What Is AWS Vulnerability Scanning?
AWS vulnerability scanning identifies security weaknesses within cloud resources hosted on Amazon Web Services (AWS). This process uses automated tools to test AWS environments for vulnerabilities that may compromise the integrity, confidentiality, or availability of the services.
By scanning for vulnerabilities, organizations can manage their security posture, ensuring they are aware of and can address potential threats before they are exploited by malicious actors. Continuous monitoring is key to vulnerability management within AWS.
Since cloud environments can change rapidly due to factors such as scaling, new deployments, and configuration updates, regular scanning helps maintain a secure posture. AWS provides various native tools and integrates with third-party solutions to enable these scans, enabling organizations to achieve a defense against vulnerabilities.
This is part of a series of articles about vulnerability assessment.
The AWS Shared Responsibility ModelExplained
The AWS shared responsibility model defines the security obligations between AWS and its customers. AWS is responsible for securing the infrastructure that runs all of the services offered in the AWS cloud. This includes hardware, software, networking, and facilities that run AWS services.
Customers are responsible for management of guest operating systems, application software, and associated configurations and controls, such as identity and access management. This clear division ensures both AWS and its customers understand their roles in maintaining a secure environment.
The RACI matrix (Responsible, Accountable, Consulted, Informed) can help clarify roles within the shared responsibility model. By explicitly mapping roles, the RACI model reduces ambiguity and improves coordination in managing cloud vulnerabilities. For example:
- AWS is Responsible for securing the physical infrastructure and Accountable for the underlying services’ security.
- The customer is Responsible for securing data, configurations, and access controls, and Accountable for compliance with organizational policies.
- Security teams may be Consulted on best practices.
- Auditors or stakeholders are often Informed of the overall security posture.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

AWS Native Tools for Vulnerability Management
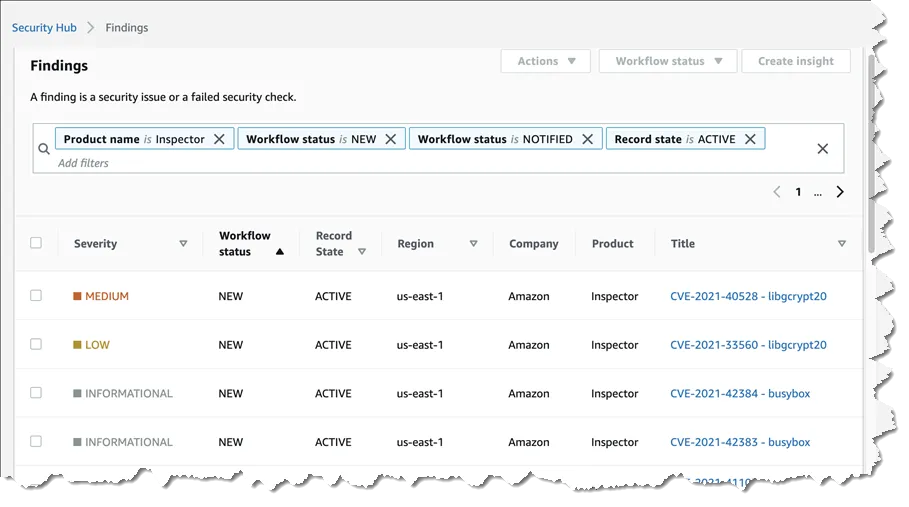
Amazon Inspector
Amazon Inspector is an automated security assessment service that helps detect vulnerabilities in applications deployed on AWS. It evaluates applications for deviations from security best practices and identifies vulnerabilities using an extensive rule engine. These assessments can uncover a range of issues, such as unpatched software, insecure network configurations, and permissions problems, providing detailed findings to help resolve security gaps.
Using Amazon Inspector, customers can configure assessment targets and conduct regular security assessments. The service provides informative reports that prioritize vulnerabilities based on severity, aiding in efficient remediation efforts. The automation of vulnerability detection also reduces the need for manual checks.
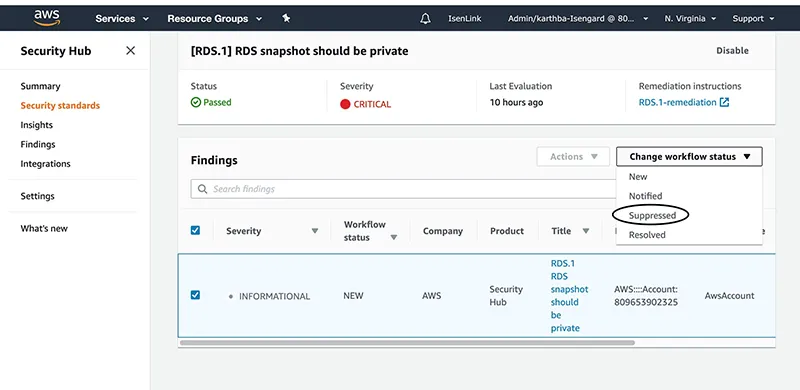
AWS Security Hub
AWS Security Hub provides organizations with a view of their security state within AWS. It aggregates security findings from multiple AWS services and partner tools into a centralized dashboard, enabling users to manage and prioritize vulnerabilities across their AWS environments.
