What Are Vulnerability Scanning Tools?
Vulnerability scanning tools are software applications designed to assess computers, networks, or applications for vulnerabilities and other security weaknesses. These tools automate the process of identifying, quantifying, and prioritizing (or ranking) weaknesses in a system, which can range from software bugs, misconfigurations, outdated software versions, to weak passwords and encryption methods.
By systematically scanning for these weaknesses, vulnerability scanning tools help organizations understand their exposure to potential security threats and provide a pathway to remediate identified issues, thereby enhancing the security posture.
Vulnerability scanning tools are important because they promote proactive security measures. Through regular scans, organizations can keep abreast of new and emerging threats, patch vulnerabilities before they are exploited, and ensure compliance with regulatory requirements. The dynamic nature of IT environments, with continuous software updates, new deployments, and changing configurations, necessitates an ongoing, systematic approach to vulnerability management.
This is part of a series of articles about vulnerability assessment.
Vulnerability Scanning vs. Dynamic Vulnerability Testing
Vulnerability scanning is an automated process that identifies and reports on known vulnerabilities within a network or application. It relies on a database of known vulnerabilities and checks systems against this database to find matches. This approach is broad and general, designed to catch a wide range of potential issues based on known vulnerabilities.
Dynamic vulnerability testing is a more interactive process, often conducted by dynamic application security testing (DAST) systems. Dynamic testing involves executing real-world attacks against live systems or applications to identify vulnerabilities that could be exploited. Unlike the passive nature of vulnerability scans, dynamic testing actively simulates an attacker’s actions to discover vulnerabilities that require specific conditions to be exploitable.
Thus, dynamic vulnerability scanning complements vulnerability scanning by identifying issues that only appear during the execution of an application. Advanced vulnerability scanning solutions are introducing dynamic testing capabilities, allowing them to identify a broader range of security weaknesses.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

Key Features of Vulnerability Scanning Tools
Comprehensive Vulnerability Database
A core feature of effective vulnerability scanning tools is their reliance on a vulnerability database. This database contains information about known security vulnerabilities, including their severity, impact, and the conditions under which they can be exploited.
The quality and breadth of this database significantly influence the scanner’s ability to detect risks. Regular updates are crucial, as they ensure the tool remains effective against emerging threats and keeps pace with the latest security research and disclosures.
The depth of the database affects the tool’s utility across different environments. It should cover a wide range of software, operating systems, and devices, enabling it to identify vulnerabilities in a diverse IT ecosystem.
Customizable Scan Profiles
Customizable scan profiles allow users to tailor the scanning process to their specific needs. This flexibility enables organizations to focus on areas of particular concern or compliance requirements, and adapt scans to specific application requirements.
Users can define what to scan, how deep the scan should go, and the types of vulnerabilities to prioritize. This customization helps minimize disruptions to operational systems and reduces false positives, making the scanning process more efficient and less intrusive.
Detailed Reporting and Analytics
After scanning, the tool provides detailed reports and analytics, offering insights into the vulnerabilities found. These reports are essential for understanding the risk landscape, prioritizing remediation efforts, and tracking progress over time. They typically include metrics on vulnerability severity, affected systems, and recommended actions to mitigate risks.
Furthermore, advanced tools offer analytics capabilities to identify trends and patterns in the data, enabling organizations to anticipate potential security issues before they become critical. This proactive approach can significantly reduce the risk of breaches.
Credential and Non-Credentialed Scans
Credential and non-credentialed scans represent two approaches to vulnerability scanning:
- Credential scans require login information, allowing the tool to perform its examination by accessing systems as a legitimate user. This approach can uncover vulnerabilities that would not be visible externally, providing a deeper insight into the security posture of the scanned systems.
- Non-credentialed scans do not use login credentials and assess systems from an outsider’s perspective. This method is useful for identifying vulnerabilities that could be exploited by an attacker without internal access.
Tips from the Expert

Rob Gurzeev, CEO and Co-Founder of CyCognito, has led the development of offensive security solutions for both the private sector and intelligence agencies.
