Every organization must prioritize the security of its systems and the protection of its customers’ sensitive information, but exposure doesn’t only happen through applications your own team develops and controls. Incidents like the recent exposure of customer data by Juniper Networks serve as stark reminders of the challenges and risks associated with managing the exposure of software, hardware, and services that you use. This incident, caused by inadvertent data exposure stemming from a support portal upgrade, highlights the critical importance of robust exposure management protocols in preventing such incidents.
Juniper Networks is a prominent vendor of networking equipment used by some of the world’s largest organizations. Due to a Salesforce misconfiguration, their website was inadvertently exposing sensitive information tied to customer products. The exposure included details such as which devices customers bought, warranty status, service contracts, and serial numbers, potentially exposing customers to security risks by revealing which products lacked critical updates.
How Could This Misconfiguration Be Exploited?
A savvy attacker could use this vulnerability to extract a list of targets who had once been Juniper customers but had ended their licenses, potentially leaving existing Juniper devices unpatched and vulnerable to exploitation.
Many breaches stem from unknown vulnerabilities or misconfigurations that never receive extensive attention. Organizations are left guessing as to how attackers gained access to a network, but the damage that’s done can last for years.
Other Misconfigurations Attackers Can Leverage
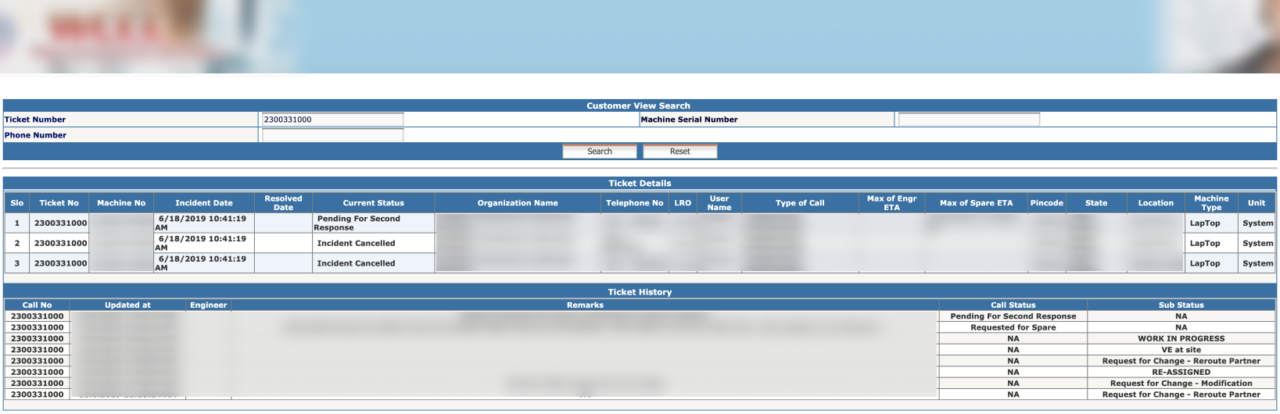
Misconfigurations like the exposed call center ticketing system shown in Figure 1 underscore the importance of effective exposure management in preventing unauthorized access to sensitive data. Exposure management involves identifying, assessing, and mitigating risks associated with the exposed digital assets. By implementing robust exposure management practices, organizations can proactively identify vulnerabilities in their systems and take corrective measures before they are exploited by malicious actors.
Figure 1: An example of an exposed call center ticketing system discovered by CyCognito. Attackers could leverage this exposure to extract contact information or service records for active and past customers.
Juniper Networks is not unique. Many organizations rely on supply chain platforms such as Salesforce for its support portal backend underscores the importance of assessing and managing supply chain risks. Misconfigurations in supply chain platforms can have far-reaching consequences, as demonstrated by the widespread data leaks associated with misconfigured Salesforce installations reported in previous research. Organizations must conduct thorough assessments of vendors and implement robust security measures to mitigate the risks posed by third-party dependencies and, in the case of Juniper Networks’ customers, by your vendor’s vendors.
