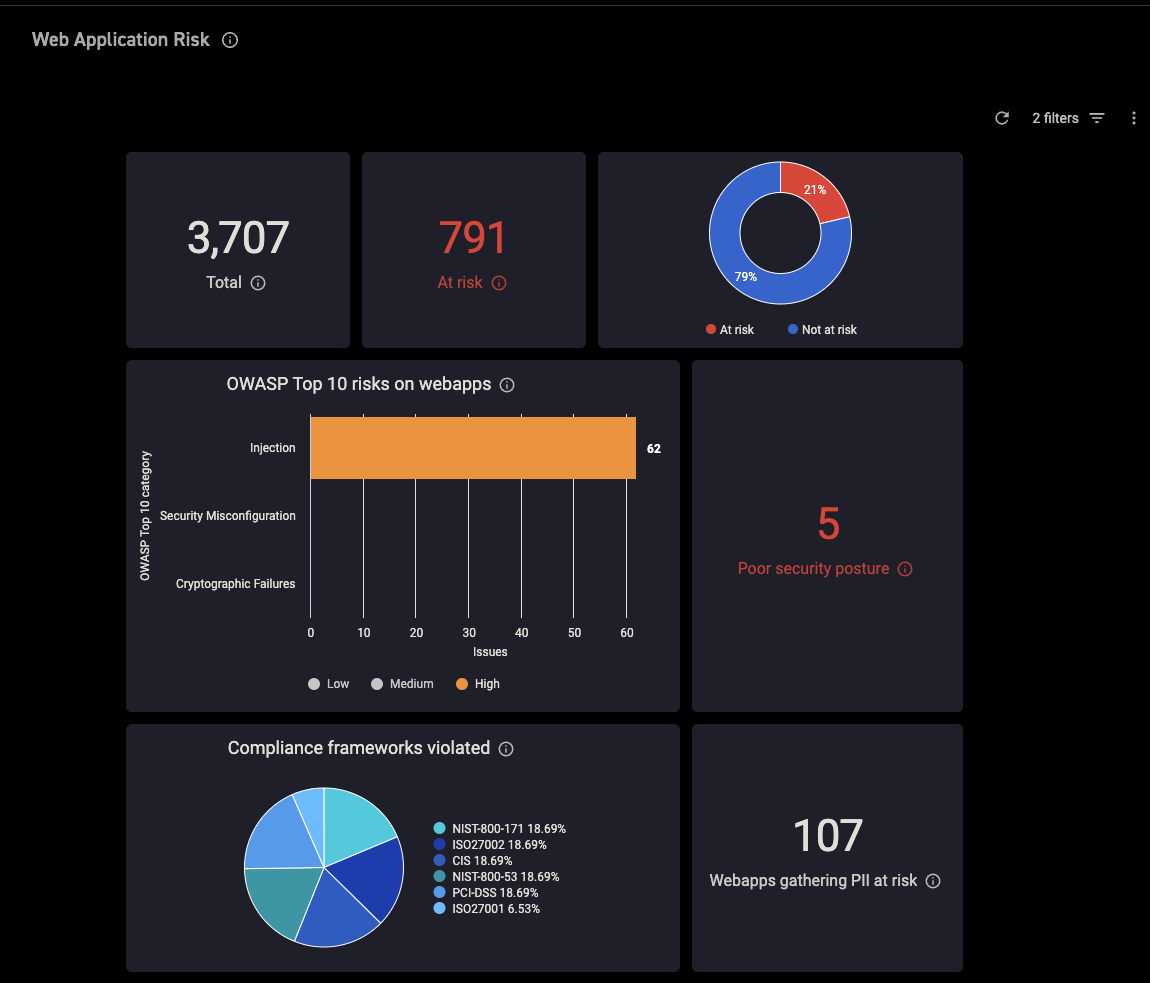
Figure 1 is a snapshot of the CyCognito Web Application Risk dashboard. The upper left is the total number of applications, which, when clicked, redirects to the web applications that make up the dataset. The middle graphic presents OWASP Top 10 results, which in this example, illustrate a high risk of injection attacks.
Figure 1: CyCognito Web Application Risk Dashboard
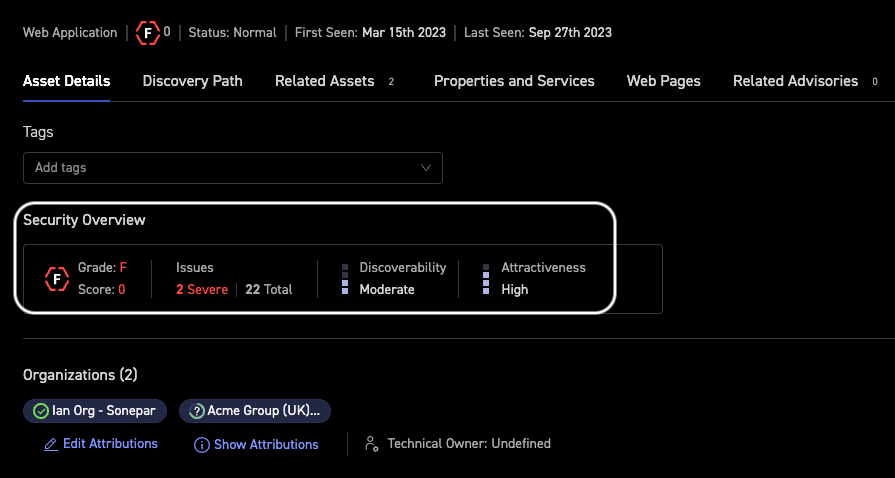
Figure 2 illustrates test insight available within the asset itself. CyCognito provides immediate visibility into security and risk posture, including an overview, security grade, number of issues, and unique CyCognito context “Discoverability” and “Attractiveness”.