In my experience, here are tips that can help you better leverage vulnerability scanning tools:
- Automate remediation workflows: Use automated workflows that trigger specific actions based on the severity of vulnerabilities detected. This can include auto-generating tickets in your ITSM system, pushing patches, or isolating affected systems to reduce the time from detection to mitigation.
- Leverage scan frequency optimization: Don’t stick to a single scan frequency. Adapt the scanning frequency based on asset criticality, exposure, and historical vulnerability trends. For instance, critical public-facing assets should be scanned more frequently than internal systems with lower exposure.
- Correlate with configuration management databases (CMDB): Integrate vulnerability scanning tools with your CMDB to ensure all assets are accounted for in scans. This integration helps prevent the “shadow IT” problem, where unregistered or unknown assets escape regular vulnerability assessments.
- Implement differential scanning: Use differential scanning techniques that focus on changes since the last scan. This reduces scan time and resource consumption, while ensuring new vulnerabilities introduced by recent changes are quickly identified.
- Utilize post-scan risk assessments: After vulnerability scans, perform a comprehensive risk assessment that considers factors beyond CVSS scores, such as business impact, exploitability in the context of your specific environment, and compensating controls already in place. This will guide more effective prioritization of remediation efforts.
Commercial Vulnerability Scanning Tools
1. CyCognito
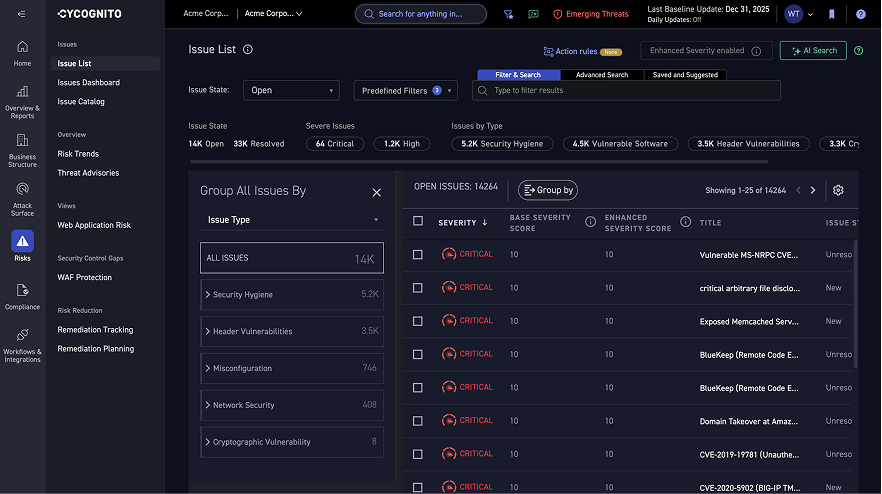
The CyCognito platform addresses today’s vulnerability management requirements by taking an automated multi-faceted approach to identifying and remediating critical issues based on their business impact rather than focusing on the generic severity of the threat alone. To do this you need a platform that is continuously monitoring the attack surface for changes and provides intelligent prioritization that incorporates the organization’s context.
The CyCognito platform addresses today’s vulnerability management requirements by:
- Maintaining a dynamic asset inventory with classification of the entire external attack surface, including exposed on-premise and cloud-hosted assets like web applications, IP addresses, domains and certificates, eliminating the need to rely on outdated or incomplete information from collaboration tools, spreadsheets, or emails. This approach significantly reduces the burden of tedious, error-prone and costly processes.
- Actively testing all discovered assets to identify risk. Active testing, including dynamic application security testing, or DAST, uncovers complex issues and validates known issues, with low false positives. Each exploited asset is assigned a security grade based on its criticality to the business.
- Prioritizing critical issues, guiding security teams to focus on the most urgent threats. Our unique risk-based prioritization analysis goes beyond the common vulnerability scoring system (CVSS), and incorporates factors like asset discoverability, asset attractiveness, exploitability, business impact and remediation complexity. Integrated tactical threat intelligence identifies the handful of attack vectors that pose the greatest risk.
