Threat hunting tools are crucial for proactively identifying and mitigating cyber threats. These tools leverage techniques like advanced analytics, machine learning, and threat intelligence to detect anomalies and potential malicious activities before they escalate into significant security incidents.
Here’s a breakdown of some main categories and examples of security monitoring tools used for threat hunting:
- Endpoint Detection and Response (EDR): EDR solutions provide deep visibility into endpoint activity, enabling threat hunters to investigate potential compromises and malicious behavior.
- Network monitoring tools: Tools like Wireshark and tcpdump help analyze network traffic for suspicious patterns and anomalies.
- Security Information and Event Management (SIEM): SIEM systems aggregate and analyze security logs from various sources, offering a centralized view for threat detection and response.
- External Attack Surface Management (EASM): These solutions help continuously discover, monitor, analyze, and secure a range of exposed to the internet, helping identify external vulnerabilities that may be exploited by threat actors.
What Are Threat Hunting Tools?
Threat hunting tools are used by cybersecurity teams to proactively search for, identify, and mitigate potential threats that evade traditional security measures. Unlike passive security solutions that rely on alerts and known threat signatures, these tools empower analysts to explore their environments for unknown, novel, or stealthy attacks. They enable teams to move beyond simple detection and to actively scrutinize system behaviors, network activity, and endpoint events for signs of compromise or emerging attack techniques.
The approach taken by threat hunting tools is rooted in the assumption that adversaries may bypass automated defenses and dwell unnoticed within systems. By equipping security teams with capabilities for systematic investigation, hypothesis generation, and evidence collection, these tools form an essential layer in modern defense strategies. Their role is not only to find active threats, but also to reduce dwell time, accelerate response, and strengthen overall security posture by uncovering previously undetected weaknesses.
Key Features of Threat Hunting Tools
Here are some of the key capabilities of threat hunting tools.
Data Collection and Aggregation
Threat hunting tools gather large volumes of relevant data from diverse sources—endpoint logs, network traffic, authentication events, user activity, and more. By consolidating this information into a centralized repository, analysts gain a unified view across their infrastructure, which is essential for uncovering subtle attack patterns and correlations that would otherwise go unnoticed.
This process often involves normalization and enrichment, transforming raw data into structured formats suitable for analysis. Without robust aggregation, security analysts would face fragmented, siloed data, hampering their ability to connect activities across the environment.
Advanced Analytics
By using statistical techniques, behavioral modeling, and increasingly machine learning, these solutions can identify anomalies that signal malicious activity. Analytics engines sift through gigabytes or even terabytes of data to surface patterns, outliers, or sequences of actions that could indicate compromise, lateral movement, or covert exfiltration.
Automation within this analytic process helps reduce human workload and shortens the time to detection. Powerful analytics not only flag potential incidents, but also allow analysts to drill down into the underlying data, formulating new hypotheses and iteratively searching for less obvious threats.
Real-Time Monitoring
Real-time monitoring provides immediate visibility into ongoing events across the network and endpoints. Effective tools offer live dashboards, alerting mechanisms, and timeline visualizations that enable security teams to track suspicious activity as it happens, rather than after the fact. This capability increases the chance of intercepting attacks during early stages before significant damage occurs.
Continuous monitoring also empowers teams to quickly validate hypotheses and respond to evolving threats. Real-time insights enable faster anomaly detection and allow organizations to adapt their defenses according to current threat landscapes.
Threat Intelligence Integration
Threat intelligence integration enhances the context and precision of threat hunting by injecting external knowledge such as indicators of compromise, known malware signatures, attacker tactics, and emerging campaigns. By aligning internal observations with global intelligence feeds, tools help analysts quickly identify relevant threats and prioritize investigation based on risk and actor sophistication.
This synergy between real-time security data and outside intelligence reduces false positives and speeds up the investigative process. Integration also supports proactive defense, enabling organizations to anticipate attacks leveraging techniques observed elsewhere.
Search, Query and Hypothesis Framework
Effective threat hunting tools provide flexible query languages or interfaces that allow investigators to form hypotheses and systematically search for evidence across datasets. For example, analysts can query for unusual logins, rare process executions, or traffic to known-bad destinations, refining their searches as they uncover new leads.
The ability to pivot quickly between different data types and views fosters an iterative approach to hunting. Strong frameworks support the documentation of hypotheses, results, and workflows, which enhances knowledge sharing and operational efficiency.
Learn more in our detailed guide to threat hunting framework (coming soon).

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

Types of Threat Hunting Tools
Threat hunting teams use a stack of security technologies to carry out their operations. Here are some common components of that stack.
1. Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) tools focus on monitoring and responding to threats on individual devices such as desktops, laptops, and servers. EDR platforms collect detailed telemetry on processes, file changes, network connections, registry modifications, and user behaviors. Analysts use this data to identify and investigate malicious activity that may have evaded preventative controls.
EDR tools often support forensic analysis and automated response actions, such as isolating compromised endpoints or terminating malicious processes. Their granular view of system events makes EDR essential for uncovering sophisticated malware, fileless attacks, or insider threats.
2. Network Monitoring Tools
Network monitoring tools provide visibility into traffic flows, packet content, and communication patterns across an organization’s infrastructure. Solutions in this category, such as intrusion detection systems and network forensic platforms, enable security analysts to detect suspicious activity like lateral movement, data exfiltration, or command-and-control communications. These tools are invaluable for identifying threats that bypass endpoint defenses and operate at the network level.
Effective network monitoring supports retrospective analysis—allowing hunters to review historical network events and reconstruct attack sequences. Rich network telemetry enables correlation of behaviors across different systems and can help track advanced adversaries as they attempt to evade detection.
3. Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) tools aggregate and correlate logs, events, and alerts from across the IT environment. They serve as the central nervous system for most security operations centers, providing a platform for data aggregation, complex event queries, rule creation, and workflow automation. SIEMs facilitate the search for threat indicators, pattern recognition, and the mapping of attack timelines.
Analytics, visualization, and incident response features in SIEMs enhance threat hunting efforts by quickly surfacing relevant data for investigation. Leading SIEM solutions now incorporate behavioral analytics, threat intelligence, and machine learning to better identify stealthy threats.
4. External Attack Surface Management (EASM)
External Attack Surface Management (EASM) is a proactive cybersecurity discipline focused on continuously discovering, monitoring, analyzing, and securing all internet-facing assets—websites, domains, APIs, cloud services, servers, IP ranges, IoT devices, third-party integrations, and even forgotten test environments—that constitute a business’s external exposure.
EASM operates from the outside-in, mimicking an attacker’s reconnaissance to uncover unknown, unmanaged, or vulnerable assets that traditional internal inventories and perimeter defenses miss. Using automated scanning, threat intelligence, and continuous monitoring, EASM tools detect misconfigurations, expired certificates, shadow IT, exposed APIs, and other weak points externally visible to adversaries.
Notable Threat Hunting Tools
1. CyCognito
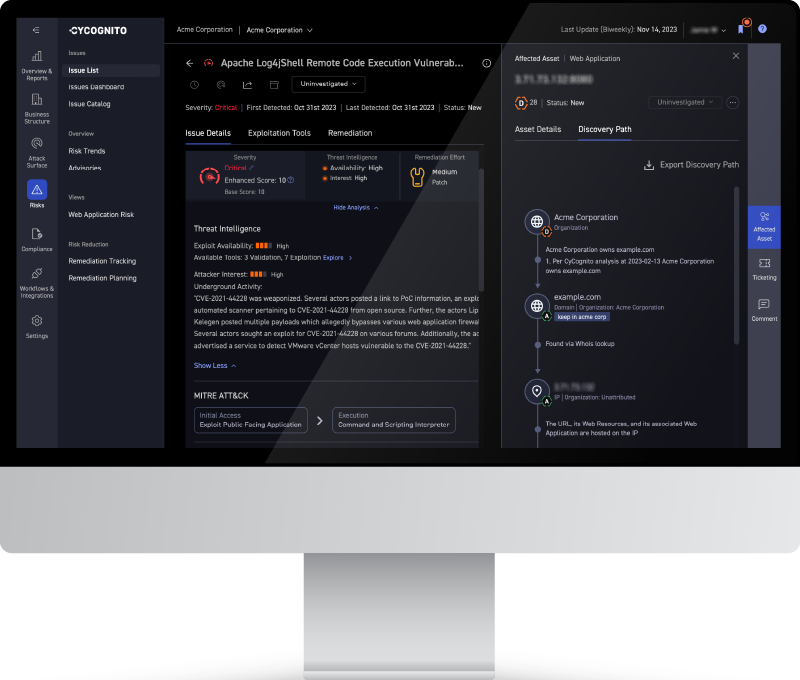
CyCognito is an Attack Surface Management (ASM) platform designed to uncover and manage risks across an organization’s internet-exposed assets. Leveraging automated reconnaissance and intelligence-driven analysis, CyCognito enables security teams to identify unknown, unmanaged, and vulnerable systems before attackers do.
Key features include:
- Automated asset discovery: Continuously maps all externally exposed assets—including shadow IT, cloud resources, web apps, APIs, inherited infrastructure, and third-party services—without requiring internal access or seed data.
