What Is Qualys?
Qualys is a cloud-based security and compliance platform for vulnerability management, policy compliance, asset inventory, and other security tasks. It provides continuous visibility into on-premises, cloud, and endpoint environments by deploying lightweight agents and scanners to collect data, assess vulnerabilities, and flag misconfigurations.
The platform covers traditional servers, endpoints, cloud resources, containerized workloads, and web applications. Its modular approach enables enterprises to select services tailored to specific needs, ranging from internal network scanning to external attack surface management. Qualys integrates with SIEMs, ticketing systems, and devops toolchains to support incident response and compliance initiatives.
Qualys covers several solution categories, and competes with different vendors in each category:
- Vulnerability management: Focus on discovering, identifying, prioritizing, and assisting in the remediation of security flaws across endpoints, servers, and network devices. These platforms employ a mix of authenticated and unauthenticated scans to detect vulnerabilities, outdated software, and misconfigurations.
- Attack Surface Management (ASM): Focus on the external, Internet-facing footprint of an organization: The full set of domains, IPs, cloud assets, exposed applications, and services accessible from outside the network perimeter. ASM tools continually scan for new assets, shadow IT, expired or misconfigured SSL certificates, and leaked credentials.
- Cloud Security Posture Management (CSPM): Addresses the unique challenges of maintaining secure configurations within cloud environments such as AWS, Azure, and Google Cloud. Unlike traditional vulnerability scanners, CSPMs continuously monitor cloud resources for misconfigurations, policy violations, insecure storage permissions, compliance issues, and other exposures specific to cloud-native architectures.
- Endpoint and XDR Platforms: Modern XDR solutions include vulnerability management capabilities to provide unified visibility and response. These platforms deploy lightweight agents on endpoints (workstations, servers, and sometimes cloud workloads) to collect security telemetry, detect threats, and run vulnerability scans.
- Application security solutions: Application security solutions address vulnerabilities and misconfigurations within web applications, APIs, and microservices. These tools use techniques such as dynamic application security testing (DAST) and static analysis (SAST) to scan code and running applications for security flaws like SQL injection, cross-site scripting (XSS), authentication gaps, and insecure dependencies.
We list and review Qualys alternatives in each category in the following sections.
How to Evaluate Qualys Alternatives
When comparing Qualys with other security platforms, a head-to-head evaluation should focus on the following criteria.
- Coverage and use case fit: Start by mapping your organization’s needs, such as vulnerability management, compliance, asset inventory, detection and response, or web application scanning, to the platform’s core strengths. Some tools focus narrowly on scanning, while others provide broader platforms with risk scoring, patch management, or threat prioritization.
- Deployment model and ease of use: Evaluate whether the platform uses agents, scanners, or a hybrid model, and how easily it can be deployed across your environment, including cloud, on-premises, and remote endpoints. Consider setup complexity, maintenance overhead, and the user experience for both analysts and administrators.
- Data quality and reporting: The value of a security platform depends on the accuracy and consistency of its findings. Review how thoroughly critical vulnerabilities are detected, how false positives are handled, and how flexible the reporting options are. Dashboards should support both operational analysis and executive reporting.
- Integration and workflow automation: Security tools rarely operate in isolation. Assess how well each alternative integrates with existing SIEM platforms, ticketing systems, and cloud infrastructure. API support, native integrations, and CI/CD connectivity are important for embedding security into operational workflows.
- Cost and scalability: Pricing models vary and may be asset-based, usage-based, or feature-bundled. Review the full cost, including licenses, add-ons, and support, and evaluate how well the platform scales as the environment grows.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

Vulnerability Management Alternatives
Tenable VM

Tenable Vulnerability Management offers a risk-based approach to identifying and prioritizing vulnerabilities across IT, cloud, and hybrid environments. It continuously discovers known and unknown assets, assesses exposures, and uses enriched threat intelligence and contextual scoring to guide remediation efforts.
Key features:
- Continuous asset identification: Automatically detects assets, including dynamic cloud and remote systems, to ensure visibility.
- Risk-based prioritization: Uses Vulnerability Priority Rating (VPR) powered by threat intelligence and AI to rank vulnerabilities based on real-world risk.
- Threat contextualization: Enriches vulnerability data with research-driven intelligence to help teams understand exploitability and business impact.
- Guided remediation: Provides best-practice steps for addressing high-risk exposures and reducing cyber risk.
- Workflow integration: Supports bi-directional ticketing and integrates with security operations tools to streamline exposure response.
Rapid7 InsightVM