Security Hub automates the evaluation of security standards and best practices using built-in security benchmarks, providing continuous compliance checks. It enables users to quickly identify and address high-priority threats, offering detailed views of each finding.
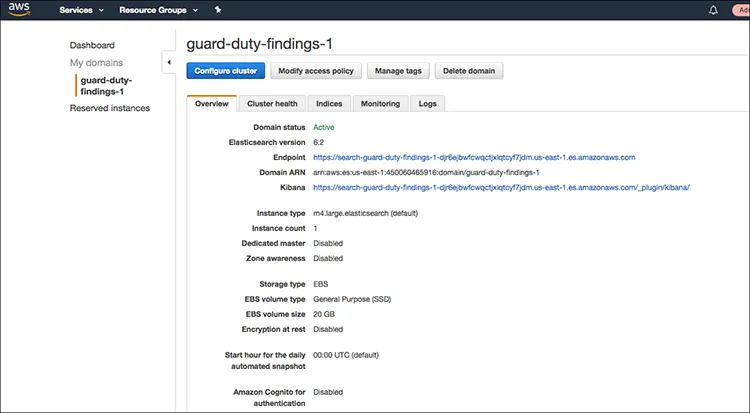
Amazon GuardDuty
Amazon GuardDuty is a threat detection service that continuously monitors AWS accounts and workloads for malicious activity. It uses machine learning, anomaly detection, and integrated threat intelligence to identify potential threats, such as compromised instances or suspicious account activity. As a managed service, GuardDuty requires no infrastructure, simplifying the setup and operation for users.
GuardDuty provides alerts and detailed findings for identified threats, allowing organizations to take immediate action. The service integrates with other AWS security services, improving security monitoring.
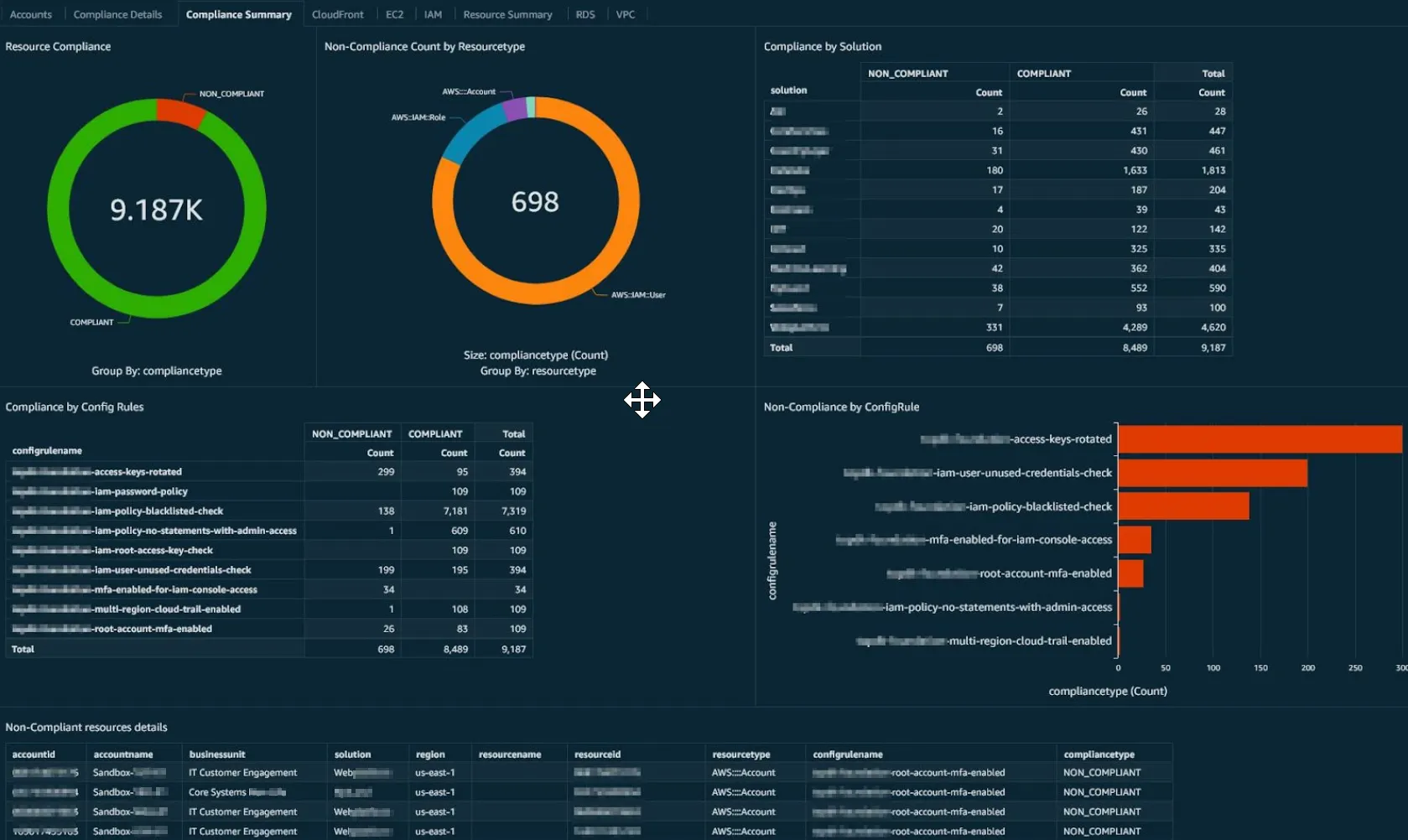
AWS Config
AWS Config enables users to assess, audit, and evaluate the configurations of AWS resources. It tracks configuration changes over time, providing a view of the resource landscape and its changes. This allows organizations to enforce security and compliance requirements by assessing compliance with configuration policies and identifying resources that deviate from acceptable configurations.
With AWS Config, users can automate the continuous monitoring of configurations and receive alerts for non-compliant changes. Config allows for auditing and examination of historical configurations, enabling the identification and remediation of misconfigurations that could lead to vulnerabilities.
Tips from the Expert

Rob Gurzeev, CEO and Co-Founder of CyCognito, has led the development of offensive security solutions for both the private sector and intelligence agencies.
In my experience, here are tips that can help you optimize AWS vulnerability scanning:
- Use AWS Organizations for centralized security management: If you manage multiple AWS accounts, consolidate vulnerability scanning across all accounts using AWS Organizations. This enables centralized monitoring through AWS Security Hub and Amazon Inspector, ensuring no environment is left unscanned.
- Monitor ephemeral resources like Lambda, ECS, and auto-scaling EC2 instances: Traditional vulnerability scans often miss short-lived cloud resources. Use event-driven security (AWS Lambda + CloudWatch) to trigger scans when instances or containers are launched. This prevents vulnerabilities from slipping through due to short lifespans.