- Risk-based prioritization: Applies business context and attacker logic to prioritize exploitable vulnerabilities based on potential impact and likelihood of compromise.
- Security testing at scale: Performs active, non-intrusive testing to detect misconfigurations, weak encryption, exposed services, and other high-risk conditions across the external attack surface.
- Actionable reporting: Provides detailed evidence and remediation guidance to reduce mean time to remediation (MTTR) and support compliance efforts.
CyCognito is distinct for its outside-in approach, making it a powerful complement to internal detection tools. By offering holistic visibility into areas commonly missed by perimeter-based defenses, it is especially valuable for threat hunters aiming to eliminate blind spots and stay ahead of adversarial reconnaissance.
2. Splunk Enterprise Security
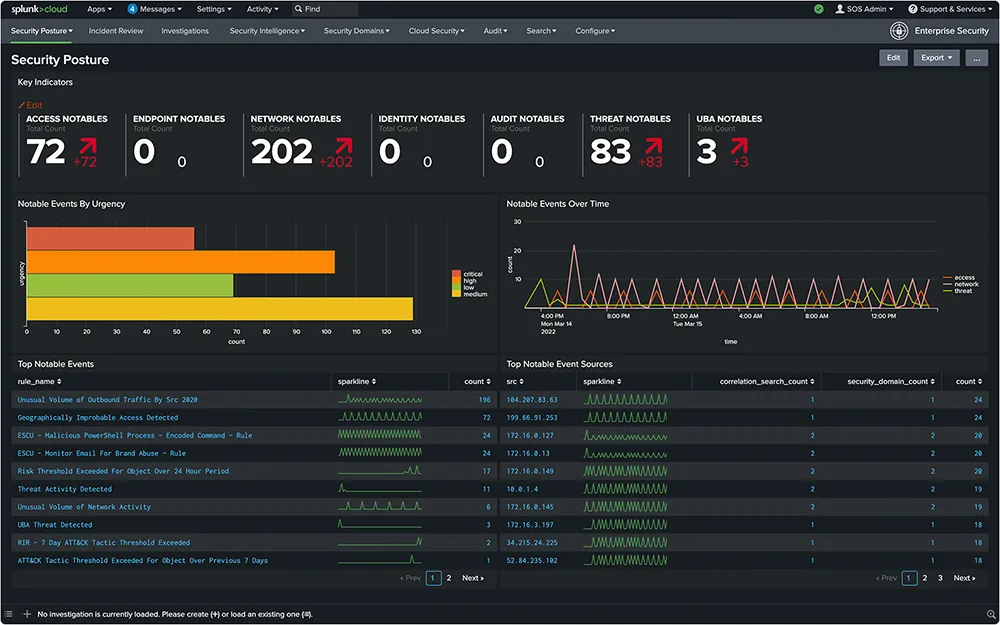
Splunk Enterprise Security (ES) is a SIEM solution that provides threat visibility and detection for security operations centers. Built on a scalable data platform, it enables organizations to ingest and analyze security-relevant data from various sources.
Key features include:
- Data visibility: Ingests, normalizes, and analyzes data from different environments.
- Risk-based alerting: Prioritizes threats with contextual risk scoring to reduce alert fatigue.
- Threat intelligence enrichment: Improves detections with access to Cisco Talos and other intelligence feeds.
- Federated search & analytics: Allows queries across distributed data sources.
- SOAR integration: Integrates natively with Splunk SOAR for automated response, improving mean time to detect and respond.
3. CrowdStrike Falcon Overwatch
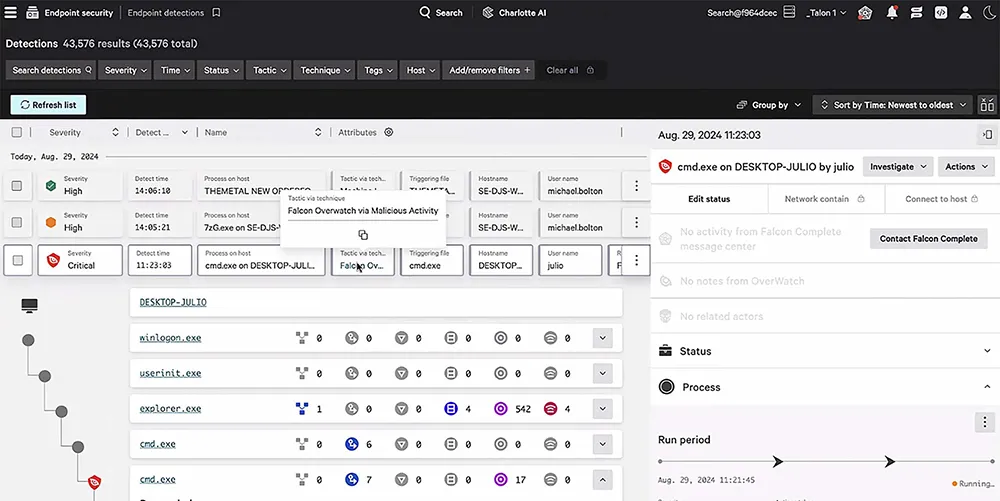
CrowdStrike Falcon OverWatch is a managed threat hunting service that provides protection across endpoints, identities, cloud environments, and SIEM data. Operating within the CrowdStrike Falcon platform, it combines human analysis with AI and threat intelligence to detect adversary activity and prevent breaches.