- Streamlining communications between remediation teams by providing comprehensive, verifiable evidence for each exploited asset. This evidence includes detailed risk assessments, asset ownership information, and actionable remediation guidance. The platform seamlessly integrates with SIEM, SOAR and ticketing system tools like Jira, ServiceNow and Splunk to facilitate information sharing and collaboration.
Learn more about CyCognito automated vulnerability testing.
2. Tenable
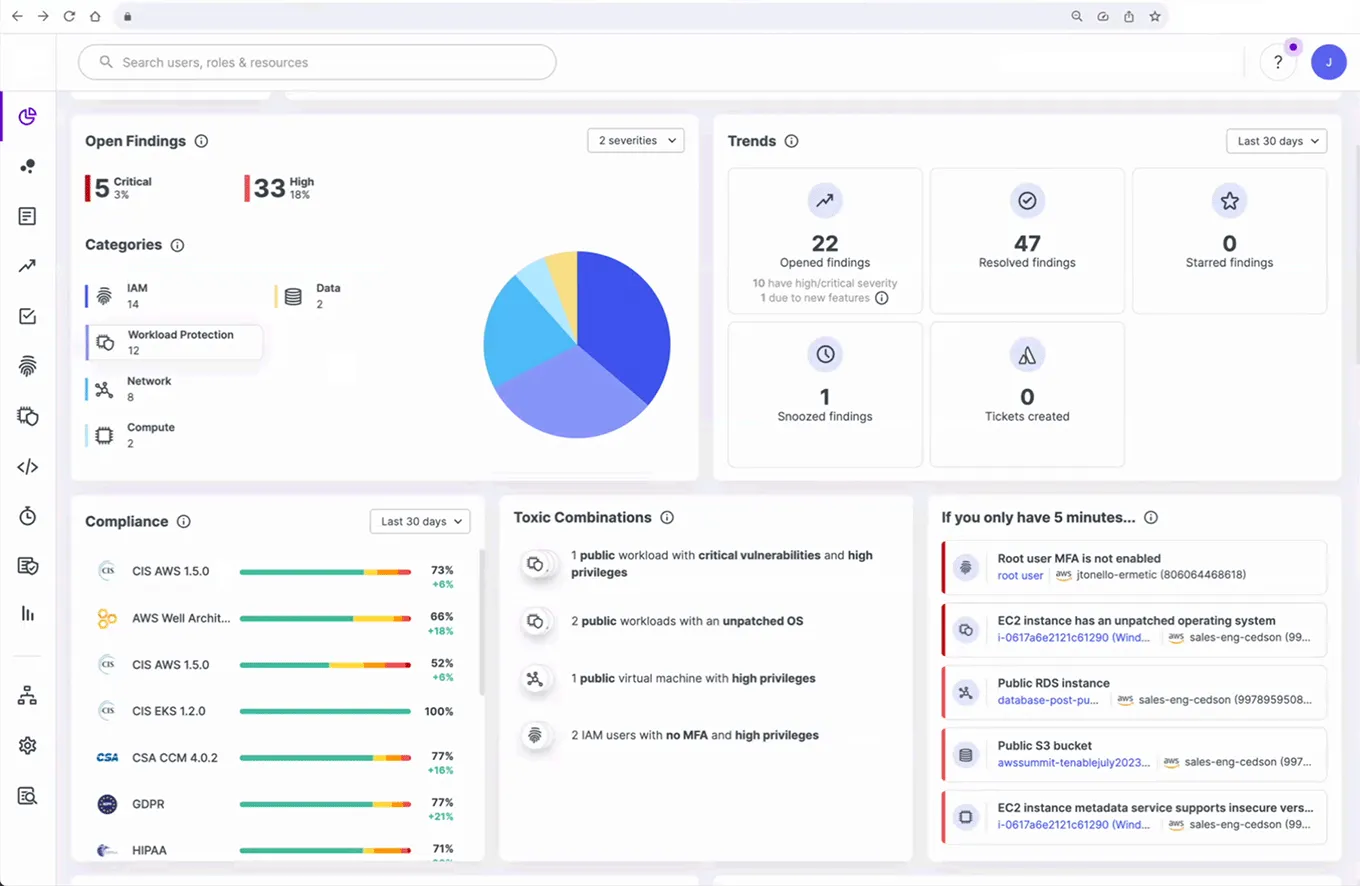
Tenable provides visibility into on-premises and cloud-based assets. The solution includes the Nessus scanner, which performs deep inspection of networks to uncover vulnerabilities. It also offers dynamic testing features through its Web Application Scanning tool, which allows for the automated discovery and testing of web application vulnerabilities in a real-world context.