Rapid7 InsightVM is a vulnerability management platform for dynamic, hybrid environments. It provides continuous visibility across assets, prioritizes vulnerabilities using risk context and threat intelligence, and simplifies remediation through automated workflows.
Key features:
- Unified asset and endpoint detection: Continuously discovers assets across on-premises, cloud, and remote environments using agent-based and agentless scanning.
- Risk-based prioritization: Uses the Active Risk model to assess exploitability, attacker behavior, and business impact for better vulnerability triage.
- Integrated remediation workflows: Enables automated and trackable remediation projects with guidance delivered to IT teams.
- Live dashboards and reporting: Offers customizable views and reports for both technical teams and executive stakeholders.
- Policy and compliance support: Includes built-in policy assessments against frameworks like CIS, PCI DSS, and HIPAA.
CrowdStrike Falcon Exposure Management

CrowdStrike Falcon Exposure Management is a risk-based vulnerability management solution that combines threat intelligence, AI-driven prioritization, and continuous monitoring to help organizations reduce exposure across cloud, on-premises, and hybrid environments.
Key features:
- Unified visibility: Provides coverage across cloud, on-prem, and hybrid assets using a lightweight agent.
- AI-driven risk prioritization: Uses ExPRT.AI to identify and rank vulnerabilities based on exploitability, business context, and attacker behavior.
- Threat intelligence: Continuously correlates vulnerability data with current adversary tactics to surface active threats.
- Predictive attack path mapping: Visualizes potential lateral movement paths to prioritize vulnerabilities that enable real-world breaches.
- Infrastructure-free operation: Removes the need for separate scanning infrastructure, simplifying deployment and reducing overhead.
Notable Cloud Security and Container Security Competitors
Palo Alto Prisma Cloud

Palo Alto’s Prisma Cloud is a cloud-native application protection platform (CNAPP) that secures applications from code to runtime across multi-cloud environments. It combines capabilities like CSPM, workload protection, API security, and vulnerability scanning into a single platform.
Key features:
- Code-to-runtime security: Secures applications from development to production with support for IaC, containers, APIs, and serverless environments.
- Workload and container protection: Performs agentless and agent-based scanning of hosts, containers, and Kubernetes clusters to detect vulnerabilities and threats.
- AI-powered risk prioritization: Uses AI to assess the blast radius and impact of risks, helping teams focus on critical issues first.
- Entitlement and access visibility: Offers cloud infrastructure entitlement management (CIEM) to monitor permissions and prevent privilege misuse.
- Integrated platform: Unifies CNAPP, IT asset management, and threat intelligence into a single interface to reduce tool sprawl and operational complexity.
Orca Security