Key features include:
- All-domain threat hunting: Provides proactive hunting across endpoint, identity, and cloud data.
- Expert-led investigations: Uses a team of threat hunters, supported by AI, to uncover and stop attacks.
- Integrated threat intelligence: Delivers context-based indicators of compromise and adversary profiling within the Falcon platform.
- Endpoint threat coverage: Tracks attacker activity on endpoints, using behavioral analytics and threat intelligence to identify and respond to threats.
- Identity-based threat detection: Identifies and disrupts credential theft, lateral movement, and privilege escalation by monitoring identity-based attacks and triggering security controls like MFA.
4. APT-Hunter
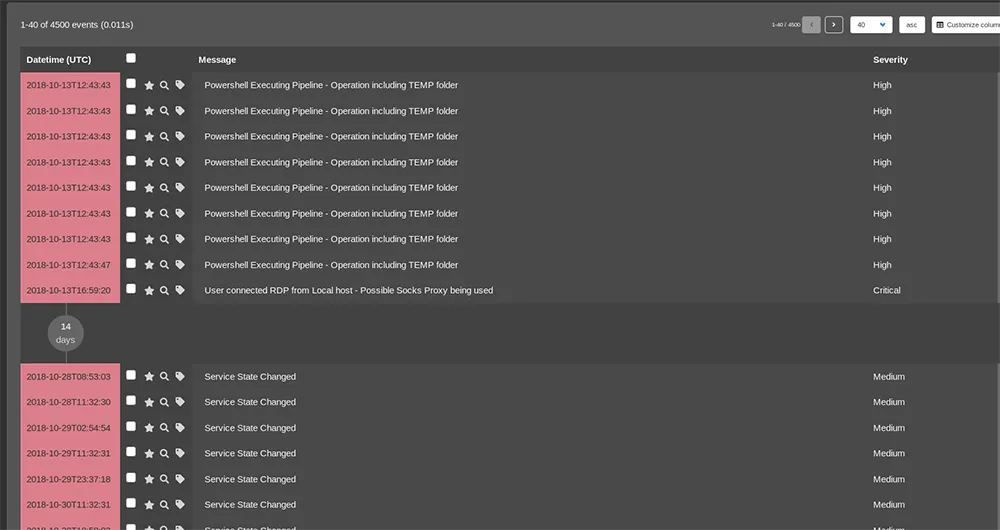
APT-Hunter is an open-source threat hunting tool to analyze Windows event logs for signs of advanced persistent threats (APTs). Developed with a purple team mindset, it focuses on detecting abnormal patterns and attacker behaviors that may be missed in routine analysis.
Key features include:
- Event log analysis: Specializes in parsing and analyzing Windows event logs to identify attacker movements across systems.
- Predefined detection rules: Uses a library of rules to identify known attack patterns and suspicious behaviors.
- Statistical anomaly detection: Applies statistical techniques to detect deviations from normal system behavior.
- Multi-format output: Generates results in multiple formats (Excel, CSV, Timeline Explorer).
- Customizable hunting: Supports string-based, regex-based, and file-based hunting.
5. Zeek
Zeek is an open-source, passive network traffic analyzer used for network security monitoring (NSM) and protocol inspection. It operates by observing live network traffic and generating high-fidelity logs that document network activity in a policy-neutral, structured format.
Key features include:
- Log generation: Automatically creates logs of network connections, application-layer protocols (HTTP, DNS, SSL, SMTP, etc.), and file transfers.
- Analysis capabilities: Ships with default scripts for detecting brute-force attacks, malware behavior, vulnerable software, and SSL issues.
- Scripting language for custom detection: Provides a domain-specific, Turing-complete scripting language for writing custom event handlers.