Tenable provides a predictive prioritization feature, which uses machine learning to analyze vulnerabilities and predict which are most likely to be exploited in the near term. This capability enables organizations to focus their remediation efforts where they will have the most significant impact.
3. Qualys
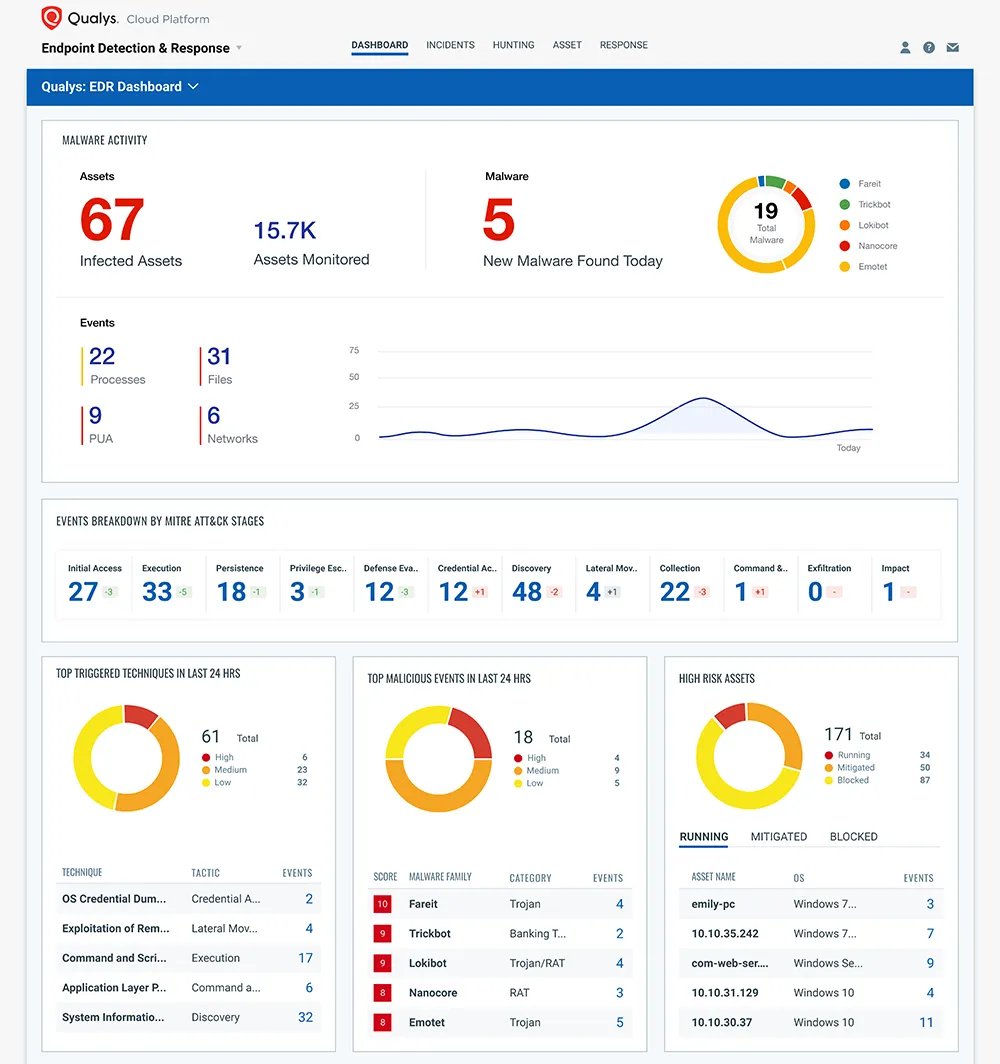
Qualys is a cloud-based vulnerability scanning and management platform. Its vulnerability management service, Qualys VM, provides scalable, in-depth analysis of vulnerabilities across all IT assets. Qualys complements scanning capabilities with dynamic application security testing (DAST) features, enabling real-time scanning and testing of web applications to identify vulnerabilities like SQL injection and cross-site scripting.