Orca Security is an agentless CNAPP that provides visibility across multi-cloud environments. It uses its SideScanning™ technology to detect vulnerabilities, misconfigurations, malware, and other risks without deploying agents.
Key features:
- Agentless deployment: Uses SideScanning™ to collect data without installing agents, ensuring visibility with minimal operational friction.
- Unified data model: Combines workload context and cloud metadata into a centralized platform for risk prioritization and investigation.
- Attack path analysis: Identifies the most critical risks by analyzing how threats can move laterally and reach high-value assets.
- AI-assisted remediation: Leverages AI to generate remediation steps and simplify response workflows across development and operations teams.
- Shift-left security: Integrates into CI/CD pipelines to detect issues in infrastructure as code (IaC) and container images before deployment.
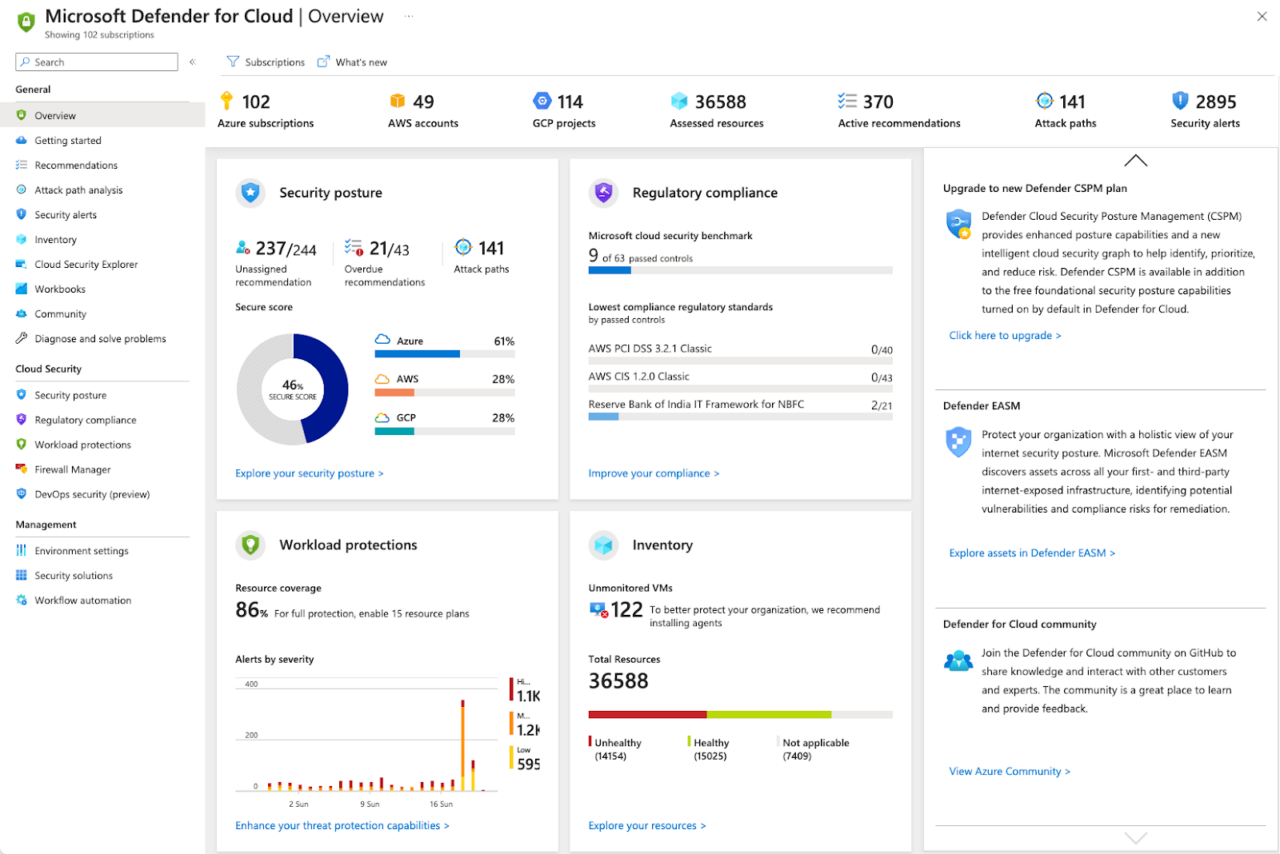
Microsoft Defender for Cloud

Microsoft Defender for Cloud is a CNAPP that provides unified security across development and runtime environments in multicloud and hybrid infrastructures. It combines cloud security posture management (CSPM), cloud workload protection (CWPP), and DevSecOps capabilities into a single platform.
Key features:
- Unified CNAPP platform: Combines CSPM, CWPP, and DevSecOps tools to secure applications from code to runtime across Azure, AWS, GCP, and on-premises environments.
- Agentless and agent-based coverage: Provides flexible deployment with agentless scanning and agent-based protection for workloads like VMs, containers, and databases.
- Integrated DevOps security management: Scans code repositories (e.g., GitHub, Azure DevOps) for IaC misconfigurations, exposed secrets, and other risks before deployment.
- AI threat protection: Detects and responds to attacks targeting generative AI workloads, and provides posture management for AI application components.
- Workload protection: Secures containers, VMs, databases, storage, and APIs with threat detection, vulnerability assessments, and runtime monitoring.
Application Security Alternatives
Invicti