- Detect and remediate overprivileged IAM roles automatically: Overly permissive IAM roles pose a major security risk. Use IAM Access Analyzer and AWS Config rules to detect excessive permissions and automate role adjustments. Implement least privilege principles to reduce attack surfaces.
- Scan AWS Systems Manager (SSM) patch compliance reports for hidden risks: AWS SSM Patch Manager provides insights into unpatched software on EC2 instances. Integrate these reports into the vulnerability scanning pipeline to identify missing security updates and automate remediation using Systems Manager Run Command.
- Harden S3 buckets against misconfigurations that scanners may miss: Many vulnerability scanners focus on network and compute resources but overlook storage. Use tools like AWS Macie to detect sensitive data exposure and enforce least-privilege policies to prevent accidental public S3 bucket access.
Considerations for Choosing Third-Party AWS Vulnerability Scanners
Many organizations find that native AWS tools are not enough for their security needs. Here are some considerations for selecting a third-party vulnerability scanning tool for your AWS environment.
1. AWS Integration
When choosing an AWS vulnerability scanner, integration with AWS services is essential for security management. A well-integrated scanner can leverage AWS-native security features, such as AWS Security Hub, Amazon Inspector, AWS IAM policies, and AWS Config, to improve vulnerability detection, reporting, and remediation.
Look for solutions that support AWS APIs and CloudFormation templates, allowing for automated deployments and scans that fit within existing AWS infrastructure. The scanner should also be able to assume IAM roles with the necessary permissions to access and analyze AWS resources without excessive privileges, reducing security risks.
Additionally, integration with AWS Organizations is useful for enterprises managing multiple AWS accounts. A scanner that supports multi-account scanning can provide centralized security insights, improving visibility and compliance tracking across the entire AWS environment. Event-driven security monitoring using services like AWS Lambda automate security responses, triggering remediation actions when vulnerabilities are detected.