Qualys provides a continuous monitoring service, which alerts users to new vulnerabilities and changes in their IT environment as they happen, allowing them to respond quickly to emerging threats. It offers a large vulnerability knowledge base and integrated solutions for web application security, compliance, and threat protection.
4. Rapid7
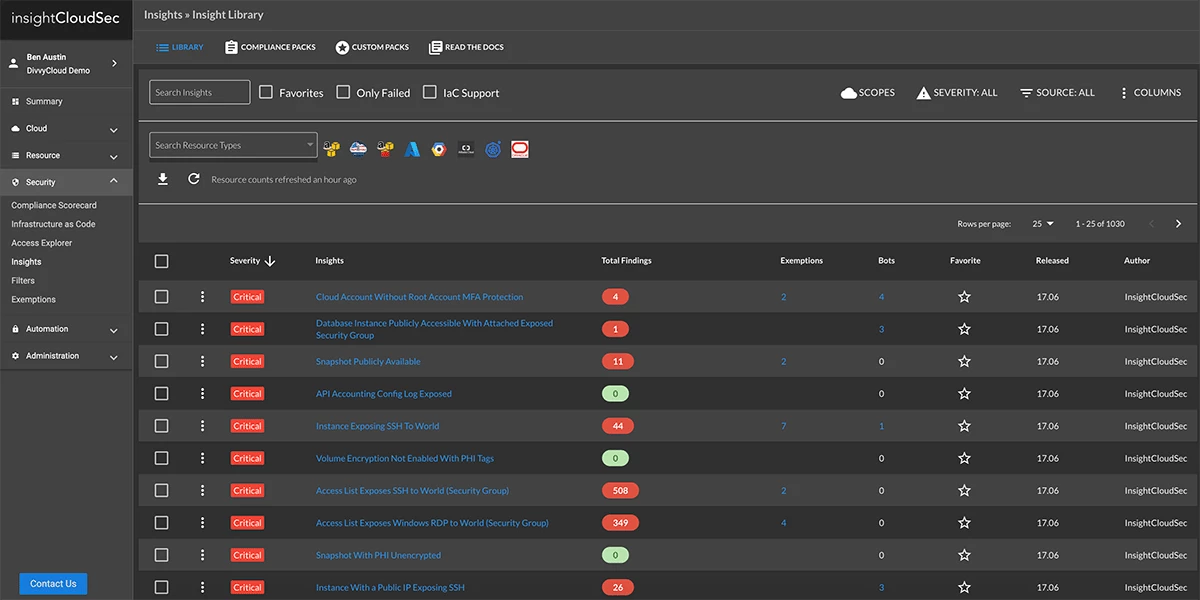
Rapid7’s InsightVM is a vulnerability management solution that stands out for its live monitoring and advanced analytics capabilities. InsightVM provides a view of an organization’s risk through real-time data collection and analysis, integrating with Rapid7’s Metasploit for dynamic vulnerability testing. This integration allows users to simulate attacks on their network, identifying vulnerabilities that could be exploited in an attack.
Rapid7 provides actionable insights that enable teams to collaborate on remediation efforts. In addition to traditional scanning, it provides threat feeds, cloud and virtual infrastructure monitoring, and container security, providing a view of vulnerabilities across environments.