Figure 2: Asset Details for a High Risk Web Application
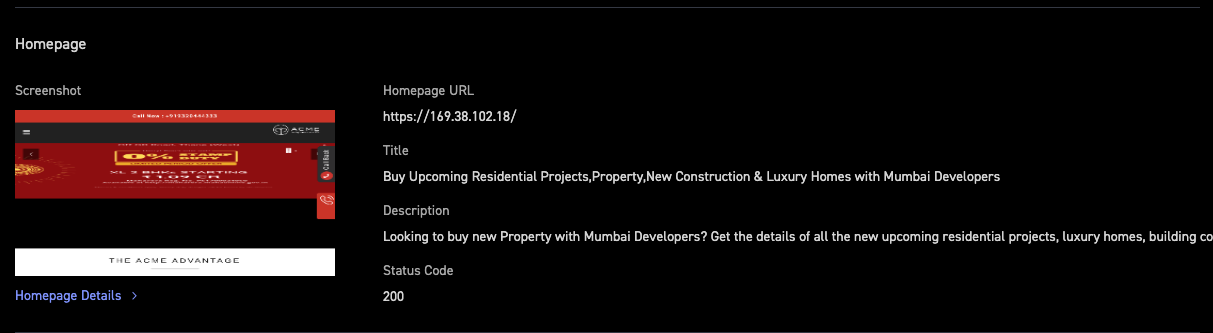
Evidence is crucial for any IT Security Team. CyCognito captures screenshots of all web applications, regardless of risk posture, along with relevant metadata. An example is provided in Figure 3.
Figure 3: Example of Web Application Screenshot with Metadata
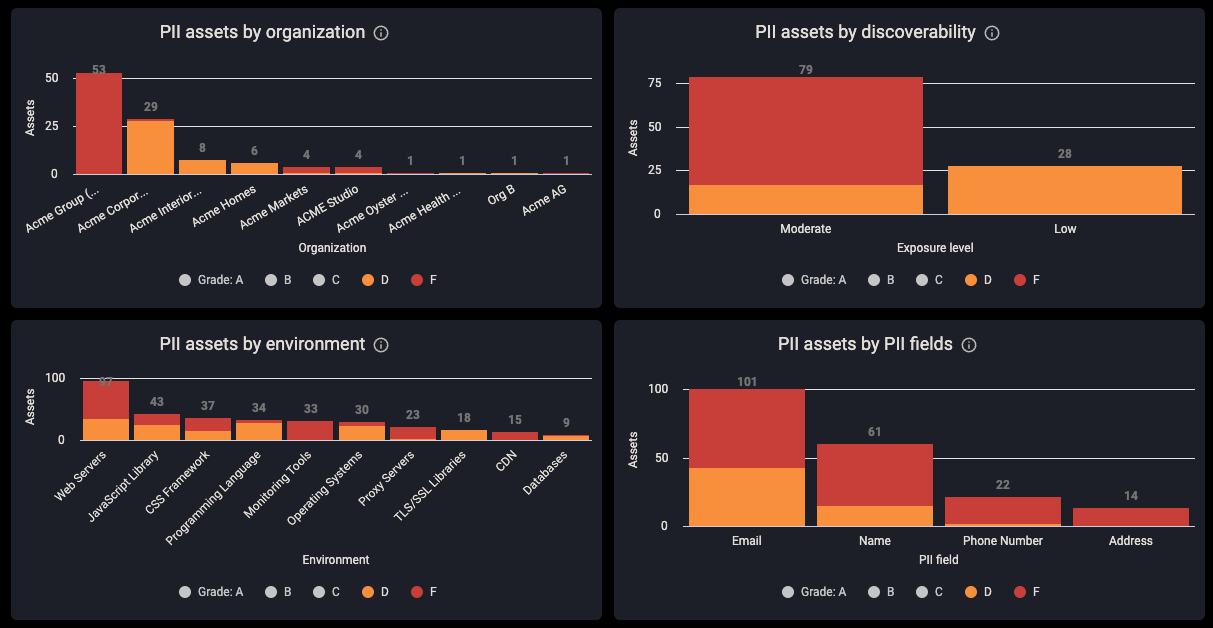
PII exposure is a concern for any organization. CyCognito active testing uncovers PII-based issues and includes a dashboard for PII risk, illustrated in Figure 3. On this dashboard, assets with PII are listed by organization (upper left), by discoverability (upper right) and even by field type (center right) are included. All data can be inspected further, directly through the dashboard.
Figure 3: PII Exposure Dashboard
Find Out More
The CyCognito platform provides comprehensive active testing, including DAST, without legacy complexities. Delivered as a SaaS, with no hardware or virtual instances to manage, policies to create, or assets to import, the CyCognito platform has low operational complexity and a high frequency of tests required for enterprise scale.
Looking for more information on how CyCognito uniquely solves external risk management challenges? Please read our Security Testing Technical Datasheet. If you are not a CyCognito customer and want to find out more about CyCognito and how we can help reduce your external risk using active testing, please contact us.
Jason Pappalexis has worked in cybersecurity for nearly two decades, holding roles across government security administration, third-party testing, solutions architecture, product management, and technical product marketing.









 Attack Surface
Attack Surface