Invicti offers a unified application security platform to reduce false positives, simplify vulnerability remediation, and integrate into DevSecOps workflows. Its dynamic application security testing (DAST) engine is supported by AI-powered automation and correlation across multiple sources, helping teams identify and validate exploitable vulnerabilities.
Key features:
- Dynamic vulnerability validation: Uses proof-based scanning to confirm exploitable vulnerabilities, reducing false positives.
- Automated CI/CD orchestration: Integrates with pipelines to automatically run scans, imports, and escalations without manual intervention.
- Single-pane vulnerability correlation: Consolidates and deduplicates findings from multiple sources for clear, prioritized risk visibility.
- AI-guided remediation: Provides developers with step-by-step instructions to fix issues, accelerating the remediation process.
- Dev tool integrations: Syncs with Jira, GitHub, Azure Boards, and other tools to track issues through resolution.
Rapid7

Rapid7’s InsightAppSec is a DAST solution designed to detect and prioritize vulnerabilities in web applications and APIs. Built on the Insight platform, it automates black-box testing while offering integration with development workflows to simplify remediation.
Key features:
- Dynamic application security testing (DAST): Identifies vulnerabilities in running applications using 95 attack types.
- Attack Replay: Allows developers to validate and retest fixes directly from within vulnerability reports without rerunning full scans.
- Universal Translator: Supports modern web frameworks and parses various formats (e.g., JSON, XML, JavaScript) for accurate scanning.
- Compliance reporting: Generates reports aligned with standards like PCI-DSS, HIPAA, and OWASP Top 10 to support audits and governance.
- DevOps integration: Connects with tools like Jira and CI/CD platforms to enable remediation workflows and visibility across teams.
Veracode