5. Acunetix by Invicti
Acunetic, now owned by Invicti, offers an automated vulnerability scanner for web applications and websites. Its technology is designed to significantly reduce false positives, a common challenge in web application security. Invicti/Acunetix also incorporates dynamic testing features to simulate real-world attacks on web applications, identifying vulnerabilities such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 risks.
The platform stands out for its ability to scan complex, authenticated web applications and SPA frameworks, offering detailed insights into the security of modern web applications. With features like continuous monitoring, integrated issue tracking, and comprehensive reporting, Acunetix helps organizations secure their web applications efficiently, reducing the risk of data breaches and enhancing their overall security posture.
6. Burp Suite
Burp Suite by PortSwigger is a solution for web application security testing, typically used by security professionals and penetration testers. It provides a range of automated and manual testing tools, from an intercepting proxy to advanced scanning and exploitation capabilities. Burp Suite’s dynamic vulnerability testing capabilities allow users to actively probe applications for vulnerabilities.
Burp Suite enables detailed analysis and manipulation of web application traffic, alongside automated scanning for vulnerabilities. Its customizable nature allows users to tailor the tool to their specific testing needs, making it possible to uncover complex and nuanced security weaknesses. The tool also provides a free community edition.
7. Frontline VM
Frontline VM, a product of Digital Defense, Inc., is a cloud-based vulnerability management solution. It provides advanced analytics capabilities, which simplify the process of identifying, prioritizing, and remediating vulnerabilities, even for users with limited technical expertise. A key capability of Frontline VM is its ability to provide clear, actionable guidance on vulnerabilities, and integrate with other security tools to streamline remediation workflows.
Open Source Vulnerability Scanning Tools
8. OpenVAS
OpenVAS (Open Vulnerability Assessment System) is a free and open source vulnerability scanner that evolved from a fork of the last free version of Nessus. It offers a comprehensive and continually updated database of vulnerabilities, providing detailed scans across network devices, servers, and web applications. It can scale to support scans of large and complex networks with thousands of devices.
OpenVAS is backed by a large open-source community, ensuring that the tool remains up-to-date with the latest vulnerabilities and scanning techniques. While it may require more setup and maintenance than commercial tools, it offers a powerful and cost-effective option for vulnerability management.
9. OWASP ZAP
The OWASP Zed Attack Proxy (ZAP) is an open-source web application security scanner developed by the OWASP Foundation. It is designed to help users find security vulnerabilities in their web applications during the development and testing phases. ZAP provides automated scanners as well as a set of tools for manual penetration testing. With its dynamic vulnerability testing features, ZAP can identify a wide range of vulnerabilities in web applications, including those listed in the OWASP Top 10, making it a valuable tool for developers and security professionals alike.
ZAP’s support for automated and manual testing processes, along with its active community and integration with continuous integration/continuous delivery (CI/CD) pipelines, makes it an integral part of secure development workflows. Its ability to perform both passive and active scanning allows for comprehensive assessments of web application security, providing insights that can be used to strengthen application defenses before deployment.
10. Nmap
Nmap (Network Mapper) is a free and open-source tool for network discovery and security auditing. While primarily known for its network mapping capabilities, Nmap also includes features for vulnerability scanning.
Nmap can detect open ports, identify running services and their versions, and, with the use of NSE (Nmap Scripting Engine) scripts, perform vulnerability detection against discovered services. Nmap’s flexibility and extensibility through customizable scanning options and scripting make it a valuable tool for both initial reconnaissance and targeted vulnerability assessments.
Related content: Read our guide to vulnerability detection tools.
Conclusion
In conclusion, vulnerability scanning tools are essential for identifying, assessing, and mitigating security weaknesses in networks, applications, and systems. These tools, whether commercial or open-source, offer a range of capabilities from comprehensive vulnerability databases and customizable scanning profiles to dynamic testing and detailed reporting.
By leveraging these tools, organizations can significantly enhance their security posture, reduce their exposure to threats, and comply with regulatory requirements. Regular use of vulnerability scanning tools is a proactive step towards maintaining a robust security framework in the face of evolving cyber threats.
Learn more about CyCognito automated vulnerability testing.