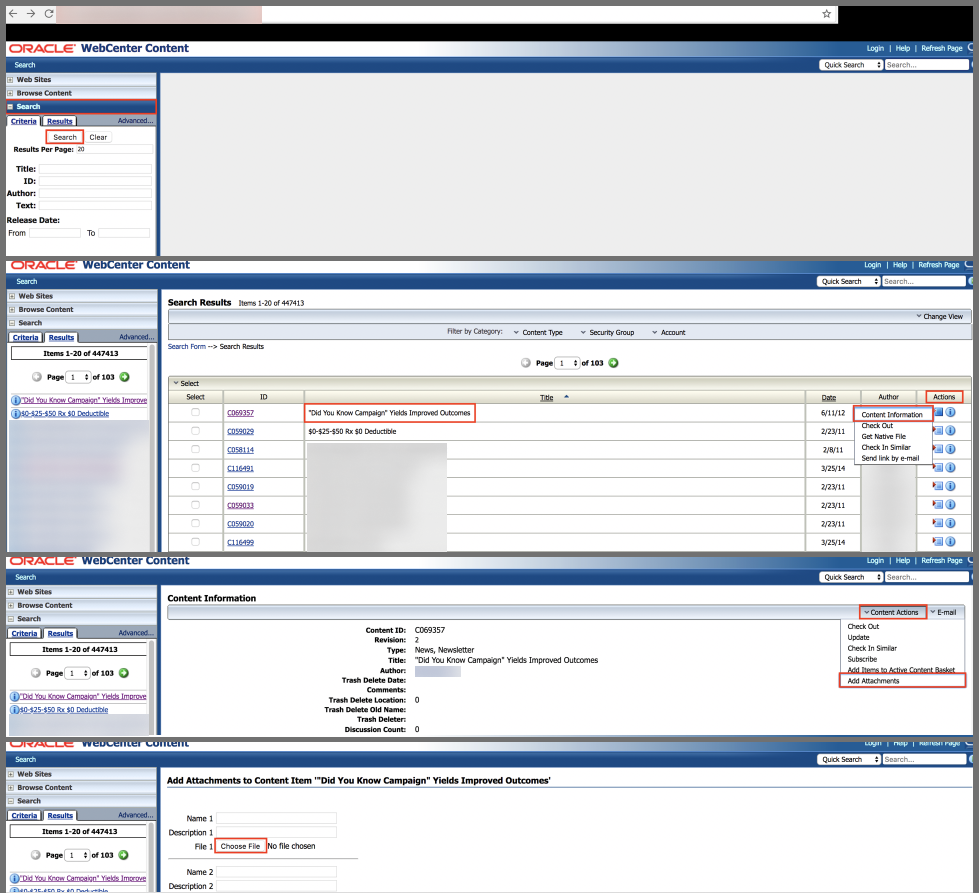
Figure 2: Because this healthcare content management system (CMS) was exposed, attackers could use the add new content feature to upload malware and send it as links to users. CyCognito identified this exposure through our zero-input discovery process.
Assets like content management systems (CMS) can provide footholds for attackers to target employees or customers. In the figure above, a red box highlights the ability for unauthorized users to add attachments as new content, while the box above it gives options to extract contact information or send attachments as links. A savvy attacker could use these features to either steal data or target other individuals inside or outside the exploited organization.
Using Exposure Management to Mitigate Security Incidents
Another critical aspect of exposure management is the timely detection and response to security incidents. Organizations must have mechanisms in place to quickly identify and investigate security incidents, mitigate the impact, and implement measures to prevent recurrence. When new information about a misconfiguration or breach comes to light, a security team must be able to quickly answer these questions:
- Are we exposed? Are any of our subsidiaries exposed?
- Are we actively testing these exposed assets every week?
- How did we validate these tests?
- What percentage of our exposed assets are being tested? Is it closer to 10% or 100%?
- Are we able to automatically prioritize the top critical attack vectors into our network, or is this based on a manual process?
- How quickly are we able to update our prioritization when new issues are discovered?
Looking ahead, organizations must continuously evaluate and enhance their exposure management practices to adapt to evolving threats and vulnerabilities. It’s no longer enough to rely on running passive scanning on a subset of networks alongside annual pentesting. To keep pace with the speed of attackers, identifying exposed assets and high priority vulnerabilities must happen constantly across the entire attack surface.
Benefits of Exposure Management
A comprehensive exposure management system continuously assesses the constellation of assets for blind spots, gathers context to classify assets, and actively tests them to validate if they are actively exploitable. The business context of the asset and testing results can be leveraged to prioritize the top issues to remediate, identifying the likeliest sources of breaches when there’s still time to mitigate them.
By adopting a proactive and comprehensive approach to exposure management, organizations can mitigate the risk of data breaches, safeguard sensitive information and reduce mean time to remediation. Focusing on high-precision testing alongside integrated validation lowers the false positive rate, saving time and fostering trust between teams as they work together to handle emerging risks.
Using exposure management to prioritize security and adopt proactive measures helps organizations protect customer data and preserve trust in an increasingly interconnected digital world.
How CyCognito Can Help
CyCognito, the leader in exposure management, provides a complete solution for identifying, prioritizing, and remediating attack surface vulnerabilities. Leveraging the latest in AI, CyCognito automatically discovers cloud and web assets within a given organization, and tests those assets to understand risk and eliminate exposure. Leading enterprises and Fortune 500 organizations, including Colgate-Palmolive, Tesco and many others, rely on CyCognito to secure and protect their attack surfaces from growing threats. Schedule a demo here.
Emma Zaballos is an avid threat researcher who is passionate about understanding and combatting cybercrime threats. Emma enjoys monitoring dark web marketplaces, profiling ransomware gangs, and using intelligence for understanding cybercrime.