Veracode provides an Application Risk Management platform to secure software development workflows, including those involving AI-generated code. The platform uses AI-powered scanning and remediation capabilities to identify and address security flaws across the software development lifecycle (SDLC).
Key features:
- AI-powered code scanning: Analyzes code in hundreds of languages with low false positive rates, using AI models trained on a vast vulnerability database.
- Application Security Posture Management (ASPM): Provides centralized oversight of risk posture across applications, teams, and projects.
- Root cause analysis: Helps prioritize vulnerabilities by identifying the underlying issue and suggesting focused remediation.
- Secure software supply chain: Assesses and secures open-source and third-party components throughout the SDLC.
- AI code remediation: Offers automated fix recommendations for flaws introduced by AI-generated or manually written code.
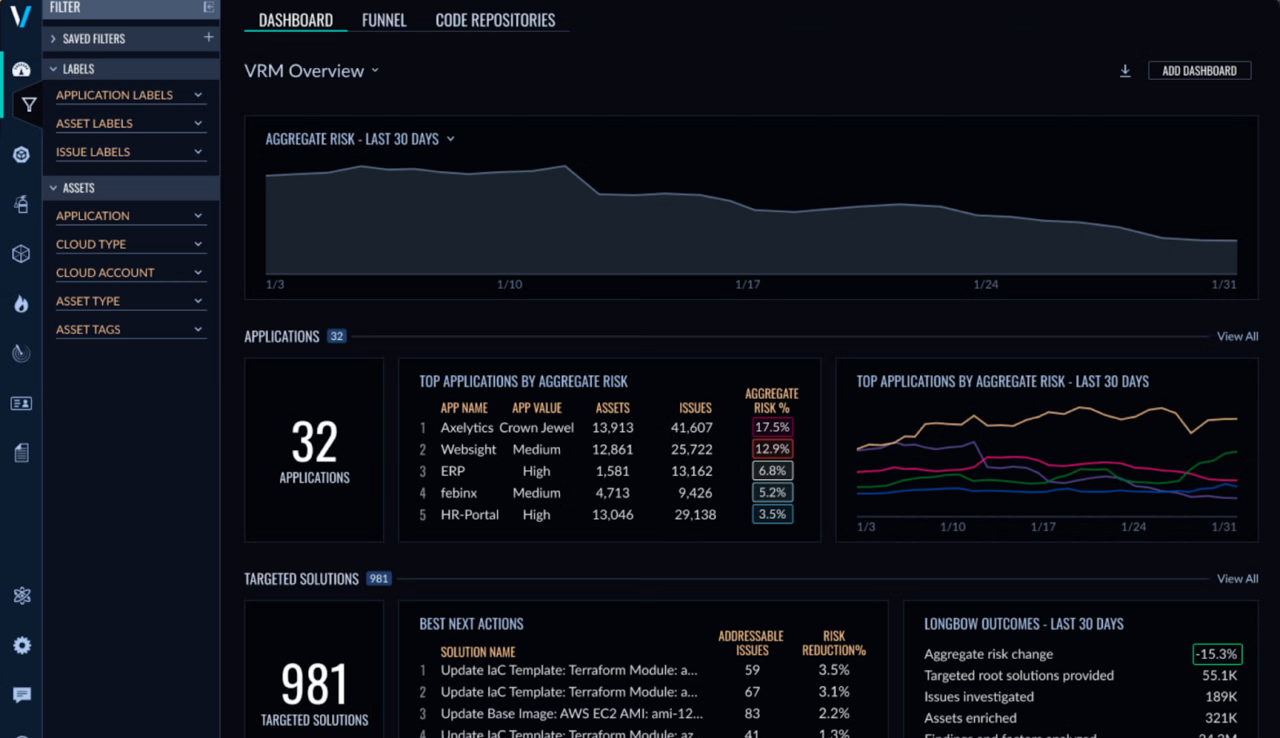
Attack Surface Management Alternatives
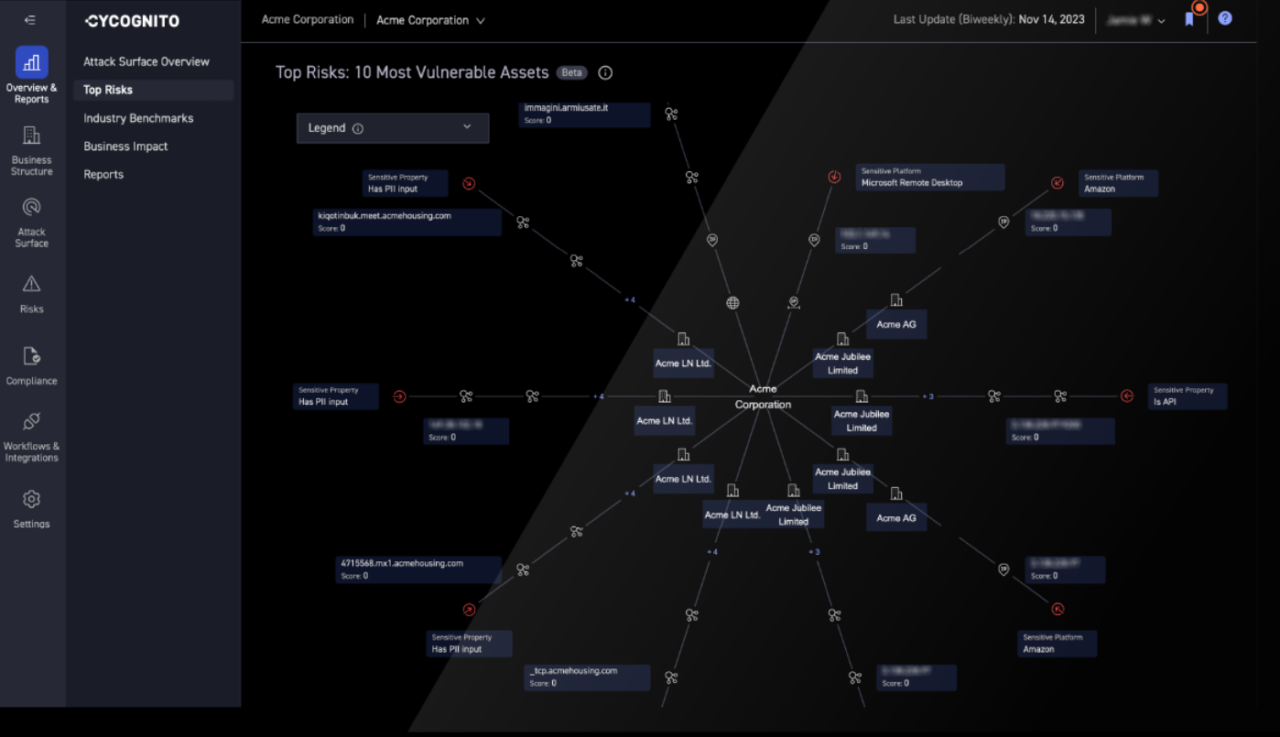
CyCognito