- File extraction: Extracts files from network streams (e.g., HTTP, FTP) for external sandboxing or malware analysis.
- Cluster support: Enables high-volume traffic processing using Zeek clusters, where traffic is load-balanced across multiple nodes and coordinated by ZeekControl.
6. TheHive
TheHive is an open-source, enterprise-grade incident response and case management platform to help security teams investigate, manage, and respond to threats. Developed by StrangeBee, it assists SOCs, CERTs, and CSIRTs by consolidating alerts, observables, threat intelligence, and response workflows.
Key features include:
- Centralized alert ingestion: Automatically collects and consolidates alerts from connected security tools.
- Customizable case management: Allows creation of case records with structured templates, attachments, metrics, and custom fields.
- Collaborative workflow: Supports realcollaboration across multiple teams or organizations with role-based access control, task assignment, and live dashboards.
- Integrated threat intelligence: Imports indicators from MISP, maps alerts to MITRE ATT&CK tactics and techniques, and highlights known observables.
- Cortex integration for automation: Automates the analysis of observables using over 200 analyzers and responders.
7. osquery
osquery is an open-source operating system instrumentation framework that transforms system data into a relational database format, enabling monitoring and investigation using standard SQL. Designed for Windows, macOS, and Linux, it allows security and operations teams to query low-level OS information across diverse environments.
Key features include:
- SQL-based data access: Exposes system internals like running processes, user accounts, network activity, kernel modules, and file hashes as relational tables.
- Cross-platform coverage: Works uniformly across Windows, macOS, and Linux.
- osqueryd for scheduled monitoring: A lightweight daemon that runs scheduled queries across endpoints, captures state changes, and logs them for downstream analysis.
- osqueryi for interactive investigation: An interactive console for ad-hoc queries and exploration.
- Custom plugin architecture: Offers a modular design with hot-swappable components and plugin support.
8. Cuckoo Sandbox
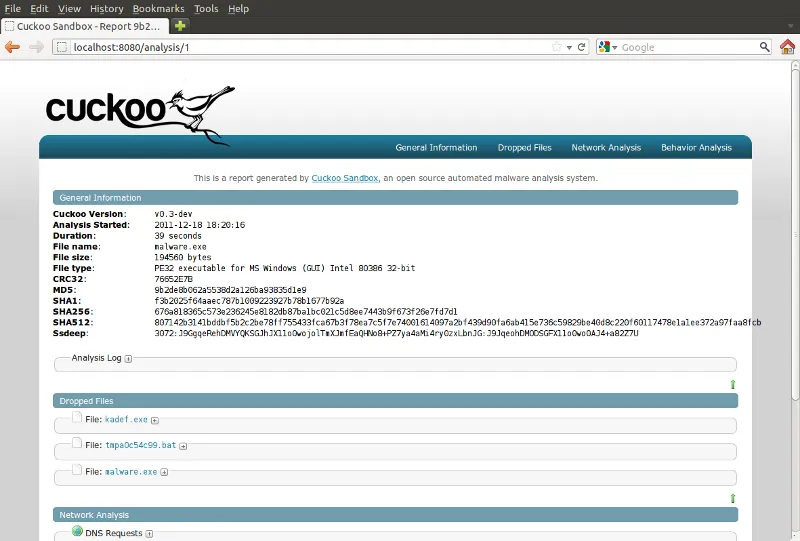
Cuckoo Sandbox is an open-source automated malware analysis system that allows security teams to execute and observe suspicious files or URLs in an isolated environment. It simulates a host environment using a virtualized Windows system to deceive malware into executing as if it were on a live victim machine.
Key features include:
- Automated malware analysis: Runs executables, documents, scripts, emails, and URLs in a controlled virtual machine to observe malicious behavior.
- Behavioral reporting: Captures system-level activities including file writes, registry modifications, API calls, dropped files, and network communications.
- Virtualized testbed: Uses a Linux host (typically Ubuntu) with VirtualBox or other supported hypervisors (KVM, VMware, XenServer) to manage an instrumented Windows guest environment.
- Multi-interface support: Offers command-line tools and a web-based dashboard for submitting samples, viewing analysis results, and monitoring system status.
- Modular and extensible: Supports integration with third-party tools and features a plugin-based architecture that allows customization of analyzers, reporting formats, and automation workflows.
Conclusion
Threat hunting tools play a critical role in enabling security teams to proactively detect and investigate advanced threats that often go unnoticed by traditional defenses. By combining capabilities like real-time monitoring, behavioral analytics, and threat intelligence integration, these tools empower analysts to uncover hidden attacker activities and reduce dwell time.