2. Coverage Scope
A vulnerability scanner should assess a range of AWS resources to provide security coverage. The scanner should be able to scan all relevant resources running in the target AWS environment, such as:
- Compute resources: EC2 instances, Lambda functions, and containerized workloads (ECS, EKS, Fargate).
- Storage resources: S3 buckets, EBS volumes, and RDS databases.
- Networking components: VPC configurations, security groups, and firewall rules.
- IAM and access controls: Permissions, policies, and access logs.
A good scanner should be able to identify misconfigurations, unpatched software and exposed credentials in compute resources, permission issues and data protection features in storage resources, network security risks such as open ports or improperly configured security groups, and identity risks such as overly permissive IAM policies.
Additionally, compliance with industry standards such as CIS benchmarks, NIST, PCI-DSS, and SOC 2 is a critical aspect of coverage. The scanner should be capable of running compliance checks against these frameworks. For organizations running hybrid or multi-cloud environments, the scanner should support scanning on-premises infrastructure and other cloud providers alongside AWS.
3. Accuracy and Reporting
One of the biggest challenges in vulnerability scanning is minimizing false positives while ensuring that real threats are detected. A high-quality AWS vulnerability scanner should have:
- Detection algorithms that differentiate between real vulnerabilities and benign configurations.
- Context-aware scanning to assess risk based on the specific AWS environment, rather than providing generic results.
- Machine learning and threat intelligence integration to improve accuracy and detect emerging threats.
Reporting capabilities are just as important as detection. A scanner should offer:
- Clear, detailed vulnerability assessments explaining the issue, affected resources, and potential impact.
- Prioritization based on severity (e.g., CVSS scores, exploitability, and business impact).
- Actionable remediation recommendations that guide security teams on how to fix detected vulnerabilities.
Look for scanners that support interactive dashboards, exportable reports (PDF, CSV, JSON), and integration with ticketing systems (Jira, ServiceNow) to simplify vulnerability management.
4. Automation and Continuous Monitoring
Given the dynamic nature of AWS environments, where resources are frequently created, modified, and terminated, traditional one-time scans are insufficient. The AWS vulnerability scanner should support:
- Scheduled scans to ensure continuous security assessments.
- Real-time threat detection that scans resources as soon as they are deployed.
- Event-driven security checks using AWS Lambda, AWS Config, or CloudWatch events to trigger vulnerability scans upon resource changes.
Automation helps organizations maintain a proactive security posture, reducing the window of exposure to vulnerabilities. Additionally, self-healing capabilities—such as triggering remediation workflows using AWS Systems Manager or Lambda—can automatically resolve common misconfigurations, reducing the burden on security teams.
5. Integration with DevOps Workflows
Security should be embedded into the development lifecycle to catch vulnerabilities early and prevent security issues from reaching production. A strong AWS vulnerability scanner should integrate with DevOps and CI/CD pipelines. This enables shift-left security, where vulnerabilities are detected and remediated before deployment.
Key features to look for include:
- Pre-deployment scanning: Scan infrastructure-as-code (IaC) templates (Terraform, CloudFormation) for misconfigurations before provisioning resources.
- Automated security testing: Run vulnerability scans on container images, application dependencies, and cloud configurations as part of CI/CD pipelines.
- Fail conditions and gating: Block deployments if critical vulnerabilities are detected, preventing insecure code from going live.
Vulnerability Management with CyCognito Attack Surface Management
The CyCognito platform addresses today’s vulnerability management requirements, built on the foundation of full discovery of your entire extended IT ecosystem, to help you proactively defend against threats from even the most sophisticated attackers. It operates continuously and autonomously using advanced attacker-reconnaissance techniques to identify attackers’ paths of least resistance into your environment so that you can efficiently eliminate them.
Once it identifies potential attack vectors, it prioritizes risks and delivers both actionable remediation guidance and ongoing validation of fixes. The result is a platform that delivers risk-based vulnerability management for your entire attacker-exposed IT ecosystem, closing what is a significant gap in existing attack surface management and vulnerability management processes.
The CyCognito platform uniquely delivers:
- Full discovery of your extended IT ecosystem, including assets that are part of your IT ecosystem, but are unknown or unmanaged by you.
- Sophisticated discovery capabilities that go beyond typical attack surface management or VM tools, which rely on passive data collection within known IP ranges.
- Detection and testing of attack vectors across your entire attacker-exposed IT ecosystem, going well beyond CVEs to include data exposures, misconfigurations and even software zero-day vulnerabilities.
- Prioritization of the attack vectors in your IT ecosystem based on what could impact your organization most from a cybersecurity risk perspective.
- Actionable remediation guidance and reporting to accelerate your remediation and validation.