CyCognito is a pure-play external exposure management platform designed to discover, validate, and prioritize an organization’s externally reachable assets from an attacker’s perspective. Unlike Qualys, which extends attack surface management from a vulnerability scanning foundation, CyCognito is built specifically for external discovery and exposure analysis.
CyCognito performs continuous, seedless discovery of an organization’s external footprint by observing internet-scale signals such as DNS relationships, IP allocations, certificate metadata, and exposed services. This allows it to identify domains, subdomains, IPs, cloud infrastructure, web applications, and other externally reachable assets, including assets that are unknown, unmanaged, or omitted from internal inventories.
Key capabilities include:
- Seedless, zero-input discovery: CyCognito starts with observable internet signals (DNS, certificates, IP space) and expands outward to uncover unknown external assets automatically, rather than relying on seeded discovery approaches like Qualys.
- Broader asset coverage and ownership mapping: CyCognito continuously maps external assets across brands, subsidiaries, acquisitions, and cloud environments, providing a more complete external view than Qualys’ domain- and subdomain-centric discovery.
- Active exposure validation: CyCognito runs automated, unauthenticated tests at scale to confirm real external reachability and exposure conditions, going beyond the passive enumeration typically used in Qualys EASM.
- Risk prioritization and remediation validation: CyCognito prioritizes exposures based on attacker relevance and impact, and validates whether fixes actually reduced external exposure, an area where Qualys relies more heavily on adjacent tools and manual follow-up.
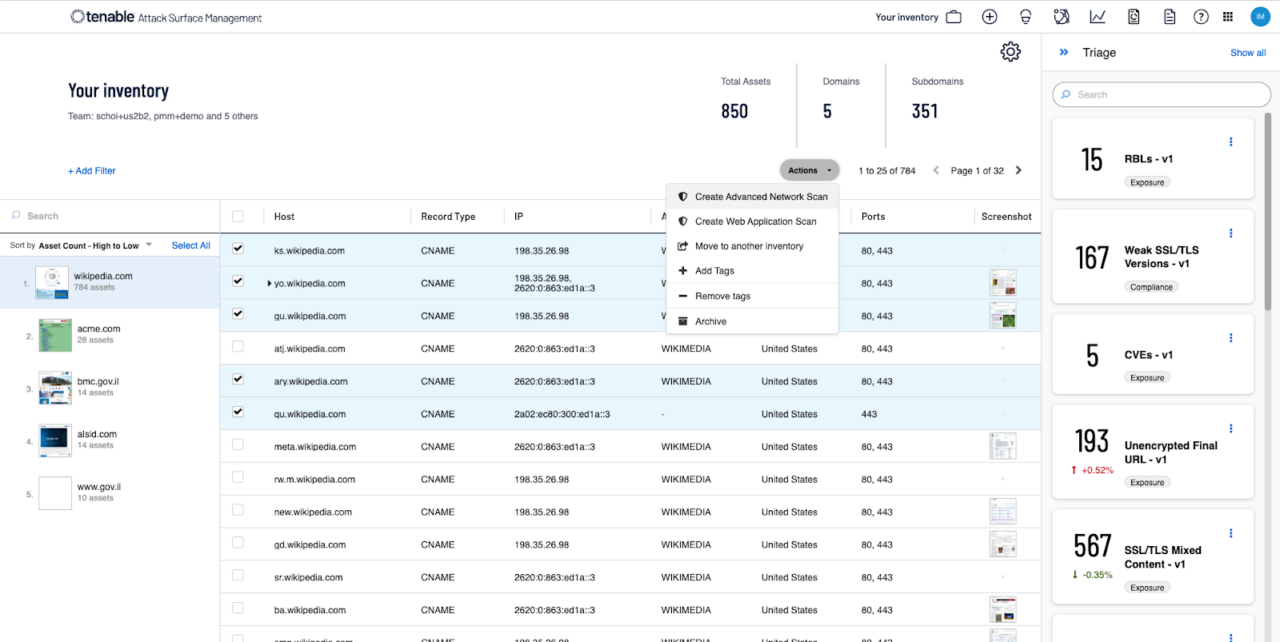
Tenable ASM

