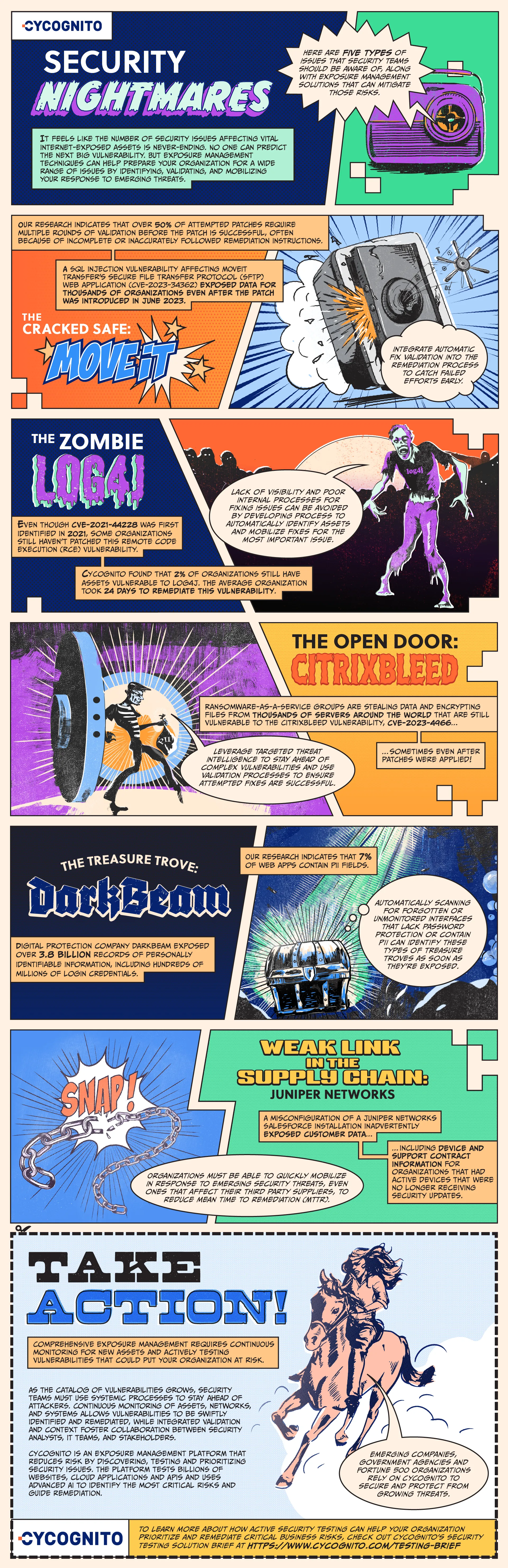
It feels like the number of security issues affecting vital internet-exposed assets is never-ending. No one can predict the next big vulnerability. But exposure management techniques can help prepare your organization for a wide range of issues by identifying, validating, and mobilizing your response to emerging threats. These processes also include validating fixes and issues, a well-documented mobilization process, and automatic scanning for high value assets.
Here are five types of issues that security teams should be aware of, along with exposure management solutions that can mitigate those risks.
The Cracked Safe: MOVEit
Issue: A SQL injection vulnerability affecting MOVEit Transfer’s secure file transfer protocol (SFTP) web application (CVE-2023-34362) exposed data for thousands of organizations even after the patch was introduced in June 2023. Our research indicates that over 50% of attempted patches require multiple rounds of validation before the patch is successful, often because of incomplete or inaccurately followed remediation instructions. If organizations are not automatically validating fixes, sensitive assets may be left unpatched for months or years.
Solution: Because remediation processes can be complex and evolve as new details about issues are discovered, organizations must automate the remediation review process in order to maintain pace.
The Zombie: Log4J
Issue: Even though CVE-2021-44228 was first identified in 2021, some organizations still haven’t patched this remote code execution (RCE) vulnerability. CyCognito found that 2% of organizations still have assets vulnerable to Log4J. The average organization took 24 days to remediate this vulnerability.
Solution: Unpatched assets linger on the attack surface for two primary reasons: lack of awareness of the asset and poor internal processes for fixing issues. Security teams must develop automated processes to identify all assets and then to mobilize fixes on the most important issues. Without it, they will find themselves falling victim to these zombie vulnerabilities long after they’re out of the news.
The Open Door: CitrixBleed
Issue: Thousands of servers around the world remain vulnerable to the CitrixBleed vulnerability, CVE-2023-4966, sometimes even after patches were applied. Affiliates of the Ransomware-as-a-Service group Lockbit 3.0 and AlphV/BlackCat have leveraged this vulnerability to compromise Fortune 100 organizations and financial institutions, stealing data and encrypting files.
Solution: Vulnerabilities with this level of impact require targeted threat intelligence to stay informed as the situation evolves, as well as processes that validate if attempted fixes were successful.
The Treasure Trove: DarkBeam
Issue: An unprotected Elasticsearch and Kibana interface belonging to the digital protection company DarkBeam exposed over 3.8 billion records of personally identifiable information (PII) in September 2023, including hundreds of millions of login credentials. Our research indicates that 7% of web apps contain PII fields and could potentially expose PII .
Solution: Automatically scanning for forgotten or unmonitored interfaces that lack password protection or contain PII can identify these types of treasure troves as soon as they’re exposed.
Weak Link in the Supply Chain: Juniper Networks
Issue: When Juniper Networks misconfigured their Salesforce installation, they not only exposed their own data, but also put their customers’ data at risk. This error allowed attackers to identify device and support contract information for organizations that were no longer Juniper customers but still had active devices, indicating that those devices were no longer receiving security updates.
Solution: Organizations must be able to quickly mobilize in response to security issues that affect not only themselves but also their third party suppliers or their third party’s third party. Security teams also need prompt awareness of devices that are no longer receiving security updates so that they can be taken offline or otherwise protected from attackers. A well-implemented mobilization process reduces friction between impacted IT security teams and accelerates MTTR.
Take Action
Comprehensive exposure management requires continuous monitoring for new assets and actively testing vulnerabilities that could put your organization at risk.
As the catalog of vulnerabilities grows, security teams must use systemic processes to stay ahead of attackers. Continuous monitoring of assets, networks, and systems allows vulnerabilities to be swiftly identified and remediated, while integrated validation and context foster collaboration between security analysts, IT teams, and stakeholders.
CyCognito is an exposure management platform that reduces risk by discovering, testing and prioritizing security issues. The platform tests billions of websites, cloud applications and APIs and uses advanced AI to identify the most critical risks and guide remediation. Emerging companies, government agencies and Fortune 500 organizations rely on CyCognito to secure and protect from growing threats. For more information, visit cycognito.com/demo.
Emma Zaballos is an avid threat researcher who is passionate about understanding and combatting cybercrime threats. Emma enjoys monitoring dark web marketplaces, profiling ransomware gangs, and using intelligence for understanding cybercrime.