Tenable Attack Surface Management (ASM) provides continuous visibility into internet-facing assets by mapping the global internet and linking discovered assets to an organization. This helps security teams identify unknown or unmanaged systems and assess them for risk.
Key features:
- Asset discovery: Continuously scans over 5 billion internet-facing assets to detect known and unknown systems tied to the organization.
- Business context enrichment: Provides over 200 metadata fields to help prioritize assets based on relevance and exposure.
- External risk assessment: Integrates with Tenable’s security platforms to scan newly discovered assets and eliminate blind spots.
- Continuous monitoring: Tracks changes in the external footprint and alerts teams to new risks as they appear.
- Use-case coverage: Supports cybersecurity, compliance, brand protection, mergers and acquisitions, and legal exposure assessments.
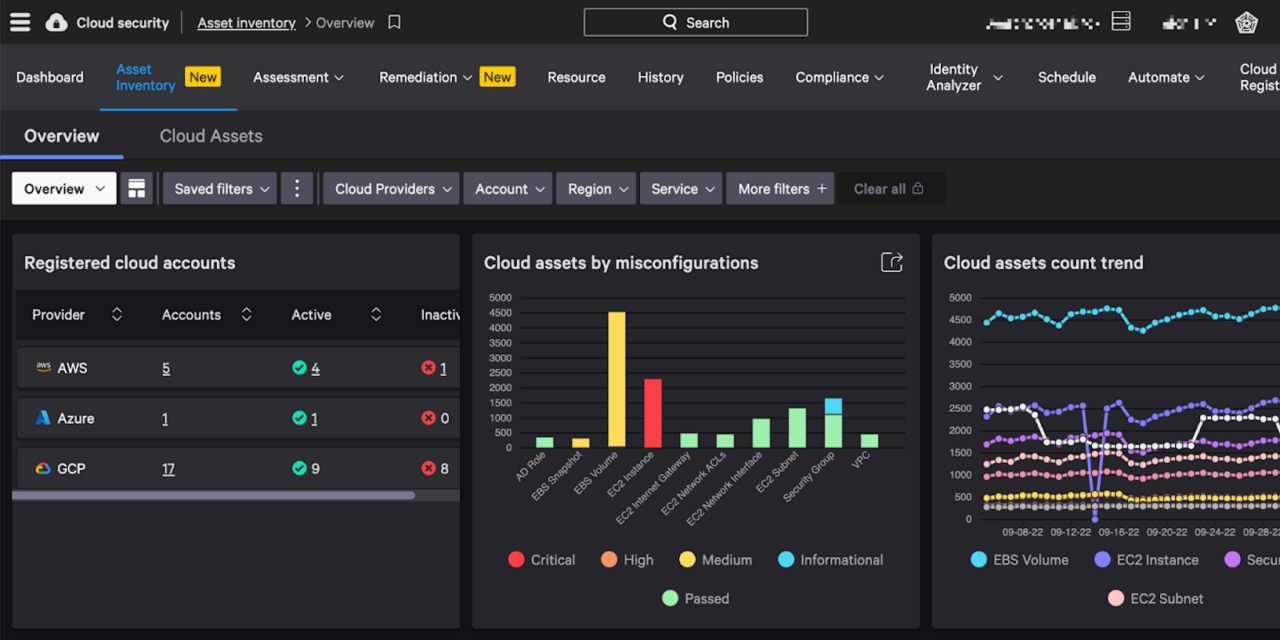
CrowdStrike EASM

CrowdStrike External Attack Surface Management (EASM) provides visibility into internet-facing assets, helping organizations uncover shadow IT and reduce risk from unknown exposures. Using continuous internet-wide scanning and AI-driven risk prioritization, it enables security teams to quickly identify and address threats from an attacker’s perspective.
Key features:
- Discovery of unknown assets: Identifies shadow IT and unmanaged internet-facing systems for attack surface visibility.
- Continuous scanning and monitoring: Maps and monitors the internet in real time to detect exposures and changes.
- AI-driven prioritization: Uses ExPRT.AI to rate vulnerabilities and guide remediation based on adversary tactics.
- Integrated threat intelligence: Combines asset data with attacker insights to prioritize the most relevant threats.
- Falcon platform integration: Unifies EASM with CrowdStrike’s IT hygiene, vulnerability, and threat management capabilities.
Final Thoughts
Qualys competes in a broad and increasingly fragmented security landscape that spans exposure management, cloud security, data security, application security, endpoint protection, and attack surface management.
Evaluating alternative security tools requires understanding which problem you are trying to solve and how deeply each platform aligns with your environment, workflows, and maturity level. Some competitors specialize in depth within a single domain, while others offer a unified security platform that trades specialization for consolidation.















